16.5 FTP (Pure-FTPd) and OES
FTP file services on OES servers are provided by Pure-FTPd, a free (BSD), secure, production-quality and standard-conformant FTP server. The OES implementation includes support for FTP gateway and offers a level of integration between eDirectory and Pure-FTP that allows users to authenticate to eDirectory for FTP access to the server.
A new module oesftpipc.service is introduced for OES FTP server (pure-ftpd) to fetch the user details of eDirectory (FQDN) and Active Directory (User ID, home directory, AD domain name) during authentication.
The pure-ftpd.service and oesftpipc.service must be running on OES server for FTP functionality to work.
The OES implementation also includes support for FTP gateway functionality between Active Directory (AD) and Pure-FTPd that allows users to authenticate to AD for FTP access to the server. For more information, see FTP (Pure-FTPd) and OES for AD Users in the NSS AD Administration Guide.
This section discusses the following topics:
16.5.1 Planning for Pure-FTPd
Before installing Pure-FTPd, make sure that users requiring FTP access are LUM-enabled and have access rights to the areas on the server they need to use.
16.5.2 Installing Pure-FTPd
To install Pure-FTPd, select the OES FTP pattern in the OES installation.
16.5.3 Home Directory Support in Pure-FTPd
The FTP server supports a home directory for users on local and remote NCP servers. The remote server can be an OES server. When the home directory is set for the user in eDirectory, the user is placed in the home directory on successful login to the Linux server.
Pure-FTPd supports three levels of home directory, default home directory, a user specific home directory on the local system, and a user specific home directory identified by the value set in eDirectory.
POSIX User Home Directory
The POSIX home directory is the directory that is available by default on POSIX file systems. The POSIX home directory is defined at the file system level and cannot be disabled.
DefaultHomeDirectory and eDirectory home directories can be disabled. If one or both of them are enabled, the following is used to establish the precedence:
-
User specific home directory set in eDirectory
-
Default home directory
-
POSIX user home directory
User Specific Home Directory in eDirectory
An administrator can set the home directory for eDirectory users as part of the User object in eDirectory. On successful login to the FTP server, the user is placed in the home directory set in the user object. The User's home directory can exist either on the OES server that is hosting the FTP service or on any other OES server in the same tree.
A new EnableRemoteHomeDirectory option is now available to support this home directory. By default, this option is set to NO and the home directory set for the user in eDirectory is ignored.
To enable eDirectory based home directory support, you must set both EnableRemoteHomeDirectory and remote_server to YES. FTP will then read the user’s home directory from eDirectory and mount it locally.
Default Home Directory
DefaultHomeDirectory indicates the path to the common home directory for all FTP users. On successful login to the Pure-FTPd, users are placed in the default home directory. The default home directory can be local or on a locally mounted NSS path or on a remote NCP Server. It can be either an NCP volume or an NSS volume and it can be configured by using the DefaultHomeDirectory and DefaultHomeDirectoryServer settings. If the home directory is on a remote server, use DefaultHomeDirectoryServer, and set it to the IP or DNS name of the remote NCP server. As with any NSS volume, the FTP client should have required rights over the NSS volume whether DefaultHomeDirectory is on a local or remote server or not.
The DefaultHomeDirectoryServer option is now available to differentiate whether DefaultHomeDirectory is on a local or remote server. By default, this option is set to NO so DefaultHomeDirectory points to a local path.
To set DefaultHomeDirectory to point to a remote NCP server with a DNS entry, you must specify the full path to the remote server, including the volume name. For example, DefaultHomeDirectory /ftphome. You must also set both DefaultHomeDirectory and remote_server to YES.
NOTE:
-
If DefaultHomeDirectory path is a POSIX path (non NCP volume) then it is supported only on local FTP server and not on remote server. In that case DefaultHomeDirectory path should be /home/commonpath (any POSIX path) and DefaultHomeDirectoryServer should be Null or commented.
Backslash in Input Paths
Support for backslashes in input path is provided. Using FTP client on Windows, you can use backslash as separator in the path. allow_backslash_in_path option is now available to allow back slash in the path. By default the option is set to NO.
16.5.4 Configuring Pure-FTPd on an OES Server
To configure the Pure-FTPd server on OES, edit the /etc/pure-ftpd/pure-ftpd.conf file.
NOTE:It is very strongly recommended that you read through the entire /etc/pure-ftpd/pure-ftpd.conf file and be familiar with the available parameters and settings.
For more information, see the pure-ftpd man page.
Refer to the /usr/share/doc/packages/pure-ftpd/README.TLS file for SSL/TLS configuration.
16.5.5 Configuring Pure-FTPd for Secure Connections with TLS
FTP configured servers that support TLS use certificates such as CA signed certificate, self signed certificate, or eDirectory certificate to check the security and identity of servers.
Prerequisites for Configuring FTP Server
-
A valid third-party CA-signed certificate or an eDirectory server certificate must be available on the server along with the private key.
-
The private key and the certificate must be a single file with name pure-ftpd.pem.
Combining the Certificate and Private Key into a Single File
To combine the files, execute the following command:
cat certificate.pem private_key.pem > /etc/ssl/private/pure-ftpd.pem
The file path is /etc/ssl/private/ by default and can be changed.
Example: For combining eDirectory certificate and private key
cat /etc/ssl/servercerts/servercert.pem /etc/ssl/servercerts/serverkey.pem > /etc/ssl/private/pure-ftpd.pem
Modifying TLS for FTP Server
-
Open the /etc/pure-ftpd/pure-ftpd.conf configuration file in a text editor.
-
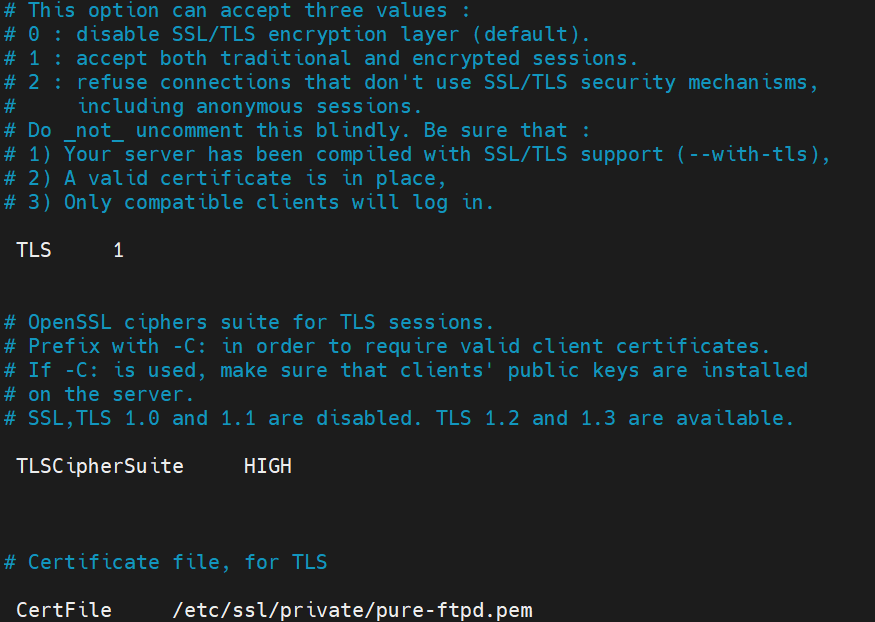
Update the TLS value as per your security requirement.
TLS Value
Functions
0
Disables the TLS support. By default, TLS is disabled.
1
Server accepts both secure and non-secure connections with TLS layer.
2
Server accepts only secure connections.
-
Uncomment and provide required inputs for TLS, TLSCipherSuite, and CertFile.
The CertFile is the location of the pure-ftpd.pem file.
-
Save the configuration file.
-
Restart the Pure-FTPd daemon with the following command:
systemctl restart pure-ftpd.service
NOTE:Pure-FTPd daemon fails to start if the pure-ftpd.pem certificate is corrupted.
Verifying the Certificate Used
To check which certificate is used, execute the following command:
openssl s_client -connect hostname/server_ip:21 -starttls ftp
This command displays the details of the certificate used by FTP.
16.5.6 Administering and Managing Pure-FTPd on an OES Server
Starting Pure-FTPd
Start the Pure-FTPd server using the systemctl restart pure-ftpd.service command.
Verifying Pure-FTPd
To verify the status of Pure-FTPd, run the following commands:
systemctl status oesftpipc.service
systemctl status pure-ftpd.service
Initializing Multiple Instances
Pure-FTPd is loaded by using a configuration file. Multiple instances of Pure-FTPd can be loaded using different configuration files.
By default, an instance of Pure-FTPd using /etc/pure-ftpd/pure-ftpd.conf file is loaded at the boot time. For loading multiple instances, new configuration files need to be created.
To load a new instance of Pure-FTPd:
-
Create a new configuration file for each instance.
For example: Copy /etc/pure-ftpd/pure-ftpd.conf to a different location. Rename the file to pure-ftpd1.conf and move it to /etc/opt/novell/pure-ftpd1.conf.
-
Modify the following settings in the configuration file to avoid IP address or port conflicts between the instances:
-
PIDFile: Points to the full path of the PID file created by the pure-ftpd instance. PID file is used for unloading a particular instance of pure-ftpd. Hence, ensure that the PID File path is unique for every instance.
For example: /var/run/pure-ftp1.pid, /var/run/pure-ftp2.pid.
-
Bind: By default, pure-ftpd binds to all the IP addresses on the system and listens to requests over port 21. Modify the settings of the bind such that all the pure-ftpd instances bind to different IP addresses or port combinations.
also, modify the settings in the /etc/pure-ftpd/pure-ftpd.conf to avoid any IP address or port conflict from the second instance.
For example: If a system has two interfaces with two IP addresses 10.1.1.1 and 10.1.1.2, then the bind setting for two pure-ftpd instances can be Bind 10.1.1.1,21 and Bind 10.1.1.2,21.
-
-
Load the new instance using /usr/sbin/pure-config.pl <Full path of the config file>
For example: /usr/sbin/pure-config.pl /etc/opt/novell/pureftpd-confs/pure-ftpd1.conf loads an instance using the config file /etc/opt/novell/pureftpd-confs/pure-ftpd1.conf.
Verifying the Load of a New Instance
Use the following methods to verify that the new instance of pure-ftpd is successfully loaded:
-
The ps –eaf | grep pure-ftpd command lists all the instances of pure-ftpd loaded on the system.
-
The PID file as specified using the PIDFile entry in the configuration file has been created.
-
An FTP connection from the client to the server over the IP address being used by the pure-ftpd instance can be created.
Unloading Specific Instances
A new script, pure-ftp-stop.pl, is added to unload an instance of pure-ftpd and all its child processes. The full path of the configuration file used to load the instance of pure-ftpd must be passed to the pure-ftp-stop.pl script.
For example: /usr/sbin/pure-ftpd-stop.pl /etc/opt/novell/pureftpd-confs/pure-ftpd1.conf unloads the instance of pure-ftpd that was loaded using /etc/opt/novell/pureftpd-confs/pure-ftp1.conf.
The PID file of the pure-ftpd instance is also used for unloading the pure-ftpd instance.
Verifying the Unload of a New Instance
-
The PID file specified using the PIDFile entry in the configuration file has been deleted.
-
The number of instances displayed by ps –eaf | grep pure-ftpd is reduced.
-
An FTP connection request to the server errors out.
Pure-FTPd Remote Server Navigation
After logging in to the eDirectory tree, users can access files and directories on a remote Linux server whether or not the server is running Linux FTP Server software. The remote server can be another Linux OES server.
This section describes how to configure and use the Remote Server Navigation feature.
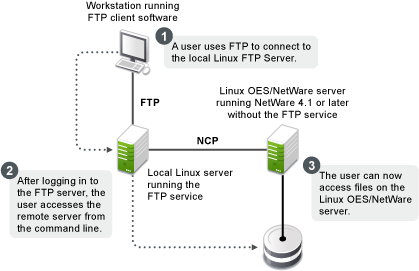
The NCP protocol lets you transfer files and navigate to and from remote OES servers.
To navigate to remote servers, use the following command:
cd //remote server name/volume/directory pathname
File operations such as get, put, and delete can be used on the remote server, even without changing the directory path to that server.
For example:
get //remote_server_name/volume/directory path/filename
The double slash (//) indicates that the user wants to access a remote server. After the double slash, the first entry must be the name of the remote server.
Configuring FTP
Configuration file: /etc/pure-ftpd/pure-ftpd.conf
The configuration parameters for remote server navigation are as follows:
|
Entry |
Value |
Function |
|---|---|---|
|
remote_server |
yes |
Enables remote server navigation for the Pure-FTPd server. |
|
disallow_list_oes_server |
yes |
Disables SITE SLIST command for listing OES machines. |
|
edir_ldap_port |
389 |
eDirectory LDAP port |
The following configuration parameters needs to be set for remote server navigation:
|
Entry |
Value |
Reason Why |
|---|---|---|
|
ChrootEveryone |
no |
Option yes restricts users to login only to his home directory and cannot navigate to other directories including remote OES servers. |
|
AnonymousOnly |
no |
Option yes allows only anonymous logins. |
Path Formats
Table 16-6 Linux FTP Server path formats
|
Task |
Command Format |
|---|---|
|
Specifying the volume and directory path name |
//server_name/volume_name/directory_path |
|
Navigating to different volumes |
cd //server_name/volume_name |
|
Switching back to the home directory |
cd ~ |
|
Switching to home directory of any user |
cd ~user_name |
|
Switching to the root of the server |
/root |
NOTE:The Linux FTP Server does not support wildcards at the root of the server.
SITE Command
The SITE command enables FTP clients to access features specific to the Linux FTP Server.
The SITE command has the following syntax:
SITE [SLIST]
NOTE:The settings done through SITE commands are valid only for the current session.
This command is unique to the Linux FTP service and are not standard FTP commands.
Table 16-7 provides the SITE command along with the description:
Table 16-7 Linux FTP SITE command
|
Command |
Description |
|---|---|
|
SLIST |
Lists all the OES servers within the eDirectory tree. Site list command accepts an eDirectory context in LDAP format. By default, site slist command lists all the NCP Servers in the entire tree. When context is passed to the command it lists all the NCP Servers within the context. |
NOTE:All the FTP users needs to be LUM-enabled on the FTP server.
Disable-ascii
This command is to enable or disable ascii based file transfer. If this is set to YES, all the file transfers are done in a binary mode and the client command 'TYPE A' is ignored.
16.5.7 Cluster Enabling Pure-FTPd in an OES Environment
You can configure Pure-FTPd server in active/active mode of Cluster Services.
Prerequisites
-
Cluster Services is installed and setup.
For step-by-step information on setting up Cluster Services, refer to
Installing, Configuring, and Repairing OES Cluster Services
in theOES Cluster Services for Linux Administration Guide.
Active/Active Mode
In active/active cluster mode, multiple instances of FTP server runs on a single node cluster.
Pure-FTPd must be associated with a shared NSS volume and the DefaultHomeDirectory of users must be on the shared NSS volume.
Configuring Active/Active Mode
-
Install pure-ftpd on all the cluster nodes by selecting OES FTP in the OES install.
-
Enable hard links on the shared NSS volumes. For more information on hard links, see
Hard Links Commands
in theStorage Services File System (NSS) Administration Guide for Linux. -
Create a unique configuration file for every FTP server to be associated with a shared NSS volume. Ensure that:
-
The Bind setting in the configuration file is same as the IP Address of the virtual server created for the NSS pool.
-
The PID file must be unique for each FTP instance running on the cluster.
-
-
Copy the configuration file to the shared volume to /etc/opt/novell on the shared volume. Copying the configuration file to the shared volume, the file is automatically moved across the nodes with the volume and is always available to the FTP Server.
For example: If the shared volume is FTPVol1, the path to copy the configuration file is /media/nss/FTPVol1/etc/opt/novell/pure-ftpd.
-
Configure all the FTP servers for DefaultHomeDirectory support. As NSS volume is shared, the DefaultHomeDirectory in the configuration file must be on the shared volume.
For example: If FTPVol1 is the shared volume attached to an FTP Server, DefaultHomeDirectory in the configuration file is /media/nss/FTPVol1/FTPShare.
-
Update the load and unload scripts of the cluster resource.
-
Load script: Add the following command to load the FTP server with the shared volume:
/usr/sbin/pure-config.pl <Full Path to configuration file>
For example: If the shared volume is FTPVol1 and the Pure-FTP configuration file is /etc/opt/novell/pure-ftpd/ftpvol1.conf on FTPVol1, the pure-ftpd load command in the load script is exit_on_error /usr/sbin/pure-config.pl /media/nss/FTPVol1/etc/opt/novell/pure-ftpd/ftpvol1.conf.
-
Unload script: Add the following command to unload the FTP server:
/usr/sbin/pure-ftpd-stop.pl <Full Path to configuration file>
Configuration file path must be same as the one passed to pure-config.pl in the load script.
-
NOTE:In iManager, load and unload the cluster resources. Pure-ftpd instances must be loaded along with the shared NSS volumes. During the migration process, the pure-ftpd instances alongwith the associated shared volumes are moved across the cluster nodes.
16.5.8 SMB Access for eDirectory Users
By default, eDirectory users access files through NCP protocol. Beginning with OES 2018 SP3, they can also access files through SMB protocol. To do this, enable the entry use_smb_for_edir_users to “yes” in the /etc/pure-ftpd/pure-ftpd.conf on the FTP server.
# Use SMB for remote access by eDirectory users use_smb_for_edir_users yes
Universal Password must be enabled for eDirectory users to access files through SMB protocol.
16.5.9 Migrating Pure-FTPd From NetWare to Linux
You can also migrate an existing FTP server configuration from a NetWare server to OES. For migration instructions and a brief FAQ, see Migrating FTP to OES 24.4
in the Migration Tool Administration Guide.