6.5 Securing Communication Channels
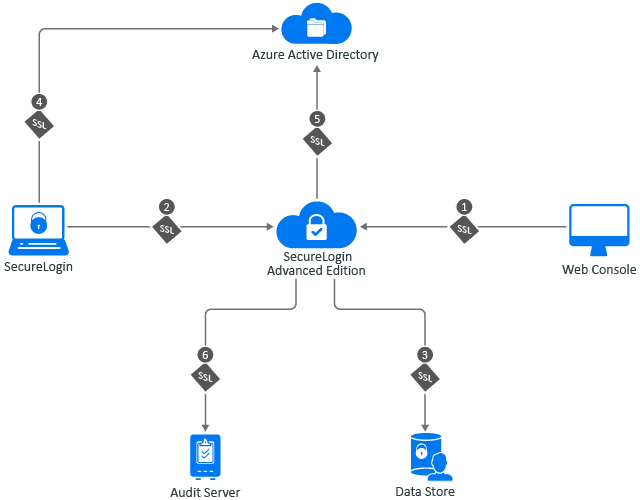
SecureLogin provides the following six communication channels:
-
Web Console to Advanced Edition
-
SecureLogin Client to Advanced Edition
-
Advanced Edition to Data Store
-
SecureLogin Client to Azure AD
-
Advanced Edition to Azure Active Directory (AD)
-
Advanced Edition to Audit Server
Figure 6-1 SSL Communication Channels
In this Section
-
Protecting the Channel between Advanced Edition and the Web Console with SSL
-
Protecting the Channel between Advanced Edition and the SecureLogin Client with SSL
-
Protecting the Channel between Advanced Edition and Data Store with SSL
-
Protecting the Channel between SecureLogin Client and Azure AD with SSL
-
Protecting the Channel between Advanced Edition and Azure AD with SSL
-
Protecting the Channel between Advanced Edition and Audit Server with SSL
6.5.1 Protecting the Channel between Advanced Edition and the Web Console with SSL
Channel 1 in Figure 6-1, SSL Communication Channels.
While installing Advanced Edition, SecureLogin uses Let's Encrypt to generate the certificate. You can replace the default certificate with a third-party certificate authority (CA) issued certificate, such as Verisign.
For more information about how to replace the default certificate, see Using Your CA Signed Certificate
in the NetIQ SecureLogin 9.0 Administration Guide.
6.5.2 Protecting the Channel between Advanced Edition and the SecureLogin Client with SSL
Channel 2 in Figure 6-1, SSL Communication Channels.
The SecureLogin client communicates with Advanced Edition over a secure SSL port. This port is con-figured while installing the client in the Advanced Edition mode.For higher security, it is recommended to install the root CA certificate on the SecureLogin client ma-chines.
6.5.3 Protecting the Channel between Advanced Edition and Data Store with SSL
Channel 3 in Figure 6-1, SSL Communication Channels.
For higher security, configure the data store root certificate in SecureLogin-Server-x.x.x.x\values.yaml.
Configuring the Datastore Root Certificate
-
Create a folder named certs inside the SecureLogin-Server-x.x.x.x folder of the helm charts.
-
Copy the datastore root certificate to the certs folder.
-
Open SecureLogin-Server-x.x.x.x\values.yaml and specify the following details in the SSL section:
-
verifyDBCert: Specify true. The server host name in the certificate is verified to ensure that it matches the host name specified in values.yaml.
-
DBCert: Specify the name of the data store root certificate that you copied to the certs folder.
-
DBCertSecret: To change the certificate for the first time, no need to change this value. However, the next time onward, you must change both DBCert and DBCertSecret.
-
-
Save the file.
-
Perform a helm install or upgrade using the following command:
-
To install:
helm install <name-of-the-release> <name-of-the-helm-chart> -n <name-of-the-namespace>
For example, helm install slserver001 server -n nsl-namespace
-
To upgrade:
helm upgrade <release-name> <name-of-the-helm-chart> -n <name-of-the-namespace>
For example, helm upgrade slserver server -n my-ingress
-
6.5.4 Protecting the Channel between SecureLogin Client and Azure AD with SSL
Channel 4 in Figure 6-1, SSL Communication Channels.
The SecureLogin client communicates to the identity provider over the TLS 1.2 protocol with the verified server certificate.
This channel is used for obtaining OAuth 2.0 tokens from the identity provider. The SecureLogin client uses the following methods:
-
Initial request using Microsoft OAuth 2.0 Resource Owner Password Credentials (ROPC) grant. The ROPC flow is a single request. It sends the client identification and user's credentials to Azure AD for fetching the required token. For more information, see Microsoft identity platform and OAuth 2.0 Resource Owner Password Credentials.
-
Refresh request using a refresh token: To improve the performance, refresh tokens can be enabled by adding the offline_access scope. For example, "api://$clientid/All offline_access"
The offline_access scope is optional if you want users to receive a refresh token.
For more information, see Microsoft identity platform and OAuth 2.0 Resource Owner Password Credentials and Resource owner password credentials policy.
6.5.5 Protecting the Channel between Advanced Edition and Azure AD with SSL
Channel 5 in Figure 6-1, SSL Communication Channels.
Advanced Edition communicates to the user and groups directory and identity provider over the TLS 1.2 protocol with the verified server certificate.
Advanced Edition uses the bearer access token to verify the authorization with the identity provider. It requests for an On Behalf Of (OBO) token using the MSAL library or using Graph REST API.
-
Using MSAL library: With the OBO token, Advanced Edition requests the information about users and groups for collecting inherited settings or performing management tasks.
-
Using Graph REST API: Graph API ensures the secure delivery of the data to Azure AD. For more information, see Microsoft Graph Documentation.
6.5.6 Protecting the Channel between Advanced Edition and Audit Server with SSL
Channel 6 in Figure 6-1, SSL Communication Channels.
For enhanced security, configure the audit server root certificate in SecureLogin-Server-x.x.x.x\values.yaml.
For information about how to configure the audit server root certificate in values.yaml, see Configuring the Root Certificate in values.yaml
in the SecureLogin 9 Advanced Edition Installation and Configuration Guide.
Ensure that the audit server is configured to listen on a TLS port. For information about how to configure the port for the audit server, see Configuring the Audit Server on the Web Console
in the SecureLogin 9 Advanced Edition Installation and Configuration Guide.