Remote Port Forwarding
Use remote port forwarding to forward data securely from an application client running on the Secure Shell server host. When you configure remote port forwarding, you designate an arbitrary remote port to use for forwarding data and a destination host and port to receive the data. Remote port forwarding works as follows.
-
When the Secure Shell connection is established, the Secure Shell server opens a listening socket on the Secure Shell server host using the specified listening port.
-
A client application running on the Secure Shell server host is configured to connect to the listening port (rather than directly to the application server host and port). When that client establishes a connection, all data is sent to the listening port, and then redirected to the Secure Shell server.
-
The Secure Shell server encrypts the data and sends it securely through the SSH tunnel to the Secure Shell client.
-
The Secure Shell client receives data, decrypts it, and redirects it to the destination host and port (on the Secure Shell client host) that is used by the server application.
-
The return data from the server application is directed to the Secure Shell client, which encrypts it and sends it securely to the Secure Shell server through the SSH tunnel. The Secure Shell server decrypts the data and redirects it to the original client application.
The general command-line syntax for remote port forwarding is:
ssh -R listening_port:app_host:hostport user@sshserver
The diagram that follows illustrates one possible remote port forwarding configuration.
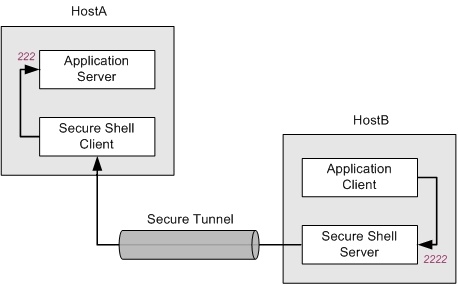
The application server and the Secure Shell client run on HostA. The Secure Shell server and application client both run on HostB. All data sent to port 2222 on HostB is forwarded to port 222 on HostA. In this arrangement, all data in transit is securely encrypted. The following command configures this.
ssh -R 2222:localhost:222 user@HostB