9.4 Configuring Identity Reporting
After installing Identity Reporting, you can modify many of the installation properties. To make changes, run the Identity Governance Configuration Update utility. For more information, see Section 15.1.5, Using the Identity Governance Configuration Update Utility.
If you change any setting for Identity Reporting with the Identity Governance Configuration Update utility, you must restart the application server that hosts Identity Reporting for the changes to take effect. However, you do not need to restart the server after making changes in the web user interface for Identity Reporting.
You should also update to the latest version of the Identity Governance reports. For more information, see Using the Download Page
in the Identity Governance Reporting Guide.
9.4.1 Assigning the Report Administrator Authorization
To access Identity Reporting you must assign the Report Administrator authorization and identify at least one data source. You assign the administrator authorization in Identity Governance. Use the following steps to assign the Report Administrator authorization to a user or group.
To assign the Report Administrator authorization:
-
Log in to Identity Governance as the Global Administrator.
-
Select Configuration > Authorization Assignments.
-
Assign users or groups to the Report Administrator authorization.
-
Save the change.
-
Select Identity Manager System Connection Information.
-
For Identity Manager URL, specify the URL for Identity Reporting.
For example, http://myserver.mydomain.com:8080/IDMRPT
-
Save the change, then refresh the browser to see the change.
You must now add a data source for Identity Reporting to be able to generate reports. For more information, see Section 9.4.5, Adding Data Sources to Identity Reporting.
9.4.2 Starting Identity Reporting
To verify installation and to initialize the Identity Reporting database, you must start the application server.
-
Log in to the application server that hosts Identity Reporting.
-
(Conditional) If this is the first time for starting Identity Reporting, complete the following steps:
-
Delete all files and folders in the following directories for your application server:
-
Linux: Temporary directory, located by default in
-
/opt/netiq/idm/apps/tomcat/temp
-
Catalina cache directory, located by default in /opt/netiq/idm/apps/tomcat/work/Catalina/localhost
-
-
Windows: Temporary directory, located by default in:
-
C:\netiq\idm\apps\tomcat\temp
-
Catalina cache directory, located by default in: C:\netiq\idm\apps\tomcat\work\Catalina\localhost
-
-
-
Delete all log files from the logs directory of your application server, located by default in:
-
Linux: /opt/netiq/idm/apps/tomcat/logs
-
Windows: C:\netiq\idm\apps\tomcat\logs
-
-
-
Start Apache Tomcat. For more information, see Section 3.5.3, Starting and Stopping Apache Tomcat.
-
(Optional) To observe the Apache Tomcat initialization process in Linux, enter the following command:
tail -f path_to_Tomcat_folder/logs/catalina.outWhen the process completes, the file contains the following message:
Server startup in nnnn ms -
To log in to Identity Reporting, you need an account with the Report Administrator authorization.
For more information, see Section 9.4.1, Assigning the Report Administrator Authorization.
9.4.3 Testing the Integration with Identity Governance
As a Report Administrator, you can access Identity Reporting from the Identity Governance interface. You can also log in directly from the Identity Reporting application through a URL. Only accounts with the Report Administrator authorization can log in to Identity Reporting.
-
To verify that you can access Identity Reporting from Identity Governance, complete the following steps:
-
Log in to Identity Reporting as a Report Administrator.
https://myserver.mydomain.com:8443/IDMRPT
-
Select Home in the upper right corner.
-
Select the Reporting module icon near your user name.
-
Verify that you are redirected to Identity Reporting.
-
-
To verify that Identity Governance denies other authorizations to Identity Reporting, complete the following steps:
-
Log in to Identity Governance, as a Global Administrator or Security Officer.
https://myserver.mydomain.com:8443
-
Remove the Report Administrator authorization from the account that successfully logged in to Identity Reporting.
-
Log in to Identity Reporting with that account, which no longer has the authorization, and log in to Identity Governance and access the reporting features.
-
Identity Governance: https://myserver.mydomain.com:8443
-
Identity Reporting: https://myserver.mydomain.com:8443/IDMRPT
-
-
Verify you cannot access Identity Reporting.
You can also attempt to log in to Identity Reporting by using a Global Administrator or Security Officer account to verify that accounts with high-level privileges cannot access Identity Reporting without the Report Administrator authorization.
-
9.4.4 Configuring a Proxy Server for the Identity Reporting Server
The server that runs Identity Reporting must have internet access to be able to access and download the most current reports for Identity Governance from the Reporting Content Delivery Network (CDN). For more information, see Using the Download Page
in the Identity Governance Reporting Guide.
If your Identity Reporting server does not have internet access, you must configure a proxy server that can access and download the most current reports for Identity Governance from the Reporting content delivery network (CDN), and is also configured to access and send updated reports to the Identity Reporting server. This configuration allows you to isolate the Identity Reporting server from the internet while ensuring reports are up to date.
Figure 9-1 Identity Reporting Server Using a Proxy Server
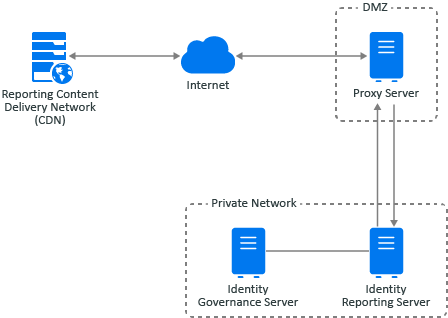
You must use the Identity Governance Configuration Update utility to enable the Identity Reporting server to send the request for the Reporting CDN through the proxy server.
To configure the Identity Reporting server to use a proxy server for the updated reports requests:
-
Log in to the Identity Reporting server as an administrator user on a Windows server or as a user with root access on a Linux server.
-
From a command prompt, access the Identity Governance Configuration Update utility directory.
-
Linux: /opt/netiq/idm/apps/configupdate
-
Windows: C:\netiq\idm\apps\configupdate
-
-
Launch the Identity Governance Configuration Update utility.
-
Linux: ./configupdate.sh
-
Windows: configupdate.bat
-
-
Click the Reporting tab.
-
In the lower left corner, click Show Advanced Options.
-
Scroll towards the bottom of the page and find the Outbound Proxy section.
-
Specify the hostname or IP address, the port, and if you are using SSL or not of the proxy server.
-
Click OK to save the changes and the Identity Governance Configuration Update utility automatically closes.
-
Restart Apache Tomcat. For more information, see Section 3.5.3, Starting and Stopping Apache Tomcat.
9.4.5 Adding Data Sources to Identity Reporting
Identity Reporting runs reports against your connected data sources. Before you can run reports, you need to add one or more data sources.
IMPORTANT:You must add the Identity Governance operations (igops) database as a data source in Identity Reporting. The igops name is the default name of the operations database.
-
Log in to Identity Reporting as the Report Administrator.
https://myserver.mydomain.com:8443/IDMRPT
-
Select Data Sources.
-
Select Add.
-
Specify whether you want to select from the list of data sources or provide the details for the source.
-
(Conditional) If you selected Provide database details, specify the values for the data source. For example, database platform, the host name or IP address of the database server, and include the following settings:
- Database
-
Specifies the name of the database. For example, to add the Identity Governance database, specify igops for PostgreSQL and orcl or whatever name you gave the Oracle database.
- Username
-
Specifies an account that can access the tables and views in the database. For example, when adding the Identity Governance database, specify igrptuser.
-
(Optional) Test the connection to your data source.
-
Select Save.
-
Clean up the Apache Tomcat folders as described in Step 2.
You might need to restart Apache Tomcat.
-
Run a test report to verify functionality in Identity Reporting.
For more information about running reports, see
Using the Reports Page
in the Identity Reporting Guide.