6.1 Command Reference Conventions
This section consists of descriptions and examples of the commands that make up SecureLogin application definitions.
An index is included in Section 2.0, Application Definition Command Quick Reference.
6.1.1 Command Information
The information for each of the commands includes:
Use With values
|
Command |
Description |
|---|---|
|
Java |
Use as part of a Java* application definition. |
|
Startup |
Use as part of a startup. |
|
Terminal Launcher |
Use as part of a terminal launcher application definition. |
|
Advanced Web |
Use as part of a manually created website or Internet application definition. Not compatible with the Web Wizard application definition language. NOTE:A predefined Web application and an Advanced Web application definition are the same. |
|
Web Wizard |
Use as part of application definitions created automatically by the Web Wizard. Web Wizard application definitions can be kept in their original XML format or converted to an ASCII script for advanced editing. |
|
Windows |
Use as part of a Windows application definition. |
Type Values
|
Command |
Description |
|---|---|
|
Action |
Performs an action, for example, the Type command types information into a field. |
|
Dialog specifiers |
Defines dialog boxes, for example, the Parent and Class commands. |
|
Flow control commands |
Directs SecureLogin to a specific location in the application definition, for example, Repeat and EndScript commands. |
|
Variable manipulators |
Modifies variables, such as the Add and Subtract commands. |
6.1.2 Web Wizard Application Definition Conventions
The SecureLogin advanced Web Wizard makes it easier for users to enable single sign-on (SSO) websites and capture a user’s web-based login details. When the user accesses a web page from the browser, SecureLogin automatically launches the Web Wizard.
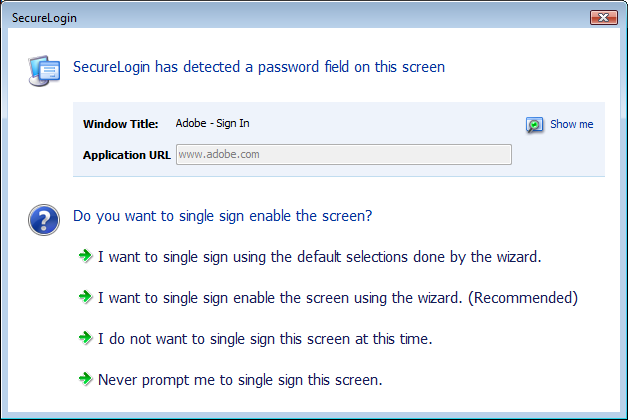
The Web Wizard captures the user’s login details and adds them to the user’s web application definitions.
When managing users’ web login credentials, the Definition tab of the Advanced Setting page allows you to customize site and user credential details. Also, an Advanced function is available under the Definitions tab that provides more functionalities with their associated values and an option to convert the user’s credentials to an application definition.
For information about how to manage application definitions, see Managing Application Definitions.
Site Matching
Web commands are added to allow much finer control of site matching. Detailed information of the loaded website can be matched and used to execute blocks of scripting commands. The technique used to specify constraints upon a site match are similar to those constraints used in the windows scripting.
Instead of Dialog/EndDialog commands, equivalent Site/EndSite commands have been created and can now be used. Within these Site blocks, Match commands can be used to filter a given site. If one of the specified match commands fails to match, the site block fails to match as a whole. See Site/Endsite.
Form/Field/Option Matching
When matching a specific form, field, or other match option, multiple items match the selection criteria. In these cases, the first item on the website which matches is considered to be the match. To access other fields that also need to be matched, subsequent match commands can be added with the same selection criteria.
NOTE:Matched items might only be matched once. Each ID must be unique and cannot have been used previously.
For example, the following will match a site with two password fields. The first is given the ID '#1:1' and the second is given the ID '#1:2'.
MatchField #1:1 -type "password" MatchField #1:2 -type "password"
Form/Field/Option ID
When matching a site, match methods are used to give specific fields, forms and options their own unique ID. When the site has been successfully matched, the given ID is used in input commands to specify particular items.
The actual IDs are denoted with a # followed by 1, 2 or 3 numbers, each separated by a colon – for instance, "#1:3:2".
6.1.3 Auditing
For auditing, use the AuditEvent command built into SecureLogin or the LogEvent command from the Windows Resource Kit. See the SecureLogin Administration Guide. See AuditEvent.
6.1.4 One Time Passwords
The use of multiple passwords places a high maintenance overhead on large enterprises. Users are required to manage multiple passwords, which can result in a significant cost, particularly with regard to calls to the help desk to reset forgotten passwords, or to ensure that all passwords are provisioned when a new user starts or are deleted when an existing user leaves the organization.
One of the benefits of implementing one time password (OTP) systems is that it is impossible for a password to be captured on the wire and replayed to the server. This is particularly important if a system does not encrypt the password went it is sent to the server, as is the case with many legacy mainframe systems.
OTP also offers advantages in terms of disaster recovery because the encryption key is used to generate OTP rarely changes. System restoration, which might be to a system version that is hours or many months old, can be achieved without consideration of restoring users' passwords or notifying staff of new passwords.
SecureLogin provides a secure, robust and scalable infrastructure by integrating ActivCard* OTP authentication functionality. See GenerateOTP.