A.1 NCPCON
The NCP Server Console (ncpcon(8)) is a management utility for NCP Server on Open Enterprise Server. The man page for NCPCON is located in the /usr/share/man/man8 directory. To view the man page when you are at the server console, enter man ncpcon at the terminal console prompt.
-
Section A.1.3, Starting and Stopping NCPCON Interactive Mode
-
Section A.1.11, Managing File System Trustees and Trustee Rights for NCP Volumes
-
Section A.1.13, Renaming a Mount Point Path for a Clustered NSS Volume
-
Section A.1.15, Managing NCP Server Wait Time for Trustee Cache Build
-
Section A.1.16, Purging Deleted Files on NSS Volumes on Linux
-
Section A.1.23, Managing Dynamic Storage Technology on OES Cluster Services for Linux Clusters
A.1.1 Syntax
The NCPCON utility can be used in three modes:
Interactive Mode
Open a terminal console, log in as the root user, then enter
ncpcon
This opens the NCPCON interactive console in the terminal console where you can enter the NCP Server console commands. Enter exit to stop the interactive mode.
Command Line Mode
For command line mode, issue an NCP Server command at a terminal console prompt by prefacing the command with ncpcon:
ncpcon [command]
For example:
ncpcon mount sys
Escaping the quote character is not required when entering the command from the NCPCON prompt or console command prompt. For example, the send command is entered as follows from the NCPCON prompt:
send "hello world" to all
For example, the send command is entered as follows from the console command prompt:
ncpcon send "hello world" to all
Scripting Mode
For scripting mode, if the file path or trustee name contains space, enclose them with double quotation marks:
ncpcon "[command]"
For example:
ncpcon rights add vol1:"dir 1/dir2" "test user.novell" rwcmef ncpcon rights add "vol1:dir 1/dir2" "test user.novell" rwcmef
It's optional to use double quotation marks if the file path or trustee name does not contain space.
For example:
ncpcon rights add vol1:dir1/dir2 testuser.novell rwcmef ncpcon rights add "vol1:dir1/dir2" "testuser.novell" rwcmef
A.1.2 Getting Help
- help [command]
-
Use this command to list the NCPCON console commands. To get specific help for a command, type help and the command.
Examples
help
help mount
help remove volume
A.1.3 Starting and Stopping NCPCON Interactive Mode
- ncpcon
-
Use this command to start the NCPCON interactive mode.
Example
ncpcon
- exit
-
Use this command to exit the NCPCON application when you are in the interactive mode. The command is not used in the command line/scripting mode.
Example
exit
A.1.4 Monitoring NCP Server
Use the commands in this section to manage the NCP Server service on your OES server.
- config
-
Displays the NCP Server configuration information such as the server name, server version, product version, NCP version, mixed-mode paths status (yes/no), and commit files status (yes/no).
Example
config
- stats
-
Use this command to display NCP statistics, including the following:
-
Server up time
-
Packets in
-
Packets dumped
-
Packet receive buffer memory
-
Packet reply buffer memory
-
NCP requests
-
NCP connections in use
-
Connection table memory
-
Mounted volumes
-
Number of open files
-
Local ID tracking
-
File handle memory
-
Volume SYS: file and subdirectory caching memory
-
Volume SYS: trustee and inherited rights mask tracking memory
Example
stats
-
- version
-
This command displays version information for all currently running OES NCP Server components, the OES build, and the hardware platform.
Example
version
- set
-
Use this command to view or set current NCP server system parameters.
Example
set
A.1.5 Managing NCP Server in a Cluster
NCPCON supports the bind and unbind commands for use with OES Cluster Services for Linux on an OES server.
Use these commands in load or unload scripts when you want to configure the NCP access for files in a cluster resource that can be moved or failed over to another node in the cluster. NCP is required for NSS volumes, NCP volumes on Linux POSIX file systems, and Dynamic Storage Technology shadow volumes.
SLP must be configured on the server where the bind command is issued. When the SLP daemon (slpd) is not installed and running on a cluster node, any cluster resource that contains the ncpcon bind command goes comatose when it is migrated or failed over to the node because the bind cannot be executed without SLP. For more information on software requirements for SLP for cluster services, see SLP
in the OES 23.4: OES Cluster Services for Linux Administration Guide
.
For information about configuring and managing OES Cluster Services for Linux, see the OES 23.4: OES Cluster Services for Linux Administration Guide.
- bind cluster_resource_name ip_address
-
Binds the specified cluster resource name. Use this command to assign an IP address to the NCP Server cluster resource name.
Example
bind oes_11_cluster 192.168.1.1
In a cluster load script, use the following syntax:
exit_on_error ncpcon bind --ncpservername=oes_11_cluster --ipaddress=192.168.1.1
- unbind cluster_resource_name ip_address
-
Unbinds the specified cluster resource name. Use this command to remove the assignment of an IP address from the NCP Server cluster resource name.
Example
unbind oes_11_cluster 192.168.1.1
In a cluster unload script, use the following syntax:
ignore_error ncpcon unbind --ncpservername=oes_11_cluster --ipaddress=192.168.1.1
A.1.6 Managing NCP Threads
Use the commands in this section to configure the number of concurrent NCP threads and to verify the current NCP utilization.
- nncpcon set NCP_CPU_AFFINITY=<value>
-
This parameter indicates whether CPU affinity is enabled for NCP.
The administrator can enable CPU Affinity by considering other services hosted on the same system. On an OES system when the other file access protocol like CIFS and other services like GroupWise, DNS, DHCP, or iManager reduces the number of CPUs available to other services. The CPU affinity is applied to SSG threads in NCP Server for improving the encryption performance. When the Enabling CPU affinity, NCP will reserve 50% of system CPUs.
NOTE:To enable CPU Affinity, the number of system CPUs must be four or more.
For example, the total number of CPUs are 16, then 8 CPUs will be used with 8 Fixed SSG threads (by bringing down from fixed 40 number of SSG threads).
To enable this feature, set NCP_CPU_AFFINITY=1 from ncpcon and restart the ndsd. CPU Affinity has to be enabled on OES servers and used as a file server without enabling other services like DNS, DHCP, and Doing this, it is ensured that other services are not starved of CPUs.
Default: 0, Valid Values: 0 and 1.
- ncpcon set NCP_BYTE_RANGE_LOCK_SPIN_TIME=<value>
-
The value ranges between 0 to 5000 in milliseconds. This avoids the lock collision when the LockTimeout is sent as 0 in a Byte Range Request from the client
- ncpcon set ADDITIONAL_SSG_THREADS=<value>
-
Sets the number of additional SSG threads (above the fixed 25 NCP threads) that can be used to serve incoming NCP file service requests. These threads are used when the fixed 25 NCP threads are busy and taking more than expected time to finish.
Default: 25. Valid Range: 7 to 103.
- ncpcon set CONCURRENT_ASYNC_REQUESTS=<value>
-
Sets the maximum number of the Async eDirectory NCP request threads that can be created. Default: 50. Valid Range: 25 to 384.
- ncpcon threads
-
Allows you to verify the current number of concurrent NCP threads running on the server. Use this command to verify the settings that you make for the ADDITIONAL_SSG_THREADS and CONCURRENT_ASYNC_REQUESTS settings.
Example - NCP SSG Thread Statistics
Total Number of Active SSG Threads: 13 Max Number of Additional SSG Threads (over and above fixed 25 NCP Threads): 12 Total Number of NCP Streams: 20 Current Average Load per Thread: 1.54 Peak Number of Active SSG Threads: 25 Peak Number of NCP Streams: 2148 Peak Average Load per Thread: 85.92
Total Number of Active SSG Threads: The currently active SSG threads.
Max Number of Additional SSG Threads (above the fixed 25 NCP threads): When all 25 fixed SSG threads are exhausted, this number defines the additional number of threads that can be created to serve other incoming NCP file service requests. This value can be modified by using the ncpcon set ADDITIONAL_SSG_THREADS=value command. Default=25. Valid Range: 7 to 103.
Total Number of NCP Streams: The current number of NCP connections that have been handled by the Active SSG threads.
Current Average Load per Thread: The current average load of NCP connections on the Active SSG threads.
Peak Number of Active SSG Threads: The highest number (peak) of the Active SSG threads.
Peak Number of NCP Streams: The highest number (peak) of NCP streams.
Peak Average Load per Thread: The highest number (peak) of streams per thread.
Example - Async (eDir) Threads and Requests Statistics
Number of Running Threads: 0 Max Thread Size: 25 Thread Peak Size: 25 Number of Queued Requests: 0 Queued Requests Peak Size: 174
Number of Running Threads: The currently running number of Async threads that can handle eDirectory requests.
Max Thread Size: The maximum number of the Async threads that can be created. This value can be modified by using the ncpcon set CONCURRENT_ASYNC_REQUESTS=value command. Default: 50. Valid Range: 25 to 384.
Thread Peak Size: The highest number (peak) of Async threads the server required so far. This number is reset when the service is restarted.
Number of Queued Requests: The number of queued eDirectory requests (after the Async threads are exhausted).
Queued Requests Peak Size: The highest number (peak) of eDirectory requests that have been queued so far (after the Async threads are exhausted).
A.1.7 Displaying NCP Volume Information
- volumes
-
Use this command to print information about mounted volumes.
Examples:
ncpcon volumes
This command displays a list of currently mounted NCP volumes.
ncpcon volume volume_name
This command displays details of the specified volume.
ncpcon volumes /v
This command displays a list of currently mounted NCP volumes along with the NCP volume IDs.
ncpcon volumes /s
Displays volume size details.
A.1.8 Managing Audit Settings
- ncpcon set AUDITING_SUPPORT=<value>
-
This parameter indicates whether auditing support is enabled for NCP. The default value is 0 and it indicates that auditing is turned off.
Default: 0. Valid Values: 0 and 1.
A.1.9 Managing Log Settings
- ncpcon set LOG_LOCK_STATISTICS=<value>
-
When an NCP volume lock is held more than the configured time, NCP server displays a message in the ncpserv.log file with the relevant details.
Default: 0. Valid Values: 0 to 10000 msec.
A.1.10 Managing NCP Volumes
Use the commands in this section to create, manage, or remove NCP volumes for Ext3 and Reiser file systems on your OES Linux server. NCP volumes use the OES Trustee Model for controlling user access to files. Users access the volume by using the Client for Open Enterprise Server.
- change volume ncp_volname [option]
-
Display the current volume options setting for the specified volume, or change the setting for a specified option on the specified volume. Issuing the command is a toggle for the setting, turning it on or off, depending on its current value.You must dismount the volume before you can change its options settings with this command.
This command cannot be added to a cluster load script.
Option
- Inherit_POSIX_Permissions <on|off>
-
This is disabled by default. When this setting is disabled, only the root user and the owner of the file can access the volume as local users in a Linux environment. Disabling the POSIX inheritance is the most secure setting because NCP volumes use the OES Trustee Model for file system access control.
If this option is enabled on a volume, the POSIX permissions are permitted to be inherited from parent directories. If POSIX inheritance is enabled, local access in the Linux environment by users who are not authenticated via NetIQ eDirectory can create security problems.
Examples
To view the current setting, enter the following at the console command prompt:
ncpcon change volume sys
To enable Inherit POSIX Permissions on the sys: volume, start NCPCON by entering ncpcon at the console command prompt, then enter the following at the ncpcon prompt:
dismount sys
change volume sys Inherit_POSIX_Permissions on
mount sys
exit
- create volume ncp_volumename path
-
Use this command to create an NCP volume by defining an NCP share on an existing POSIX file system on your Linux server. This command creates a Volume object in NetIQ eDirectory, and associates the volume name to a path on your server when using file system types other than the Storage Services (NSS) file system.
This command does not remove or delete data in the mount point location. It adds the NCP volume’s volume name and mount information to the NCP Server configuration file (/etc/opt/novell/ncpserv.conf).
Replace ncp_volumename with the name for the volume.
Replace path with the path to an existing folder on the Linux server that is used as the mount point for the NCP volume. The folder must be on a Linux POSIX file system volume.
After creating the NCP volume, you must mount it to make it accessible to NCP clients.
Example
create volume vol1 /media/ncpvolumes/vol1
- dismount <ncp_volumename | all>
-
Use this command to dismount a specified NCP volume on your Linux server, or to dismount all NCP volumes on your Linux server.
Examples
To dismount the NCP volume named VOL1, enter
dismount VOL1
To dismount all NCP volumes, enter
dismount all
- mmount < all | volumename | volumename=volume_id,path=/volume_mntpoint >
-
Use this command to mount an NCP volume on your Linux server. This command makes the NCP volume accessible to NCP clients.
Replace volumename with the name of the volume, such as VOL1. To mount all volumes, replace the volume name with all.
Replace volume_id with a value from 0 to 254 as the server volume ID. It is not necessary to manually specify a volume ID for a locally mounted volume. NCP automatically assigns unique volume IDs to locally mounted NCP volumes and NSS volumes in increasing order, from 0 to 254. IDs 0 and 1 are reserved for the sys and _admin volumes. When the command is used in a cluster resource script, the volume ID must be specified to ensure that the volume ID is unique across all cluster nodes where the volume will be mounted. By convention in clusters, the volume IDs are assigned in decreasing order, from 254 to 0.
For an NCP volume created on a Linux POSIX file system, replace /volume_mntpoint with the Linux path of the mount point for the NCP share. Typically, this path is mount point of the Linux volume; that is, the share is created at the root of the Linux volume.
If an NCP volume is mounted locally, the mount path is stored in the /etc/fstab file, so it is not necessary to specify a mount path. For example:
ncpcon mount VOL1
The mount path for the NCP volume is required in a cluster resource. For example, if you use NSSMU to create and NCP enable a clustered Linux LVM volume 'myvol' with a mount point of /usr/novell/myvol, the NCP volume name (share name) is MYVOL, and the resource load script includes the following definitions for variables used in the command:
# define the mount point path of the Linux volume
MOUNT_PATH=/usr/novell/myvol
# define the NCP volume name
NCP_VOLUME=MYVOL
exit_on_error ncpcon mount $NCP_VOL=253,path=$MOUNT_PATH
For an NSS volume, the default mount path is /media/nss/<nss_volume_name>. For example, if you create a volume named USERS, the default mount path is /media/nss/USERS. If you use the default path for NSS volumes, it is not necessary to include the path option for local mounts:
ncpcon mount USERS
A volume ID must be specified in a cluster load script:
exit_on_error ncpcon mount USERS=252
In a cluster, you cannot rename the mount point path. The default mount point path of /media/nss/<volume_name> applies.
exit_on_error ncpcon mount volumename=volume_ID
For example:
exit_on_error ncpcon mount USERS=252
The volume is mounted at /media/nss/USERS.
- remove volume ncp_volumename
-
Use this command to remove the NCP volume and path association. This command does not remove or delete data from the mount location. This command removes the NCP volume mount information from /etc/opt/novell/ncpserv.conf configuration file.
Example
remove volume VOL1
- volumes, volume volumename
-
Displays a list of currently mounted NCP volumes. You can also specify a specific volume name with the command to get information about that volume.
Examples
volumes
volume VOL1
- volume data
-
Displays a list of currently mounted NCP volumes and information about them. For example, if the volume is a Dynamic Storage Technology shadow volume pair, it identifies the Linux paths of its primary and secondary volumes.
Example
volume data
- disable write <volume name> [Broadcast message]
-
This command disables write permission on files in the specified volume. The broadcast message is optional, but if any message is sent to all the clients accessing the specified volume.
NOTE:Executing this command closes any files that are opened for writing.
Example
disable write VOL1 Closing all open files on this volume.
- enable write <volume name> [Broadcast message]
-
Use this command to enable write permissions on a volume that has been previously disabled for writing by using the disable write command.
The broadcast message is optional, but if any message is sent to all the clients accessing the specified volume.
Example
enable write VOL1 Files on this volume can now be edited.
A.1.11 Managing File System Trustees and Trustee Rights for NCP Volumes
Use the commands in this section to manage file system trustees and trustee rights for NCP volumes for Linux POSIX file systems on your OES server. NCP volumes use the OES Trustee Model for controlling user access to files.
- rights <view path | add path fdn options | remove path fdn>
-
Allows you to view, add, or remove trustees and trustee rights for a specified path. Replace fdn with the typeless fully distinguished name (username.context) of the trustee, such as bob.example. Replace options with all, none, or the combination of rights to assign for the specified trustee. List the rights together without spaces or commas, such as RF. If the file path or trustee names contain spaces, ensure to enclose them within double or single quotes. For visibility, users need the Read and File Scan rights.
Options
- all
-
All rights
- none
-
No rights
- S
-
Supervisor
- R
-
Read
- W
-
Write
- C
-
Create
- E
-
Erase
- M
-
Modify
- F
-
File scan
- A
-
Access control
Examples
rights view sys:login
rights view "vol1:login dir1/dir2"
rights view "vol1:/login/dir 1/", rights view 'vol1:/login/dir 1/'
rights add users:bob bob.example RF
rights add "vol1:dir 1" bob.example RF
rights add "vol1:dir1" "bob christo.example" RF
rights add "vol1:dir 1" "bob christo.example" RF, rights add 'vol1:dir 1' 'bob christo.example' RF
rights remove users:bob bob:example
rights remove "vol1:dir 1" bob.example
rights remove vol1:dir1 "bob christo.example"
rights remove "vol1:dir 1" "bob christo.example", rights remove 'vol1:dir 1' 'bob christo.example'
- irm <view path | set path mask>
-
Displays or sets the inherited rights mask on the specified path. Specify both the NCP volume and directory in the NetWare path format, such as volname:dir1/dir2. Replace mask with the mask options all, none, or the combination of rights to block from being inherited. List the rights together without spaces or commas, such as SAE. If the file path or trustee names contain spaces, ensure to enclose them within double or single quotes.
MASK OPTIONS
- all
-
All rights
- none
-
No rights
- S
-
Supervisor
- R
-
Read
- W
-
Write
- C
-
Create
- E
-
Erase
- M
-
Modify
- F
-
File scan
- A
-
Access control
Examples
irm view sys:login
irm view "vol1:login dir1/dir2"
irm view "vol1:/login/dir 1/", irm view 'vol1:/login/dir 1/'
irm set vol1: SA
irm set vol1:dir1 RF
irm set "vol1:dir 1/dir 2" RF, irm set 'vol1:dir 1/dir 2' RF
A.1.12 Managing NSS Volumes in a Cluster
Use the following load script to mount NSS volumes in a cluster resource.
ncpcon mount <VOLUMENAME>=<VOLUMEID> ncpcon mount /opt=ns=LONG <VOLUMENAME>=<VOLUMEID> ncpcon mount /opt=ns=UNIX <VOLUMENAME>=<VOLUMEID>
A.1.13 Renaming a Mount Point Path for a Clustered NSS Volume
You can modify the load and unload scripts to specify a non-standard mountpoint path for a clustered NSS volume. It requires using Linux commands in the scripts. For instructions, see Renaming the Mount Point Path for a Shared NSS Volume (Using a Custom Mount Point for a Shared NSS Volume) in the OES 23.4: OES Cluster Services for Linux Administration Guide.
A.1.14 Managing TCP Connections
This parameter allows you to configure the keep-alive timeout for all the TCP client connections accepted by the NCP server. Based on this parameter, the TCP keep-alive packet is sent by the server if the client is inactive for the configured amount of time.
This parameter also helps the NCP server to clear unwanted connections. The actual time taken to clear the unwanted NCP connections also depends on other system-wide TCP keep-alive parameters, like net.ipv4.tcp_keepalive_probes and net.ipv4.tcp_keepalive_intv.These parameters can be controlled using the sysctl command.
ncpcon set NCP_TCP_KEEPALIVE_INTERVAL=<value>
Default: 8 minutes. Valid Range: 3 minutes to 240 minutes.
A.1.15 Managing NCP Server Wait Time for Trustee Cache Build
This parameter allows you to configure the time in seconds that the NCP server waits for the completion of trustee cache build during volume mount. If trustee cache build takes a longer time, NCP server does not wait any longer than this configured time and continues with further activities of volume mount.
If the parameter is set to a lower value, the volume mount may complete faster but the users accessing the data on that volume may experience access failure. Because, the trustee cache build is not complete yet.
If the parameter is set to a higher value, the volume mount may take a longer time to complete but the users are unlikely to experience access failure on accessing the data on that volume. Because, the trustee cache build would be complete by the time the volume mounts.
In your environment if only CIFS is used for file access and not NCP, you can set this parameter to 1 so that the volume mount is completed faster. The users do not experience any access failure too.
This parameter can be helpful in reducing the time taken for a cluster resource migration.
ncpcon set NCP_TRUSTEE_BUILD_WAIT_TIME=<value>
Default: 7 seconds, Valid Range: 1 second to 30 seconds.
A.1.16 Purging Deleted Files on NSS Volumes on Linux
- purge volume nss_volumename
-
Use this command to purge or permanently remove deleted files from an NSS volume on Linux. This command works only with NSS volumes where the Salvage attribute has been previously enabled.
Example
purge volume vol1
A.1.17 Managing User Login
Use the commands in this section to enable or disable login for NCP clients to the Linux server.
- disable login
-
Use this command to prevent NCP clients from logging in to the Linux server.
Example
disable login
- enable login
-
Use this command to allow NCP clients to log in to the Linux server.
Example
enable login
A.1.18 Sending Messages to Logged-In Users
- send "text_message" to <station | station1,station2... | all>
-
Use this command to send a message to logged-in NCP clients. Replace text_message with a message of up to 252 characters and spaces. Specify multiple logged-in stations by separating the connection numbers with commas and no spaces. Specify all to send the message to all logged-in users.
To find the connection number assigned to a user’s connection, use the connection commands in Section A.1.19, Managing NCP Server Connections.
Example
To issue the command at the ncpcon prompt:
send "Hello, world" to 1 send "Hello, world" to 1,2,4 send "Hello, world" to all
To issue the command at the terminal console prompt:
ncpcon send "Hello, world" to 1 ncpcon send "Hello, world" to 1,2,4 ncpcon send "Hello, world" to all
A.1.19 Managing NCP Server Connections
Use the connection commands in this section to display the NCP Server connection information for all current connections, or for a given connection. You can also display a list of the connections and clear the connections. The general syntax is:
connection [list | connection_number | clear connection_number | clearALL except connection_number]
- connection
-
Displays an overview of current NCP Server connection information.
Parameter
Description
Connection Slots Allocated
Displays the number of slots currently allocated for use. As connection slots are required on this server that exceed the current number of slots displayed here, new slots are allocated.
Depending on the server’s memory, connection slots are usually allocated in blocks of 16. Connection slots are allocated as needed by users and other services.
Connection Slots Being Used
Displays the number of connection slots currently in use. As this number matches or exceeds the Connection Slots Allocated entry, more connection slots are allocated to the connection table.
Signing Level
Displays the level at which NCP packet signature signing is set on the server. NCP packet signatures prevent packet forgery by requiring the server and the workstation to sign each NCP packet. A higher packet signature number impacts the performance of your server. At some point, the need for security might outweigh certain performance issues.
Login State
Displays whether users are allowed to log in to the server.
To disable users from being able to log in to the server (for server maintenance or other reasons), enter disable login at the NCPCON prompt, or enter ncpcon disable login at a terminal console prompt.
To allow users to log in to the server, enter enable login at the NCPCON prompt, or enter ncpcon enable login at a terminal console prompt.
Licensed Connections
Displays the number of connections that are currently licensed. Licensed connections are authenticated, logged in, and consume a license. An unlicensed connection does not consume a license and can be authenticated or not. An unlicensed, authenticated connection can access the eDirectory database but cannot access any other resources.
Not Logged In Connections
Clears all user connections that are open, but not currently authenticated to the server.
Use this parameter to clear all user that are not logged in.
Example
connection
- connection list
-
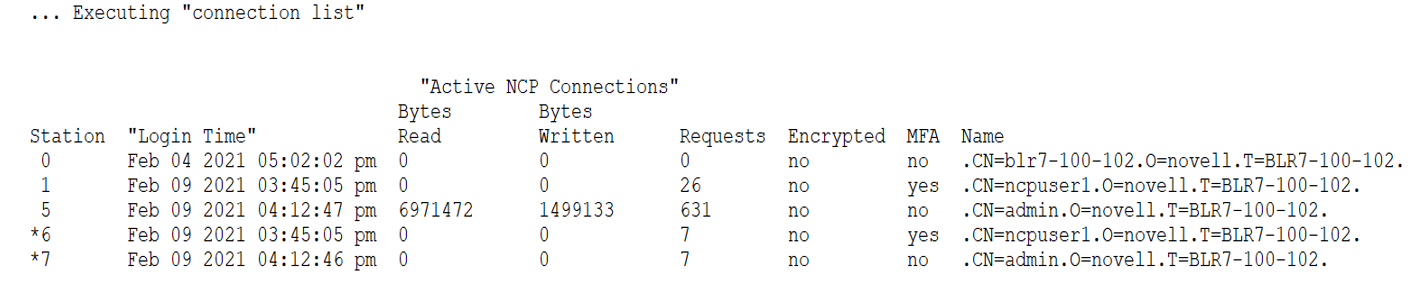
Displays a list of all current NCP Server connections along with connection type information.
The general syntax for the ncpcon connection list command is:
connection list [/m | /e | /n]
Operations: Only one option at a time can be used with connection list. For example, connection list /m.
- /m
-
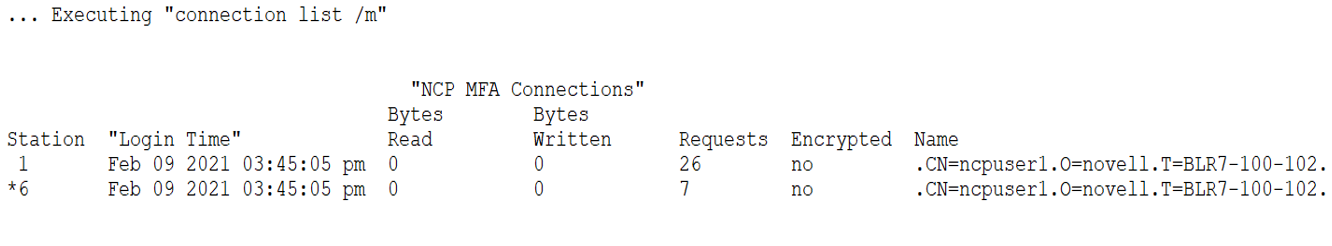
Displays a list of Multi-factor Authentication (MFA) NCP connections including MFA encrypted and MFA non-encrypted connections.
- /e
-
Displays a list of encrypted NCP connections including MFA encrypted and non-MFA encrypted connections.
- /n
-
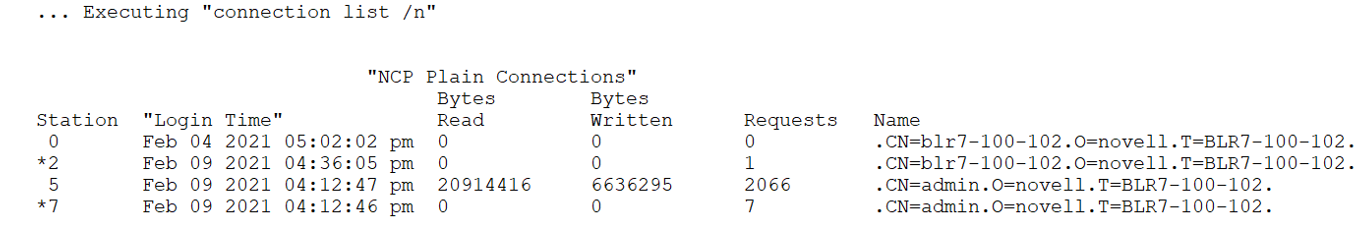
Displays a list of non-MFA and non-encrypted NCP connections.
Parameter
Description
Station
Shows the connection number for each connection. Connection 0 is the connection used by the server. The server’s operating system uses connection numbers to control each station’s communication with other stations. Remote Manager does not distinguish connections that don’t count against the server’s connection limit.
Login Time
Shows the login day, date, and time for the connection.
Reads & Writes
Shows the number of reads and writes (in bytes) made by the connection.
Requests
Shows the number of NCP requests made by the connection.
Name
Shows the name of the user, server, service, or login status and links to specific information about that user connection such as the login time, connection number, network address, login status, number of NCP requests, files in use, and security equivalence.
Connections with an asterisk (*) displayed next to the name indicate an unlicensed connection (it does not consume a license). These licenses can be either authenticated or not authenticated. An unlicensed, authenticated connection can access the NetIQ eDirectory database but not other server resources.
From this detailed Connection Information page, you can also clear the connection or send a message to the user.
Encrypted
Shows the encryption status of the connection. If "yes" the connection is encrypted and "no" then the connection is not encrypted.
MFA
Shows whether the connection is enabled for MFA. If "yes" the connection is MFA and "no" then the connection is non-MFA.
Example
connection list /m
connection list /e

connection list /n
connection list
- connection list /h
-
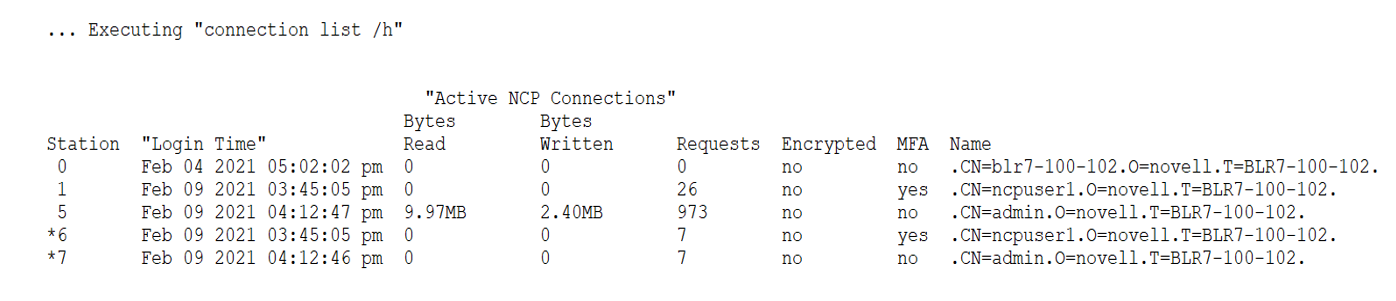
The switch /h interprets the number of bytes read or written in human readable format, that is, KB/MB/GB based on the size.
Examples
connection list /h
- connection connection_number
-
Displays detailed information about a specified NCP Server connection. Replace connection_number with the station of interest. You can find the station’s connection number from the report displayed by issuing the connection list command.
Parameter
Description
Connection Number
The station number for the connection.
Authentication Method
Shows the authentication method used if the connection is logged in.
Login Time
Shows the login day, date, and time for the connection.
Encrypted
Shows the encryption status of the connection. If "yes" the connection is encrypted and "no" then the connection is not encrypted.
MFA
Shows whether the connection is enabled for MFA. If "yes" the connection is MFA and "no" then the connection is non-MFA.
Privileges
Shows whether the connection has privileges, such as Supervisor or Console Operator.
Connection Type
Shows whether the connection is internal or external.
Bytes Read
Shows the total number of reads made by the connection.
Bytes Written
Shows the total number of writes made by the connection.
NCP Requests
Shows the total number of NCP requests made by the connection.
IP Address
Shows the IP address where the connection originates.
Open Files
Shows the files open for the connection.
Security Equivalence
Shows the name of the user, server, or service if it is logged in.
Example
connection 1
- connection clear connection_number
-
Clears the NCP Server connection for a specified station. Replace connection_number with the station of interest. You can find the station’s connection number from the report displayed by issuing the connection list command.
Example
connection clear 1
- connection clearALL, connection clearALL except <connection_number>
-
These parameters help the NCP server to clear all user connections that are open. You can optionally specify connection numbers that you do not want to close in the exception list. NCP server exempts those connections from closing. Specify multiple connection numbers by separating them with commas.
- clearALL except <connection_number>
-
This command will clear all connections except:
-
Connections that are mentioned in the exception list.
-
NCP server object connections.
-
Not Logged In connections (User connections that are open, but not currently authenticated to the server).
Even if you clear user connections using this command, connections get reestablished automatically. To use this command effectively, first disable users from being able to log in to the server, enter disable login at the NCPCON prompt, or enter ncpcon disable login at a terminal console prompt.
IMPORTANT:Use this command prudently. Otherwise, it might lead to unexpected complications.
Examples
To issue the command at the NCPCON prompt:
connection clearALL connection clearALL except 1 connection clearALL except 1,2
To issue the command at a terminal console prompt:
ncpcon connection clearALL ncpcon connection clearALL except 1 ncpcon connection clearALL except 1,2
-
A.1.20 Managing NCP Security Configurations
Encryption and MFA enforcements on NCP servers allow security settings to be configured at the volume, path, and cluster resource levels. The NCP security options behave consistently across the tree and must be configured on all servers.
Grace Time option is introduced to gracefully terminate the non-encrypted connections. Grace time is not enforced at the volume, path, or cluster resource levels, but it is enforced at the server level. This eliminates data loss due to ungraceful file closures when the connections are closed. Established connections are secure, if encryption and multi-factor authentication (MFA) are enforced at the server level.
Data access is not terminated on unencrypted or non-MFA connections, however clear connections on encryption/MFA enforced channels are blocked. If all data in the enterprise requires an encrypted channel, enforce it at the server level. If only a portion of the data set requires encryption, enable it at the server level and enforce it at the volume or path level. Both encrypted and unencrypted connections are allowed.
MFA and encryption are applied on NSS volumes only.
NOTE:Beginning with OES 2018 SP3, NCP server-level encryption is enabled by default, and TLSv1.2 is supported. In OES 23.4, the encrypted connection between client and server supports both TLSv1.2 and TLSv1.3.
NCP Security Configurations for Encryption
The encryption capability on NCP servers allows the client to establish a secure connection between the client and the server. The Client for Open Enterprise Server not having the encryption capability are blocked and connections originating from such clients are shutdown.
- security encrypt <enable | disable | enforce>
-
Use this command to enable, disable, or enforce encryption of file system communication on the NCP server.
Operation Options
- enable
-
Enables the encryption capability on the NCP server to establish a secure channel when the client is also encryption enabled. The clients without encryption (Clients older than Client for Open Enterprise Server 2 SP5) also can access files through unencrypted connection.
- disable
-
Disables the encryption capability on the NCP server. The client and server establishes a non-secure channel.
- enforce
-
Enforces the encryption capability on the NCP server. This forces the clients to establish a secured channel with the server even if the client is not encryption enabled. This option is applicable only to file service requests and the drive mapping fails from non-encrypted Client for Open Enterprise Server.
IMPORTANT:Setting this option pulls down any unencrypted connections (existing or new) that sends the file service request. This in-turn may cause data loss if there are any open files on those connections.
During the grace period, encrypted or non encrypted connections are allowed based on the previous state. Once the grace period is over it will be in the enforced state.
Grace time option is applied only on changing state from:
-
Enable to Enforce
-
Disable to Enforce
Grace time should be specified in the range of 0 to 72 hrs.
-
NOTE:The send file support is not available when encryption is enabled or enforced. That is, setting SENDFILE_SUPPORT=1 with encryption enabled or enforced does not have any impact. Hence, it is recommended to set SENDFILE_SUPPORT=0, when encryption is enabled or enforced. Although for non-encrypted connections (with encryption disabled), SENDFILE_SUPPORT=1 will still be effective.
Syntax
To issue the command at the NCPCON prompt:
security encrypt enable
To issue the command at a terminal console prompt:
ncpcon security encrypt enable
- security cipher-strength <low | medium | high>
-
Use this command to set the cipher’s ability to protect the data transmitted over the network. This is applicable when the encryption is enabled or enforced. This command at the cluster resource level individually enables or enforces encryption for all the volumes of cluster resources.
Operation Options
- low
-
Sets the message authenticity security level to 64 bits or more. Key size limited to 128 bits cipher.
- medium
-
Sets the message authenticity security level to 80 bits or more. Key size is 128 bits or more.
- high
-
Sets the message authenticity security level to 128 bits or more. Key size is 256 bit but due to the limitation of the TLS protocol the overall security level is 192 bits.
- Syntax
security cipher-strength high
NCP Security Configurations for Enforcing MFA
The MFA capabilities on NCP servers allow the client (Client for Open Enterprise Server 2 SP5 or later) and the servers to establish a secure channel when Advanced Authentication is enabled. Multi-factor authentication support through Advanced Authentication Service integration.
- security Enforce-MFA <yes | no>
-
Use this command to enforce Multi-factor Authentication (MFA) capability on the NCP server.
Operation Options
- yes
-
Enforces the MFA capability on the NCP server. The earlier Client for Open Enterprise Server even though having Advanced Authentication capability are blocked and connections originating from such clients are shutdown. This option is applicable only to file service requests and the drive mapping fails from non-MFA Client for Open Enterprise Server.
- no
-
Disables the multi-factor authentication capability on the NCP server. The clients with or without Advanced Authentication establishes connection with the server and the file service requests continue as usual.
- security enforce </e | /m | /em> </a |/r> <volume-name | path |cluster-resource- name>
-
Use this command at volume level or path level and at cluster level on the NCP server individually to enable or enforce MFA for all the volumes of cluster resources.
During the grace period, MFA or non-MFA connections are allowed based on the previous state. Once the grace period is over it will be in the enforced state.
Grace time option is applied only on changing state from:
-
No to Enforce
Grace time should be specified in the range of 0 to 72 hrs.
NOTE:
-
To enforce encryption at a volume or path level the encryption must be enabled at server level. Encryption at server level is by default enabled in OES 23.4.
-
To enforce MFA at volume or path level the MFA capability must not be enforced at the server level. Both authenticated and non-authenticated connections are allowed if MFA is not enforced at the server level. This is by default not enforced at the server level.
-
Grace time feature is not available on enabling security enforce option.
-
If the Enforced/MFA folder is deleted from Client for OES, then the enforced/MFA setting on the folder gets revoked. On salvage operation, an administrator has to explicitly enforce the folder. Else the non-encryption/non-MFA clients will be able to access the enforced folder.
-
Security enforcement cannot be applied on SYS volume.
Operations
- /e /a
-
Enforces encryption on the volume/ cluster volume or path. On enforcing, only encrypted clients are able to access or perform file operations on the specified volume or path.
- /e /r
-
Encryption is no longer enforced on the volume/cluster volume or path. Encrypted and non-encrypted clients are able to access or perform file operations on the specified volume or path.
- /m /a
-
Enforces MFA on the volume/cluster volume or path. On enforcing, only MFA enabled clients are able to access or perform file operations on the specified volume or path.
- /m /r
-
MFA is no longer enforced on the volume/cluster volume or path. MFA and non-MFA enabled clients are able to access or perform file operations on the specified volume or path.
- /em /a
-
Enforces encryption and MFA on the volume/cluster volume or path. On enforcing, only encrypted and MFA enabled clients are able to access or perform file operations on the specified volume/cluster volume or path. Both /em or /me option can be used.
- /em /r
-
Encryption or MFA is no longer enforced on the volume/cluster volume or path. All clients are able to access or perform file operations on the specified volume or path. Both /em or /me option can be used.
NOTE:On enforcing MFA/encryption using cluster resource name, all the volumes under that resource are enforced. If volume /path is given, MFA/encryption is enforced only on a single volume/path. If cluster resource name is given, MFA/encryption is enforced on all the volumes under that cluster resource.
-
- Examples
-
# ncpcon security enforce /e /a VOL1:FOL1 VOL1:FOL2
Encryption is enforced on folders FOL1 and FOL2. Only encrypted clients can now access these folders.
If the same command is executed again or if the volume or folder is already enabled for enforcement, then a message, “Encryption is not enforced on Volumes or Directories: VOL1/FOL1, VOL1/FOL2” is displayed. Run the command security view to verify if the volumes or folders are already enforced.
# ncpcon security enforce /e /a VOL1:JUNCTION1
Encryption is enforced on the DFS junction. If the DFS junction source is enforced then access to the target is blocked.
- security view
-
Use this command to view the current security configurations on the NCP server.
- Syntax
-
To issue the command at the NCPCON prompt:
security Enforce-MFA yes security enforce /e /a <VOL1> <VOL1:fldr1/fldr2> <cluster-resource-name>security enforce /e /r <VOL1> <VOL1:fldr1/fldr2> <cluster-resource-name> security enforce /m /a <VOL1> <VOL1:fldr1/fldr2> <cluster-resource-name> security enforce /m /r <VOL1> <VOL1:fldr1/fldr2> <cluster-resource-name> security enforce /em /a <VOL1> <VOL1:fldr1/fldr2> <cluster-resource-name> security enforce /em /r <VOL1> <VOL1:fldr1/fldr2> <cluster-resource-name> security view <VOL1> <VOL1:fldr1/fldr2> <cluster-resource-name>
For enforcing security on all the volumes under a cluster resource, syntax is followed by resource name.
security enforce /e /a <VOL1> <VOL1:fldr1/fldr2> <cluster-resource-name>
If the admin wants to enforce on a single cluster volume, then the syntax is the same as volume level enforcement.
security enforce /e /a <VOL1> <VOL1:fldr1/fldr2> <cluster-volume-name>
To issue the command at a terminal console prompt:
ncpcon security encrypt enable ncpcon security cipher-strength high ncpcon security Enforce-MFA yes ncpcon security enforce /e /a <VOL1> <VOL1:fldr1/fldr2> <cluster-volume-name> ncpcon security enforce /e /r <VOL1> <VOL1:fldr1/fldr2> <cluster-volume-name> ncpcon security enforce /m /a <VOL1> <VOL1:fldr1/fldr2> <cluster-volume-name> ncpcon security enforce /m /r <VOL1> <VOL1:fldr1/fldr2> <cluster-volume-name> ncpcon security enforce /em /a <VOL1> <VOL1:fldr1/fldr2> <cluster-volume-name> ncpcon security enforce /em /r <VOL1> <VOL1:fldr1/fldr2> <cluster-volume-name> ncpcon security view <VOL1> <VOL1:fldr1/fldr2> <cluster-volume-name>
Examples
- # ncpcon security enforce /m /a VOL1:FOL1 VOL1:FOL2
-
MFA is enforced on folders FOL1 and FOL2. Only MFA-enabled clients can now access these folders.
If the same command is executed again or if the volume or folder is already enabled for enforcement, then a message, “MFA is not enforced on Volumes or Directories: VOL1/FOL1, VOL1/FOL2” is displayed. Run the command security view to verify if the volumes or folders are already enforced.
- # ncpcon security enforce /em /r VOL1:FOL2
-
Encryption and MFA are disabled on folder FOL2.
- # ncpcon security enforce /em /r CLSPOOL1_SERVER
-
Encryption is enforced on Volumes, Directories and Resource: CLSPOOL1_SERVER
A.1.21 Viewing or Closing Open Files
- files operation <v=volumename | f=filename | c=connection_number>
-
Use this command to list or close open files on an NCP volume by volume, filename, or connection number. If the file path or trustee names contain spaces, ensure to enclose them within double or single quotes.
To find the connection number assigned to a user’s connection, use the connection commands in Section A.1.19, Managing NCP Server Connections.
Operation Options
- list
-
Lists the open files for a specified NCP volume by volume, filename, or connection number.
- close
-
Closes the open files for a specified NCP volume by volume, filename, or connection number.
Options
- v=volumename
-
Replaces volumename with the name of the NCP volume.
- f=filename
-
Replaces filename with path on the Linux file system of the file you want to close, such as /usr/novell/sys/filename.ext.
- c=connection_number
-
Replaces connection_number with the station number of the connection whose open files you want to close.
Examples
files list v=sys
files list f=/usr/novell/sys/test.txt
files list "f=/usr/bob christo/novell/sys/test.txt"
files list c=9
files close v=sys
files close f=/usr/novell/sys/test.txt
files close 'f=/usr/bob christo/novell/sys/test.txt'
files close c=9
A.1.22 Managing Dynamic Storage Technology
NCPCON supports the commands in this section for use with OES Dynamic Storage Technology. For information about configuring and managing shadow volumes and file systems, see the OES 23.4: Dynamic Storage Technology Administration Guide.
- create shadow_volume <primary_volumename> <shadow_path>
-
Creates a non-clustered shadow association between a primary NSS volume and secondary NSS volume, and adds the SHADOW_VOLUME mount information to the /etc/opt/novell/ncpserv.conf file. If the file path or trustee names contain spaces, ensure to enclose them within double or single quotes.
When you issue the command from the NCP Console, you do not need to restart ndsd in order for the changes to take effect. When you issue the command from a Linux prompt, you must restart ndsd in order for the changes to take effect.
Options
- primary_volumename
-
Specifies the volume name for the primary NSS volume, such as VOL1.
- shadow_path
-
Specifies the Linux path of the mount location for the secondary NSS volume, such as /media/nss/ARCVOL1.
Examples
- create shadow_volume VOL1 /home/shadows/VOL1
-
Creates a shadow volume where VOL1 is the primary storage area and /home/shadows/VOL1 is its mount point as a shadow volume.
- create shadow_volume VOL1 "/home/bob christo/shadows/VOL1", create shadow_volume VOL1 '/home/bob christo/shadows/VOL1'
-
Creates a shadow volume where VOL1 is the primary storage area and /home/bob christo/shadows/VOL1 is its mount point as a shadow volume.
- remove shadow_volume [/l] [/i] [/f] <primary_volumename>
-
Removes the non-clustered shadow relationship between a primary NSS volume and a secondary NSS volume, and removes the SHADOW_VOLUME command from the /etc/opt/novell/ncpserv.conf file. You must unmount the volume before you issue the command.
IMPORTANT:You can use this command as part of the process to unlink the primary and secondary volumes of a non-clustered DST shadow volume. For information, see
Removing the Shadow Relationship for a Non-Clustered DST Shadow Volume
in the OES 23.4: Dynamic Storage Technology Administration Guide.Typically, you specify the /l option, which leaves the files in place on the primary volume and secondary volume, and removes the shadow relationship. This is equivalent to the Volume Tasks > Remove Shadow Action Options > Remove Shadow option in OES Remote Manager.
When the /l option is not used, the command attempts to move all files on the secondary volume to the primary volume, and then removes the shadow relationship between the two volumes. Ensure that the primary volume has sufficient space to accommodate the files before you unmount the volume and issue the remove command. Moving the files can take some time, depending on how much data must be moved. If a file move fails, the unlinking of the shadow relationship also fails. You can use the /i option to ignore file move errors and allow the unlinking to succeed. After the files on the secondary volume have been moved to the primary volume, the shadow relationship is removed, and a summary report is created and displayed.
Options
- primary_volumename
-
Specifies the volume name for the primary NSS volume, such as VOL1.
- /l
-
Leaves the files in place on the two volumes and removes the shadow relationship.
- /i
-
Ignores any file move errors that might occur if you issue the command without the /l option, and allows the unlinking of the shadow relationship to succeed.
For example, if there are duplicate files on the volumes, the duplicate instance on the secondary volume cannot be moved to the primary volume, and the shadow relationship cannot be unlinked. Using the /i option ignores the file move error and allows the relationship to be unlinked.
- /f
-
Provides a full detail report of actions taken. Use this option to understand which file moves might be failing.
Examples
Issue the following commands from the NCP Console, or add ncpcon at the beginning of the command when issuing it from a script or at a terminal console prompt.
- ncpcon remove shadow_volume /i /f VOL1
-
Removes the shadow relationship for shadow volume VOL1, and moves all files from the secondary storage area to the primary storage area. You must dismount VOL1 before you issue this command. File move errors are ignored. Full details of the actions taken are reported.
- remove shadow_volume /l VOL1
-
Removes the shadow relationship for shadow volume VOL1, and leaves files where they currently are on the secondary storage area and the primary storage area. You must dismount VOL1 before you issue this command.
- shadow volumename operation=<lp | ls | mp | ms> [options]
-
Allows you to list files on the shadow volume, or to move files between the primary storage area and the secondary storage area based on specified criteria. All files on the selected shadow volume that match the criteria are moved. Use the command from within cron jobs to automate data partitioning. If the file path or trustee names contain spaces, ensure to enclose them within double or single quotes.
Operation Options
- lp
-
Lists primary files. Lists all files currently residing on the primary storage area.
- ls
-
Lists shadow files. Lists all files currently residing on the secondary storage area.
- mp
-
Moves files to primary. Moves files that match the specified criteria to the primary storage area from the secondary storage area.
- ms
-
Moves files to shadow. Moves files that match the specified criteria to the secondary storage area from the primary storage area.
Operations
- pattern="searchPattern"
-
Specifies the file pattern to match against.
- owner="username.context"
-
Specifies the NetIQ eDirectory username and context of the owner of the files to match against.
- uid=uidValue
-
Specifies the Linux user ID to match against.
- time=[time_field]
-
Specifies which time field to match against, where the time_field is:
[m][a][c]
-
m: Last time modified (content)
-
a: Last time accessed
-
c: Last time changed (metadata)
-
- range=[time_period]
-
Specifies which time period to match against, where the time_period is:
[a][b][c][d][e][f][g][h][i][j]
-
a: Within last day
-
b: 1 day to 1 week
-
c: 1 week to 2 weeks
-
d: 2 weeks to 1 month
-
e: 1 month to 2 months
-
f: 2 months to 4 months
-
g: 4 months to 6 months
-
h: 6 months to 1 year
-
i: 1 year to 2 years
-
j: More than 2 years
-
- size=[size_differential]
-
Specifies the size differential to match against, where the size_differential is:
[a][b][c][d][e][f][g][h][i][j][k]
-
a: Less than 1 KB
-
b: 1 KB to 4 KB
-
c: 4 KB to 16 KB
-
d: 16 KB to 64 KB
-
e: 64 KB to 256 KB
-
f: 256 KB to 1 MB
-
g: 1 MB to 4 MB
-
h: 4 MB to 16 MB
-
i: 16 MB to 64 MB
-
j: 64 MB to 256 MB
-
k: More than 256 MB
-
- output="filename"
-
Output the search results to the specified file.
Examples
- shadow vol1 operation=ls pattern="*.exe"
-
Lists all files of type EXE that currently reside on the secondary storage area for the shadow volume vol1.
- shadow vol1 operation=lp size=g
-
Lists all files of sizes between 1 MB to 4 MB that currently reside on the primary storage area for the shadow volume vol1.
- shadow vol1 operation=ms range=j
-
Moves all files on the primary storage area that have not been modified, accessed, or changed in more than 2 years from the primary storage area to the secondary storage area for the shadow volume vol1.
- shift "volumename:\path\filename" [primary | shadow]
-
Returns the specified file’s location as being on the primary storage area or secondary storage area. Specify the primary or secondary options to move the specified file from its current location to the specified storage area.
The shift command works only at the command line, and not in ncpcon interactive mode. Enter the command as the root user at a terminal console prompt.
ncpcon shift "volumename:\path\filename" [primary | shadow]
OPTIONS
- primary
-
Moves the specified file from the secondary storage area to the primary storage area. The file must be closed when you issue the command; otherwise, the command fails.
- shadow
-
Moves the specified file from the primary storage area to the secondary storage area. The file must be closed when you issue the command; otherwise, the command fails.
Examples
Enter the commands as the root user at a terminal console prompt.
- ncpcon shift VOL1: "path\textfile.txt"
-
Shows the specified file’s storage area location in the shadow volume as primary (the primary storage area) or shadow (the secondary storage area) for the shadow volume sys.
- ncpcon shift "vol1:\usr\bob christo\textfile.txt" , ncpcon shift 'vol1:\usr\bob christo\textfile.txt'
-
Shows the specified file’s storage area location in the shadow volume as primary (the primary storage area) or shadow (the secondary storage area) for the shadow volume vol1.
- ncpcon shift VOL1: "path\textfile.txt" primary
-
Moves the specified file’s storage area location from the secondary storage area to the primary storage area for the shadow volume sys.
- ncpcon shift "vol1:\usr\bob christo\textfile.txt" primary , ncpcon shift 'vol1:\usr\bob christo\textfile.txt' primary
-
Moves the specified file’s storage area location from the secondary storage area to the primary storage area for the shadow volume vol1.
- ncpcon shift VOL1: "path\textfile.txt" shadow
-
Moves the specified file’s storage area location from the primary storage area to the secondary storage area for the shadow volume sys.
- ncpcon shift "vol1:\usr\bob christo\textfile.txt" shadow , ncpcon shift 'vol1:\usr\bob christo\textfile.txt' shadow
-
Moves the specified file’s storage area location from the primary storage area to the secondary storage area for the shadow volume vol1.
A.1.23 Managing Dynamic Storage Technology on OES Cluster Services for Linux Clusters
NCPCON supports the commands in this section for use with OES Dynamic Storage Technology in combination with OES Cluster Services for Linux clusters. For information about configuring and managing shadow volumes and file systems in a cluster, see the OES 23.4: Dynamic Storage Technology Administration Guide.
Use the following syntax in cluster load scripts to mount the volume in a cluster. With clustering, no changes are needed to the ncpserv.conf file for shadowing. The primary volume information is also not added to the ncpserv.conf file.
Scenario 1: Primary NSS and Shadow NSS
- ncpcon mount volumename=volID,SHADOWVOLUME=shadow_volumename
-
Use this command in a cluster load script when the primary volume is an NSS volume and the secondary volume is an NSS volume. Both NSS volumes must already exist and be mounted in NSS.
Replace volID with a value from 0 to 254 as the server volume ID to ensure that the volume has the same ID on all servers when it is mounted in a cluster resource.
Example
- ncpcon mount VOL1=254,SHADOWVOLUME=ARCHIVE1
-
Mounts the NSS volume named VOL1 with a volume ID of 254. The primary volume is an existing NSS volume named VOL1 (/media/nss/VOL1). The secondary volume is an existing NSS volume named ARCHIVE1 (/media/nss/ARCHIVE1).
Scenario 2: Primary Non-NSS and Shadow Non-NSS (Not Supported)
- ncpcon mount volumename=volID,SHADOWPATH=shadowpath,path=primarypath
-
Use this command when the primary volume is a non-NSS volume and the secondary volume is a non-NSS volume.
Replace volID with a value from 0 to 254 as the server volume ID to ensure that the volume has the same ID on all servers when it is mounted in a cluster resource.
Example
- ncpcon mount VOL1=254,SHADOWPATH=/media/ncpvolumes/ARCHIVE1,path=/media/ncpvolumes/VOL1
-
Mounts the NCP volume named VOL1 with a volume ID of 254. The primary volume’s path is /media/ncpvolumes/VOL1. The secondary volume’s path is /media/ncpvolumes/ARCHIVE1.
Scenario 3: Primary Non-NSS and Shadow NSS (Not Supported)
- ncpcon mount volumename=volID,SHADOWVOLUME=shadow_volumename,path=primarypath
-
Use this command when the primary volume is a non-NSS volume and the secondary volume is an NSS volume. The NSS volume must already exist on the system and be mounted in NSS.
Replace volID with a value from 0 to 254 as the server volume ID to ensure that the volume has the same ID on all servers when it is mounted in a cluster resource.
Example
- ncpcon mount VOL1=254,SHADOWVOLUME=ARCHIVE1,path=/media/ncpvolumes/VOL1
-
Mounts the NCP volume named VOL1 with a volume ID of 254. The primary volume’s path is /media/ncpvolumes/VOL1. The secondary volume is an existing NSS volume named ARCHIVE1 (mounted at /media/nss/ARCHIVE1).
Scenario 4: Primary NSS and Shadow Non-NSS (Not Supported)
- ncpcon mount volumename=volID,SHADOWPATH=shadowpath
-
Use this command when the primary volume is an NSS volume and the secondary volume is a non-NSS volume. The NSS volume must already exist on the system and be mounted in NSS.
Replace volID with a value from 0 to 254 as the server volume ID to ensure that the volume has the same ID on all servers when it is mounted in a cluster resource.
Example
- ncpcon mount VOL1=254,SHADOWPATH=/media/ncpvolumes/ARCHIVE1
-
Mounts an NSS volume named VOL1 with a volume ID of 254. The primary volume is an existing NSS volume named VOL1 (/media/nss/VOL1). The secondary volume is an NCP volume named ARCHIVE1 that is mounted at /media/ncpvolumes/ARCHIVE1.
Managing Quotas for Dynamic Storage Technology Volumes
NCPCON supports the ncpcon quotas command for OES Dynamic Storage Technology volume pairs. For information, see the OES 23.4: Dynamic Storage Technology Administration Guide.
You can run NCPCON console commands without entering the console by prefacing the command with ncpcon.
- quotas help
-
Displays command help at the command prompt.
- quotas view <nss_volume_name> <d|u> [c]
-
Shows the assigned NSS directory quotas or user quotas for a specified NSS volume that is used in a DST volume pair. Replace nss_volume_name with the name (such as VOL1) of the primary volume or the secondary volume.
Specify either directory (d) or user (u) after the volume name to indicate the type of quotas to display. You can use the combined (c) option to display the specified type of quotas for both volumes.
Options
- c
-
(Optional) Shows a combined view for the specified type of quotas on the primary volume and secondary volume of a DST shadow volume pair.
- d
-
Applies the operation to NSS directory quotas.
- u
-
Applies the operation to NSS user quotas.
Examples
- ncpcon quotas view VOL_D u
-
Shows the user quotas for NSS volume VOL_D. VOL_D can be the primary volume or secondary volume in a DST shadow volume pair.
- ncpcon quotas view VOL1 d c
-
Shows a combined view of the directory quotas on the primary volume and secondary volume of a specified DST shadow volume.
- quotas sync <ALL|MISSING|PERCENT> <nss_volume_name> [percent_value] <d|u> [q]
-
Synchronizes the NSS directory quotas or user quotas from the primary volume to the secondary volume of a DST shadow volume pair. Replace nss_volume_name with the name (such as VOL1) of the primary volume. You can specify to use the same settings, or specify a percentage to set smaller or larger quotas on the secondary volume. You can duplicate all settings, or duplicate settings only where they do not exist.
Specify either directory (d) or user (u) after the volume name to indicate the type of quotas to synchronize.
Operations
- ALL
-
For all of the directory quotas or user quotas (whichever type is specified) that are currently set on the primary volume, duplicates the quotas settings on the secondary volume.
- MISSING
-
For each of the directory quotas or user quotas (whichever type is specified) that are currently set on the primary volume, if a quota is not set on the secondary volume, duplicates the quota setting on the secondary volume. This option does not overwrite existing quotas on the secondary volume.
- PERCENT
-
For each of the directory quotas or user quotas (whichever type is specified) that are currently set on the primary volume, sets the quotas settings on the secondary volume as a specified percentage of the quota that exists on the primary volume. The percentage value must also be specified after the volume name.
A percent value of 100 is a one-to-one quota assignment. A percent value of 50 assigns a quota that is one-half the size of the quota set on the primary volume. A percent value of 200 assigns a quota that is twice the size of the quota set on the primary volume.
Options
- d
-
Applies the operation to NSS directory quotas.
- u
-
Applies the operation to NSS user quotas.
- percent_value
-
Required if the PERCENT operation is used. Specifies the value to use when calculating the quota for the secondary volume based on a percentage of the primary volume’s quota.
- q
-
(Optional) Indicates quiet mode. No output appears in the execution window.
Examples
- ncpcon quotas sync ALL VOL_D u
-
For all of the NSS user quotas that are currently set on the primary volume VOL D, duplicates the quotas setting on the secondary volume of a DST shadow volume pair.
- ncpcon quotas sync PERCENT VOL1 50 d
-
For each of the NSS directory quotas that are currently set on the primary volume VOL1, sets a quota that is one-half that size on the secondary volume of a DST shadow volume pair.
- ncpcon quotas sync MISSING VOL1 u
-
For each of the NSS user quotas that are currently set on the primary volume VOL1, if a quota does not exist on the secondary volume, duplicates the quota setting on the secondary volume of a DST shadow volume pair.