19.1 Understanding Business Roles
Business roles specify a set of applications, roles, and permissions that each member of a business role is authorized to access. The set of authorized resources is defined by the authorization policy of the business role. A business role authorizes resources and generates requests, but does not assign resources.
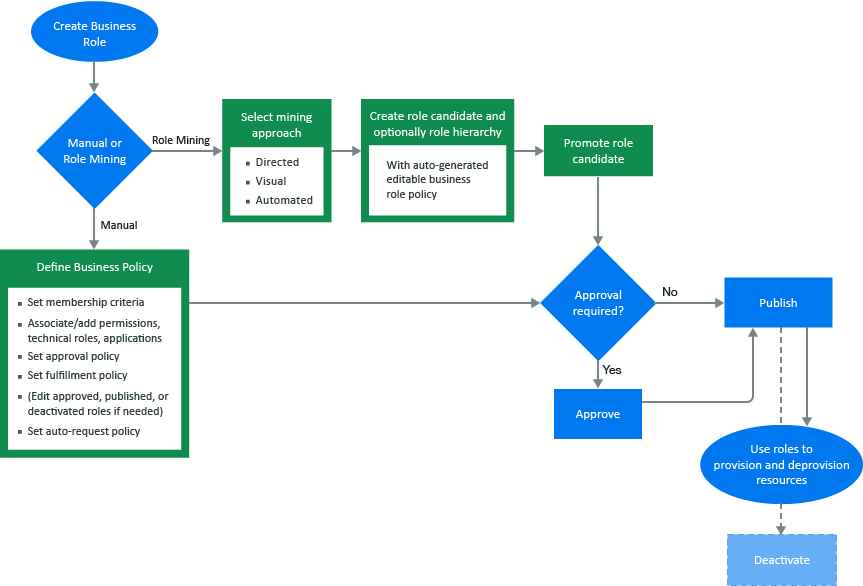
Figure 19-1 shows the business role workflow in Identity Governance.
Figure 19-1 Business Role Workflow
19.1.1 Understanding Business Role Access Authorizations
The Customer, Global, or Business Roles Administrator creates, modifies, and defines business roles, and manages business role policies. They can delegate administrative actions by specifying a Business Role Owner or a Business Role Manager for each business role. Business Role Owners can view and approve business roles but cannot edit business roles. Business Role Managers can edit business role membership and resource authorizations, submit business roles for approval, promote role candidates, publish roles, and deactivate roles. If the administrator does not specify role owners in the business role definition, Identity Governance automatically assigns the administrator who created the role as the role owner. For more information about access authorizations, see Section 2.1, Understanding Authorizations in Identity Governance.
19.1.2 Understanding Business Role Mining
Business role mining is the process of discovering and analyzing business data to group multiple users and access rights under one business role candidate. Identity Governance uses advanced analytics to mine business data and to identify role candidates. Customer, Global, or Business Roles administrators can use role mining to reduce complexity in defining roles, and easily select role candidates with authorized users, permissions, technical roles, and applications to create business roles and technical roles with common permissions. Identity Governance uses three approaches to business role mining to identify business role candidates.
- Directed role mining
-
Enables administrators to direct the mining based on specified user attributes. If administrators are not sure which attribute to select, they can search for recommended attributes, then select an attribute from the recommended bar graph that displays the strength of attributes that have data. Additionally, directed role mining enables administrators to specify a minimum membership and coverage percentage to identify role candidates. For example, if an administrator selects Department as the attribute to group candidates by, the mining results display the list of items consisting of department name with the associated users, permissions, roles, and applications as role candidates.
- Automated role mining
-
Enables administrators to enhance business role mining in larger environments by specifying a minimum number of attributes, a minimum number of occurrences, and the maximum number of results. Administrators can also specify a coverage percentage to identify role candidates. In this approach, Identity Governance uses the attributes specified in the role mining settings in Configuration > Analytics and Role Mining Settings to calculate role candidates.
NOTE:We recommend that you use this option if you have a large and complex catalog, such as a catalog with a greater number of variations in extended attributes, with multiple values of attributes, and a catalog size that slows role mining performance.
- Visual role mining
-
Enables administrators to select role candidates from a visual representation of the user attributes. The width of an attribute circle displays the strength of the recommendation, and the width and darkness of the lines indicate the affinity of the attribute to other user attributes. Administrators can customize the mining results by modifying the default maximum number of results, the minimum potential members, and the number of automatic recommendations. In this approach, Identity Governance uses the attributes specified in the role mining settings in Configuration > Analytics and Role Mining Settings to calculate role candidates.
NOTE:Variations in the number of extended attributes, attributes with multiple values, or overall catalog size may affect the performance of visual role mining. You might see invalid results when mining larger or more complex data. You can disable this option by setting the com.netiq.iac.analytics.role.mining.visual.hide global configuration property to true. To optimize performance and to avoid invalid results, use the automated role mining option to mine for roles.
Identity Governance uses the permission, the technical role, and application coverage fields to determine which authorizations are automatically populated in the business role candidate for automated and directed role mining options. For example, if permission coverage is at 50%, then 50% of the members must hold the permission for Identity Governance to add it as an authorization in the candidate. If it is 100%, then all members must hold the permission for Identity Governance to add it as an authorization.
Table 19-1 helps you determine the type of role mining to use.
Table 19-1 Determining Which Role Mining Approach to Use
|
If |
Then |
|---|---|
|
You have a small catalog and want Identity Governance to mine for roles based on attributes specified in the role mining settings in Configuration > Analytics and Role Mining Settings, and automatically suggest role candidates. |
Select Visual Role Mining or Automated Role Mining. |
|
You have large and complex data to mine, want Identity Governance to mine the data based on the attributes specified in the role mining settings in Configuration > Analytics and Role Mining Settings, and want to include minimum occurrences of attributes as mining criteria without specifying any user attributes. |
Select Automated Role Mining. |
|
You want to direct the mining by specifying user attributes from the catalog. NOTE:When using this role mining option, you are not limited to using only the attributes included in the role mining settings in Configuration > Analytics and Role Mining Settings. |
Select Directed Role Mining. |
NOTE:Role recommendations are dependent on your data and role mining settings. To optimize search results, administrators can modify default role mining settings in Configuration > Analytics and Role Mining Settings. For more information see, Configuring Analytics and Role Mining Settings.
After previewing users and their associated permissions, technical roles, and applications, administrators can analyze specified potential role candidates to see if they duplicate existing roles by matching on membership or authorizations. Existing roles that match the membership or authorizations are displayed in the potential candidate list after performing the analysis. Administrators can then choose not to create those candidates. Additionally, Identity Governance could group common permissions under a technical role, and generate a technical role candidate for each application.
NOTE:Identity Governance creates the mined business or technical roles in a candidate state. Administrators can edit and save role candidates, but they must promote candidates before they can activate them as roles. Administrators can also select multiple role candidates and submit them for approval, publish them, or delete them using the options under Actions.
Identity Governance performs role mining as a background process. If you navigate from the role mining page, role mining will continue. When you return to the role mining page, click Load Previous Suggestions to list the mining suggestions, then create the business role candidates. The generated role mining suggestions are available for 96 hours. You can adjust the mining retention interval by selecting Configuration > Analytics and Role Mining Settings.
19.1.3 Understanding Role Hierarchy with Role Mining
Business role mining in Identity Governance creates business roles for each selected candidate, but cannot group the created roles. Role hierarchy allows you to create a hierarchy of roles, based on the mining attributes, that allow you to assign resources either at the candidate level, or by grouping the candidates at a higher level.
NOTE:Role hierarchy is not available for visual role mining.
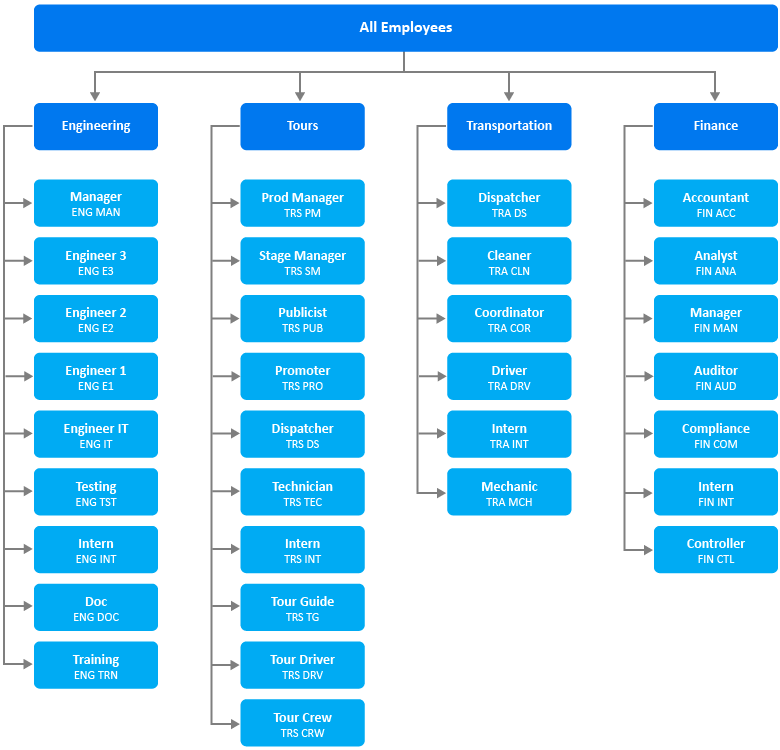
When you select Create business role hierarchy, you can select the attributes used in the role mining as grouping attributes for the role hierarchy. For example, Figure 19-2 illustrates a company organization chart in which each department includes job codes that represent positions. The company wants to create departmental business roles for Engineering, Tours, Transportation and Finance, as well as roles for each job code. Furthermore, they want an “All Department” role that includes the Engineering department and all the other top-level departments. Selecting the department attribute as the role hierarchy grouping attribute would create business roles that mirror the organizational chart.
Figure 19-2 Company Organization with Department and Job Codes
19.1.4 Understanding Business Role States
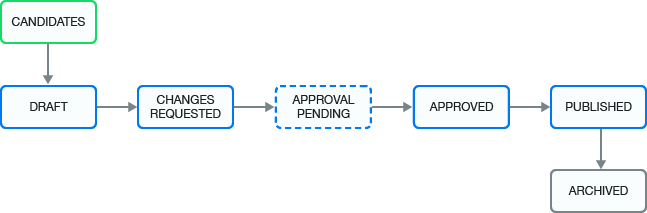
After you create, or after Identity Governance mines a business role, the role goes through many states during its life cycle, as shown in Figure 19-3.
Figure 19-3 Business Role States
|
Business Role State |
Description |
|---|---|
|
CANDIDATES |
The mining process created the business role, and the administrators must promote it before they or others can approve it (depending on the approval policy) and publish it. This state corresponds to the internal state called MINED. |
|
DRAFT |
The assigned approval policy requires approval and the administrator has not submitted the changes for approval. |
|
CHANGES REQUESTED |
The approver denies approval of a business role. This state corresponds to the internal state called REJECTED. |
|
APPROVAL PENDING |
Pending changes are ready for approval by the approver specified in the approval policy. This state corresponds to the internal state called PENDING_APPROVAL. |
|
APPROVED |
The approver approved the business role, but the business role has not yet been published. |
|
PUBLISHED |
The business role is approved and the administrator has published the role. |
|
ARCHIVED |
An administrator deletes the policy or creates a new version. Identity Governance archives the policy for history and reporting purposes. Identity Governance never displays archived business roles in the application. |