How To...
Logon to the Gateway Administrator
Gateway Administrator is a web-based tool for provisioning users and configuring Jobs and Transfer Sites. Your initial logon resets the default administrative password.
Before you begin
Install the Gateway Administrator.
To connect to the Gateway Administrator and log on
-
Connect to the Gateway Administrator console using either of the following methods:
On the server running Gateway Administrator, use the Windows Start menu. Gateway Administrator is installed under Micro Focus Reflection for Secure IT Gateway > Gateway Administrator.
-or-
From a web browser on any system with access to the Gateway Administrator server, enter the following URL replacing
with the name or IP address of the host running Gateway Administrator. https://<gateway_administrator_host>:9490Note
You will see a warning message before you see the login page. This warning shows up because the Gateway Administrator installs with a self-signed security certificate that is unknown to your browser. For initial testing purposes, you can ignore this warning and proceed with the connection (Edge or Chrome) or add an exception (Firefox). For more information, see Server Certificate Management.
-
For your initial logon, enter the following credentials:
Username:
adminPassword:
secret -
Immediately after your first logon, you will be prompted to change the password for the admin account.
Use the next procedure to specify an actual email address for the default admin user. Use this procedure if you plan on doing initial testing of email notifications using this default user.
To update the email address of the default admin account
-
From Gateway Administrator, click the Users tab.
-
Select the default "admin" user and click Edit.
-
Edit Email address and click Save.
Note
It is not possible to reset a lost administrator account password. After you begin to provision actual users, you should add appropriate users to the Administrators group to replace the default admin account. This helps ensure that the correct users will have full access to Gateway Administrator configuration options, and that backup administrators are available to provide access if needed. For details about how to add Windows domain users to the Administrators group, see Add LDAP Users to the Administrators Group.
Add File Servers to Gateway Administrator
SFTP file servers are used for both Jobs and Transfer Sites.
Jobs require at least one added file server. Job administrators can configure Reflection Gateway to scan for new and/or updated files on any added server. Jobs actions can then be used to transfer files to another location on the scanned server or to any other added server. Job actions can also be used to manage files by executing commands on any added server. If desired, the Gateway Administrator system administrator can set up File Server Groups to limit which file servers Job administrators have access to when configuring Jobs.
Transfer Sites use a single designated Transfer Site file server for all transferred files. This server can be the default Gateway Administrator Proxy or any added server. Transfer Sites files are uploaded and downloaded to and from subdirectories created in the designated Transfer site base directory. For more information, see Set Up the Transfer Site File Server.
Note
If you don't plan on configuring Jobs, and you use the default Gateway Administrator Proxy as your Transfer Site file server, you do not need to add additional file servers, so you can omit this procedure.
Before you begin
-
Know the host name (or IP address) of the SFTP file server you want to add and the port used by this host for SFTP connections. (The standard port for SFTP connection is 22.) This can be any UNIX or Windows system running an SFTP-enabled SSH server.
Note
The Reflection for Secure IT Gateway installer includes the Reflection for Secure IT Server. Each Reflection Gateway license entitles you to install this SFTP-enabled server on one system. Contact Micro Focus for information about purchasing additional Windows or UNIX servers.
-
Identify a user on this server whose User ID will be used for the connection to the server. To configure password authentication you will need to know the user's password. To configure public key authentication, public key authentication must be configured for the user on the server and you need access to the user's private key.
To add a File Server to Gateway Administrator
-
Log on to Gateway Administrator using the default admin account, or any account that has the System setup role enabled.
-
Go to System > File Servers and click New.
-
Enter the server name or IP address and the port used by this server for SFTP connections.
-
Click Retrieve to retrieve the host key.
-
For UserID enter the user whose credentials will be used to connect to this server.
-
Configure user authentication using one of the following:
- Select Password and enter the user's password.
-OR-
- Select Public key. Click Import key, then browse to locate this user's private key. This imports the key into the Reflection Gateway database. After the import, you can delete the key from the file system to minimize security risks.
-
If you are configuring a server for Jobs, leave Transfer site base directory blank; this setting is not used for Job actions.
If you plan on using this server for your Transfer Site files, browse to select a Transfer site base directory. The directory you select must be available to the specified user account. The path you select is automatically entered using the correct syntax for your server. By default, the base directory is set to a subdirectory called
Reflectionin the directory you selected. This subdirectory is not required; you can edit or delete this subdirectory name. -
Click Test Connection. (This tests the current on-screen settings. These settings are not saved until you click Save.)
-
Click Save.
Related Topics
Set Up Directory Access on your SFTP Servers
If you are going to use an SFTP server in Job actions, review this information to ensure that Job actions will have access to required directories on the server.
Each SFTP server you add to Gateway Administrator includes a UserID whose credentials provide access to this server. All transfers and commands executed on this server use the access rights of this user.
Job actions that transfer files use an SFTP connection running as the user specified for UserID.
-
If you specify a relative path for a transfer destination, files are transferred to a location relative to the SFTP home directory of this user.
-
If you specify an absolute path for a transfer destination, the location must be accessible to this user from an SFTP session.
Job actions that execute commands run a remote SSH command as the user specified for UserID. The action runs in a shell session from the user's home directory.
-
Commands specified without path information run in the SSH home directory of the user.
-
If you specify a relative path for command output, files are created in a location relative to the home directory of user.
-
If you specify an absolute path for command output, the location must be accessible to the user in an SSH terminal session.
If you want files to land in a location other than the user's home directory, you need to configure your SFTP server to provide access to the required directories. The approach you use depends on your server type.
Configuring Directory Access on a Reflection for Secure IT Server for Windows
On a Reflection for Secure IT Server for Windows, the SSH terminal
directory is configured on the Permissions pane. The default is the
user's Windows Profile directory. When configuring fully qualified paths
for Job actions that execute commands, use the actual Windows path (for
example c:\Users\Joe).
The Reflection for Secure IT Server provides SFTP directory access using
virtual directories. By default users log into a virtual directory
called Home, which is mapped to the user's Windows Profile directory.
When configuring fully qualified paths for Job actions that transfer
files, use the virtual directory name (for example Home). If you want
to configure Job actions that transfer files to a different location,
you can configure additional virtual directories. The following
procedure shows how to create a virtual directory called destination
that is mapped to the physical location c:\destination on the server.
To configure an additional accessible directory on a Reflection for Secure IT Server for Windows
-
Start the Reflection for Secure IT Server for Windows console and open the Configuration tab.
-
Click SFTP Directories and click Add.
-
For Virtual directory specify the directory name you want to use in Job actions that transfer files (for example
destination). -
For Local or UNC directory enter the actual path to a directory available to UserID on this server (for example
c:\destination). -
Click OK.
-
Save your settings (File > Save Settings).
Configuring Directory Access on a UNIX Server
On UNIX servers, both the default SSH and SFTP home directories are
typically the same (for example /home/joe).
If you want to configure Job actions that transfer files or create files in a different location, you can use UNIX system commands to specify a different home directory for the user.
Add Hubs to Gateway Administrator
Hubs are required to support Reflection Gateway Jobs. You must add at least one Hub before you can configure Jobs.
Hubs are not used for Transfer Sites; if you use only Transfer Sites, you can skip this procedure.
Before you begin
-
Install the Reflection Hub feature on the Hub server.
You will need to know a host name or IP address that can be used by Gateway Administrator to connect to this Hub.
To add a Hub Server to Gateway Administrator
-
Log on to Gateway Administrator using the default admin account, or any account that has the System setup role enabled.
-
Go to System > Hubs and click New.
-
For Reflection Hub server, enter the name or IP address of the Reflection Hub. The correct default listening port is entered automatically. Unless an administrator has modified this port, do not edit this value.
The name and currently configured listening port for the server running the Reflection Gateway Administrator service are entered automatically. In most cases you should leave these as entered.
-
Click Save and Activate. This tests the connections between the servers and configures certificates that are used by each server for authentication in subsequent connections. (For details, see Hubs Tab.)
Note
You can add multiple Hubs to ensure availability of the Reflection Hub service. If you configure connections to more than one Hub, Reflection Gateway uses a round robin schedule to determine which Hub to connect to.
Related Topics
Configure Email Support in Gateway Administrator
Reflection Gateway supports a number of optional email notification services. These include:
-
Account creation email for new users
-
Job success and failure notifications
-
Password reset email
-
Transfer site access notifications
-
Notifications sent to Transfer Site managers and/or Transfer Site members when files are uploaded or downloaded
To support these services, you need to configure access to an email server and configure the server address that will be used in URL links included in email messages.
To configure the email server connection
-
Log on to Gateway Administrator using the default admin account (or any account that has the System setup role enabled).
-
Go to System > Email Server.
-
Set Email service to Enabled. This step is required to make the remaining items editable.
-
For SMTP server, enter your email server name or IP address.
-
Configure additional options appropriate for your mail server. For details, see Email Server Tab.
-
If Check server identity is selected (recommended), click Retrieve Certificate.
-
-
Click Test Connection. (This tests the current on-screen settings. These settings are not saved until you click Save.)
-
Click Save.
The connection test on the Email Server page confirms that the server can be reached, but does not confirm that outgoing messages will be successful. You can use the next procedure to test an outgoing email. This helps ensure that the email server settings you entered meet your email server's requirements.
To test an outgoing message using your email server settings
-
Click the Email Templates tab. The Account Creation template is displayed by default.
-
Below the template text, click Preview to expand this portion of the page.
-
Enter your email address in the To box.
-
Click Send Test Email. You should receive a sample Account Creation email.
Configuring the URL for Transfer Site Email Messages
By default, links use "localhost" as the server address. If you are creating and configuring Transfer Sites that use these emails, you need to configure Gateway Administrator to create links that connect correctly to the actual Transfer Server address. To do this, you edit the Gateway Administrator Properties File, as described in the next procedure.
To configure the base server URL used in Transfer Site email message links
-
As an administrator of the system running Gateway Administrator, open the Gateway Administrator
container.propertiesin a text editor. The default location of this file is:C:\Program Files\Micro Focus\ReflectionGateway\GatewayAdministrator\conf\container.properties -
Locate the following lines:
Public facing base URL of Transfer Server (for example https://attachmate.com:9492) transfer.server.url=https://localhost:9492 -
Replace
localhostwith the host address of your Reflection Transfer Server. For example:transfer.server.url=https://myhost.rgateway.com:9492 -
Save the edited properties file.
-
Restart the Micro Focus Reflection Gateway Administrator service. A restart is required after any changes to the properties file.
Related Topics
Enable Reflection Gateway Connections in the Reflection Secure Shell Proxy
This procedure applies to Transfer Sites only. It is not required for creating and using Jobs.
To support file exchange using the Reflection Gateway Transfer Sites, you must configure the Reflection Secure Shell Proxy to enable access by Reflection Gateway users.
Before you begin
To enable Reflection Gateway Transfer Site transfers
-
Log in as an administrator to the Windows system on which you installed the Reflection Gateway Proxy. Use the Windows Start menu to launch the Reflection Secure Shell Proxy console.
-
On the Reflection Gateway Users pane, enable Allow access to Reflection Gateway users.
-
For Gateway Administrator host, enter the name or IP address of the computer running the Reflection Gateway Administrator. (If you installed all Reflection Gateway services on the same computer, you can leave the default value, localhost.) Leave the default port value (9190). Reflection Gateway Administrator is configured to listen on this port by default.
-
(Optional) change the value for Reflection Gateway user access account from the default (Service account) to an actual User account on the system. The following factors may enter into this decision:
-
When Service account is selected, Reflection Gateway users run using the same privileges as the Reflection Secure Shell Proxy service (the Local System account). You may want to specify an alternate user account with more limited privileges.
-
Running as the service account is limited by the operating system to 110 simultaneous client connections. Configuring a User account does not have this limitation.
-
-
Click Activate and verify. This saves your settings and triggers actions that ensure that the Reflection Gateway Proxy services can establish a secure connection with the Gateway Administrator.
-
You will be prompted to accept the certificate presented by the Gateway Administrator server. Click Yes to establish the trust relationship.
-
When the configuration update is complete, click Close to close the Web service connection dialog box.
-
Click Yes when prompted to restart the Reflection Transfer Server service. This step is required.
-
Set Up the Transfer Site File Server
This procedure applies to Transfer Sites only. It is not required for creating and using Jobs.
Reflection Gateway Transfer Sites use directories on a designated Transfer Site file server for file upload and download. Use the procedures described here to designate which server should be used.
Use the Reflection Gateway Proxy for Transfer Site files
By default, Gateway Administrator is configured to use the Reflection Gateway Proxy for as the Transfer Site file server. Files are transferred to and from this server. This configuration is appropriate for initial testing, or if you use Transfer Sites to manage transfers within your internal network. You do not need to modify any default settings to use this configuration.
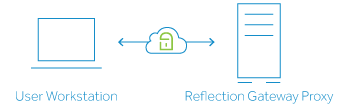
To customize the base directory used for files on the Reflection Secure Shell Proxy, see Change the Transfer Site Directory used by the Reflection Secure Shell Proxy.
Use an added SFTP server for Transfer Site files
Transferring files to and from an added SFTP server is recommended for most environments. If you run the Reflection Gateway Proxy in the DMZ, you can configure Reflection Gateway to transfer files securely to and from an SFTP server running behind your firewall. In this configuration, data streams continuously through the Reflection Secure Shell Proxy, eliminating the need to save data on the system running the proxy.
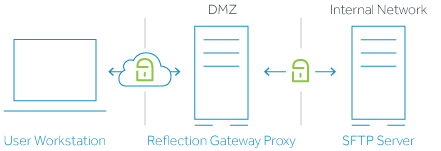
An additional advantage of this configuration is that it supports Post Transfer Actions. These actions are not supported when the Reflection Gateway Proxy is the Transfer Site file server.
To set up the added SFTP server
-
Log on to Gateway Administrator using an account in the Administrators group (or any account that has the System setup role enabled).
-
In the New (or Edit) File Server page, set Transfer site base directory to the directory you want to use for Transfer Site file exchange.
Note
If you use the Browse button to specify a directory on the server, Gateway Administrator automatically adds a
Reflectionsubdirectory to the path to help ensure that Transfer Site files are easy to locate on the server. This subdirectory is not required; you can edit the path to modify or remove the subdirectory name if you prefer. -
Click Save.
-
In the File Servers tab, use the Transfer site file server drop-down list to select the added SFTP server.
-
Click Save.
Configure Server Certificates
When you log on to Gateway Administrator, the browser connects to the Reflection Gateway Administrator server. The connection is made using HTTPS and the default configuration results in certificate warning messages.
Why you see certificate warning messages
When an HTTPS connection is established, the browser requires server authentication. By default, the Reflection Gateway servers send a self-signed security certificate to the browser for this purpose. (A self-signed certificate is signed by the same entity that it certifies.) The browser checks the digital signature in this certificate against its list of trusted Certificate Authorities (CAs). You see a certificate warning because the signer of the certificate is not in your browser's list of trusted CAs.
Managing certificates
Depending on where you are in your Reflection Gateway evaluation and configuration process, you can use any of the following approaches to manage server certificates.
-
Use the default self-signed certificates and ignore the certificate errors.
This option is appropriate during initial testing.
-
Configure your browser to trust the self-signed certificates.
This option is appropriate during initial testing. You might also choose this as a permanent option for the Gateway Administrator.