Ensuring High Availability of Reflection Gateway Services
Ensuring High Availability of Reflection Gateway Services
To ensure high availability of Reflection Gateway services, you can configure duplicate server systems and use a load-balancing proxy to manage connections between the components.
To support any load-balancing system for Reflection Gateway, you will need to create a database on a remote system and configure duplicate Gateway Administrator servers to communicate with this database. Details are provided in the procedures that follow. The database server should be configured for failover, for example using a Windows cluster. Failover configuration procedures for the database are not covered in this guide.
Note
The port values shown in these diagrams and in the sample HAProxy configurations are the defaults. The diagrams also omit some connections that do not need to be handled by the proxy. For more detailed information, see Ports and Firewall Configuration.
Configuring high availability for Jobs
To support load balancing for jobs, you will need to create identically configured Gateway Administrator servers and use a load balancing proxy to manage connections to these servers, as shown here:
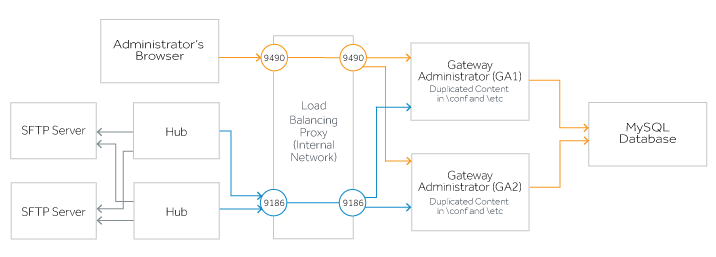
To set up load balancing for Jobs
-
Create identically configured Gateway Administrator systems that connect to the same database.
-
Configure a load balancing proxy to forward requests coming from administrators' browsers (port 9490) and Reflection Hub servers (port 9186) to the Gateway Administrator servers. For an example using HAProxy, see Sample Proxy configuration in the internal network.
-
Install the Reflection Hub service on two or more systems and configure any Gateway Administrator instance to connect to each Hub.
-
On the Hubs tab, confirm that the Gateway Administrator server value for each Hub is specified using the network name or IP address that is configured on the load balancing proxy for connections from your Hub systems.
-
You can add or delete Hubs at any time after you have configured your database connection. The round robin connection to the Hubs is managed by Gateway Administrator and all Hub connection settings are stored in the common database. Increasing the number of hubs may improve performance if your jobs manage large numbers of file multiple transfers.
-
Configuring load balancing for Transfer Sites
Load balancing for Transfer Sites typically involves two load-balancing proxies--one in the DMZ and one in the internal network. The proxy in the DMZ forwards requests from transfer clients to identically configured Reflection Gateway Proxy systems. The proxy in the internal network forwards requests from the Reflection Gateway Proxy systems to identically configured Gateway Administrator systems.
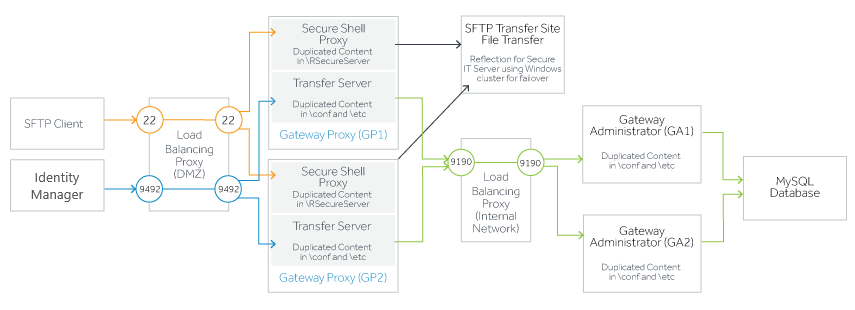
-
Create identically configured Gateway Administrator systems that connect to the same database.
-
Create identically configured Reflection Gateway Proxy systems.
-
Configure a load balancing proxy in the DMZ to forward requests coming from Transfer Site users (ports 22 and 9492) to the services running on the Reflection Gateway Proxy systems. For an example using HAProxy, see Proxy configuration in the DMZ.
-
Configure a load balancing proxy in the internal network. To support both Jobs and Transfer sites you will need to forward requests coming to Gateway Administrator from administrators’ browsers (port 9490), Reflection Hub servers (port 9186), and the Reflection Gateway Proxy systems (port 9190). Examples for all of these are included in Sample Proxy configuration in the internal network.
-
Configure a failover system for the Transfer Site file server. If the server is a Reflection for Secure IT Server for Windows, you can use a Windows cluster. See "Using a Server Cluster" in the Reflection for Secure IT Server Help.
Configuring load balancing for both Jobs and Transfer Sites
Setting up load balancing for both Jobs and Transfer Sites combines the procedures above.
To set up load balancing for both Jobs and Transfer Sites
-
Create identically configured Gateway Administrator systems that connect to the same database.
-
Create identically configured Reflection Gateway Proxy systems.
-
Configure a load balancing proxy in the DMZ to forward requests coming from Transfer Site users (ports 22 and 9492) to the services running on the Reflection Gateway Proxy systems. For an example using HAProxy, see bridgehead_title.
-
Configure a load balancing proxy in the internal network. To support both Jobs and Transfer sites you will need to forward requests coming to Gateway Administrator from administrators' browsers (port 9490), Reflection Hub servers (port 9186), and the Reflection Gateway Proxy systems (port 9190). Examples for all of these are included in bridgehead_title.
-
Install the Reflection Hub service on two or more systems and configure any Gateway Administrator instance to connect to each Hub.
-
On the Hubs tab, confirm that the Gateway Administrator server value for each Hub is specified using the network name or IP address that is configured on the load balancing proxy for connections from your Hub systems.
-
You can add or delete Hubs at any time after you have configured your database connection. The round robin connection to the Hubs is managed by Gateway Administrator and all Hub connection settings are stored in the common database. Increasing the number of hubs may improve performance if your jobs manage large numbers of file multiple transfers.
-
-
Configure a failover system for the Transfer Site file server. If the server is a Reflection for Secure IT Server for Windows, you can use a Windows cluster. See "Using a Server Cluster" in the Reflection for Secure IT Server Help.
Configure Duplicate Gateway Administrator Systems
To support high availability, you will configure and test an initial instance of Gateway Administrator, then create an identically-configured Gateway Administrator system and use a load-balancing proxy to distribute the load between these systems. Each Gateway Administrator system must:
-
Use a common database.
-
Use identical server certificates.
-
Use identical copies of the Gateway Administrator properties file (
container.properties). -
Use identical Job templates (if this optional feature is configured).
Note
Configuring more than two Gateway Administrator systems will not improve performance and may lead to slower response rates.
Before you begin
-
Run the Setup program on each system that will run Gateway Administrator. Use the Features tab to install the Reflection Gateway Administrator feature. Restart Windows on each system. This starts the service and creates initial default settings files.
-
Select one of the Gateway Administrator systems for initial configuration and testing. After you have this instance working, you will copy required files to duplicate the configuration on your second system.
Configure an initial Gateway Administrator system
-
Configure Gateway Administrator to use an external database. The database should be located on a different system from each of the systems that will run Gateway Administrator. (This database should be configured for failover, for example using a Microsoft cluster. This procedure is not included here.)
-
If you are using a CA-signed certificate for server HTTPS authentication, replace the default self-signed server certificate with the CA certificate and test connections using the new certificate. See Replace the Default Server Certificate. This certificate should be configured to authenticate the server name that will be used for connecting to you your load-balancing proxy.
-
If you are using Transfer Site email notifications, configure the URL that will be used to create links in email messages. This requires an edit to the
container.propertiesfile. -
If you are using Job templates, configure and test a
jobTemplate.xmlfile. -
Log onto Gateway Administrator and test your configuration.
Copy required files to the duplicate Gateway Administrator system
-
Locate the Gateway Administrator folder on your initial system. The default location is:
C:\Program Files\Micro Focus\ReflectionGateway\GatewayAdministrator\ -
Copy the following files to the duplicate system.
Files Details container.propertiesIn the confsubfolder.
Includes settings and password for connecting to the database. If configured, it includes the URL used in email notifications, and settings for using a CA-signed certificate.server.cerserver.bcfksIn the etcsubfolder.
A private key stored in server.bckfs is used to encrypt passwords for LDAP servers, SFTP servers, and SMTP servers. An identical private key must be present in each system to enable each server to encrypt or decrypt these passwords.servletcontainer.cerservletcontainer.bcfksThese files contain the certificate and private key used to authenticate the server when users make HTTPS connections to Gateway Administrator. - If you are using the default self-signed certificate, copy servletcontainer.cer and servletcontainer.bckfs located in the etc subfolder.
- If you are using a CA-signed certificate, find the certificate package file in the location specified in the container.properties file. For example:
servletengine.ssl.keystore=../etc/myCAkeystore.bcfks
Copy this file to the same location on each of the other systems.
jobTemplate.xmlIn the confsubfolder.
This file is only needed if you have configured a Job template.
Configure Duplicate Reflection Gateway Proxy Systems
The Reflection Gateway Proxy system is required to support Transfer Sites. Two services run on this system:
-
Reflection Transfer Server
-
Reflection Secure Shell Proxy.
To support high availability, you will configure and test an initial instance of the Reflection Gateway Proxy system, then create an identically-configured system and use a load-balancing proxy to distribute the load between these systems.
Before you begin
-
Run the Setup program on each system. Use the Features tab to install the Reflection Gateway Proxy feature on each of these systems. Restart Windows on each system. This starts the services and creates initial default settings files.
-
Log onto Gateway Administrator. Go to System > File Servers and confirm that Transfer site file server is set to use an added SFTP Server. Using the default Reflection Gateway Proxy is not supported for a high availability configuration because there is no replication of data between the Reflection Gateway Proxy systems.
-
Select one of the Reflection Gateway Proxy systems for your initial configuration and testing. After you have this instance working, you will copy required files to duplicate the configuration on your other system.
Configure an initial Reflection Gateway Proxy system
-
Start the Reflection Secure Shell Proxy console on the server you are using for initial configuration.
-
On the Reflection Gateway Users pane, enable Allow access to Reflection Gateway users.
-
For Gateway Administrator host, enter the network name or IP address of the load-balancing proxy configured to connect to Reflection Gateway Administrator.
-
Click Activate and verify. Click Yes when prompted to restart the Reflection Transfer Server service.
This action configures the connection between components and saves an internal password that is used to connect to Gateway Administrator. (Each time you click Activate and verify, the internal password is changed.) Changes are saved to the following files: the Secure Shell Proxy's
trustedWebService.cerandRSITDatabasefiles and the Transfer Server'strustedWebService.cerandcontainer.propertiesfiles. -
If your users will will be using the Identity Manager, you need to replace the default self-signed server certificate with a CA-signed certificate. See Replace the Default Server Certificate. This certificate should be configured to authenticate the server name that will be used for connecting to your load-balancing proxy.
-
Test your configuration. Use Gateway Administrator to create Transfer Sites and confirm that you can transfer files using an SFTP client.
Copy required configuration files to the duplicate Reflection Gateway Proxy system
-
On the destination server, stop the Reflection Secure Shell Proxy and the Reflection Transfer Server services.
-
Locate the Reflection Secure Shell Proxy configuration files. The default location is:
C:\ProgramData\Micro Focus\RSecureServer -
Copy the following files to the duplicate system.
File Details rsshd_config.xmlThe Reflection Secure Shell Proxy configuration file. The settings saved to this file include the values you have specified on the Reflection Gateway Users tab for connecting to the Gateway Administrator host name and port. RSITDatabaseThe Reflection Secure Shell Proxy's encrypted credential cache. RSITDatabase.secThis file contains the key required to decrypt the credential cache and is required to use the cache. trustedWebService.cerContains the public key used to authenticate Reflection Gateway Administrator. This file is created when you click the Activate and Verify button on the Reflection Gateway Users pane. hostkeyThe private key of the public/private host key pair used to authenticate this server. hostkey.pubThe public key of the public/private host key pair used to authenticate this server. -
Locate the Reflection Transfer Server configuration files. The default location is:
C:\Program Files\Micro Focus\ReflectionGateway\TransferServer -
Copy the following files to the duplicate system.
Files Details container.propertiesIn the confsubfolder.
Includes settings and password for connecting to the Gateway Administrator. If configured, it incudes settings for using a CA-signed certificate.trustedWebService.cerIn the etcsubfolder.
Public key of Gateway Administrator.servletcontainer.cerservletcontainer.bcfksThese files contain the certificate and private key used to authenticate the server when users make HTTPS connections to the Reflection Transfer Server. - If you are using the default self-signed certificate, copy
servletcontainer.cerandservletcontainer.bcfkslocated in the etc subfolder. - If you are using a CA-signed certificate, find the certificate package file in the location specified in the container.properties file. For example:
servletengine.ssl.keystore=../etc/
Copy this file to the same location on each of the other systems.
- If you are using the default self-signed certificate, copy
-
Restart the Reflection Secure Shell Proxy and the Reflection Transfer Server on the duplicate system.
Sample HAProxy Configuration
The sample configuration files shown here provide examples of configuration for two HAProxy load balancers. The proxy shown for use in the internal network supports both Jobs and Transfer sites. The proxy in the DMZ handles connections from Transfer Site users; it is not required for Jobs.
For a visual representation of proxy configuration, see the diagrams above.
Sample Proxy configuration in the internal network
This example shows settings to forward requests to two identically configured Gateway Administrator servers from browsers (port 9490), the Reflection Hub service (port 9186), and the Reflection Transfer Server service (port 9190).
global
log 127.0.0.1 local0
log 127.0.0.1 local1 notice
maxconn 2384
frontend www-GA-https
bind :9490
mode tcp
default_backend www-GA-backend
frontend www-HUB-to-GA-https
bind :9186
mode tcp
default_backend www-HUB-to-GA-backend
frontend www-XFER-to-GA-https
bind :9190
mode tcp
default_backend www-XFER-to-GA-backend
backend www-GA-backend
mode tcp
balance roundrobin
stick-table type ip size 200k expire 30m
stick on src
default-server inter 1s
server GA1-HTTPS 10.10.10.333:9490 check id 1
server GA2-HTTPS 10.10.10.444:9490 check id 2
backend www-HUB-to-GA-backend
mode tcp
balance roundrobin
default-server inter 1s
server GA1-HUB 10.10.10.333:9186 check id 1
server GA2-HUB 10.10.10.444:9186 check id 2
backend www-XFER-to-GA-backend
mode tcp
balance roundrobin
default-server inter 1s
server GA1-XFER 10.10.10.333:9190 check id 1
server GA2-XFER 10.10.10.444:9190 check id 2
Sample Proxy configuration in the DMZ
This example shows sample settings to forward connections from Transfer Site users to two identically configured Reflection Gateway Proxy servers. Connections from the Reflection Identity Manager require forwarding of both HTTPS (port 9492). Connections from SFTP clients require forwarding of SSH only.
global
log 127.0.0.1 local0
log 127.0.0.1 local1 notice
maxconn 2384
frontend www-Transfer-Client-https
bind :9492
mode tcp
default_backend www-transfer-client-backend
frontend www-ssh-proxy
bind :22
mode tcp
default_backend www-ssh-proxy-backend
backend www-transfer-client-backend
mode tcp
balance roundrobin
stick-table type ip size 200k expire 30m
stick on src
default-server inter 1s
server GP1-HTTPS 10.10.10.111:9492 check id 1
server GP2-HTTPS 10.10.10.222:9492 check id 1
backend www-ssh-proxy-backend
mode tcp
balance roundrobin
stick-table type ip size 200k expire 30m
stick on src
default-server inter 1s
server GP1-SSH 10.10.10.111:22 check id 1
server GP2-SSH 10.10.10.222:22 check id 1