15.4 Understanding Technical Role Mining
Technical role mining is the process of discovering and analyzing business data to logically group permissions to simplify the review process or allow grouping of related permissions under one technical role candidate. A technical role candidate is a set of permissions and users that can be promoted to a technical role. OpenText Identity Governance uses advanced analytics to mine business data and to identify role candidates. Customer, Global or Technical Roles Administrators can use role mining to create technical roles with common permissions after collecting related metrics.
OpenText Identity Governance uses the following two approaches to identify technical role candidates.
- Automatic Suggestions
-
Enables administrators to direct the mining calculations by specifying the candidate type, minimum number of permissions that a specified number of users should have in common, the coverage percentage, the maximum number of role suggestions, and other role mining options.
For more information about Automatic Suggestions criteria and computation, see Section 15.4.1, Understanding Automatic Suggestions Mining Approach.
- Visual Role Mining
-
Enables administrators to select role candidates from a visual representation of the distribution of users based on permissions. The map displays several clusters that can be potential technical role candidates. Administrators can click within the user access map and drag to select permissions within an area on the map, then view technical role candidates.
With both these approaches, you can edit and save role candidates. You must also promote candidates before you can activate them as roles. You can also generate technical role candidates when you use mining to create a business role. For more information about business roles, see Section 16.0, Creating and Managing Business Roles.
OpenText Identity Governance performs role mining as a background process. If you navigate from the role mining page, role mining will continue. When you return to the role mining page, click Load Previous Suggestions to list the mining suggestions, then create the technical role candidates. The generated role mining suggestions are available for 96 hours. You can adjust the mining retention interval by selecting Configuration > Analytics and Role Mining Settings.
HINT:If you have a large catalog of users and technical roles, data mining performance might be very slow and eventually fail. To improve performance for technical role mining, limit the analysis to a specific set of permissions or permissions held by a specific set of users or contact your SaaS Operations Administrator to adjust properties for role mining.
15.4.1 Understanding Automatic Suggestions Mining Approach
When OpenText Identity Governance collects technical role related User to permission assignments metric, it stores the permission-assignment map in the database to display automatic suggestions. The metric results are in a compressed format in the database where rows are permissions and columns are users holding permissions.
The database binary matrix includes all users who hold at least one of the permissions and all permissions which are held by at least one user. The number of included users and the number of permissions in this matrix are based on com.netiq.iac.analytics.roles.technical.MaxUserSize and com.netiq.iac.analytics.roles.technical.MaxPermSize configuration properties respectively. OpenText Identity Governance updates this data based on the metrics schedule.
The metrics results (permission-assignment map) include several clusters that can be potential technical role candidates. The map is like the visual representation displayed when you choose the Visual Role Mining approach. If needed for debugging purposes, you can view Automatic Suggestions map by setting the com.netiq.iac.roleMining.showMapData configuration property to true, then clicking Show Maps in the Role Mining Settings.
NOTE:In SaaS environments, you will need to work with your SaaS Operations Administrator to make changes to the default values of the configuration properties.
OpenText Identity Governance further analyzes these clusters, isolates (permission-user pairs), and sorts them by the rectangle area (number permissions multiplied by the number of users). During this process, the matrix is transposed repeatedly, and rows are moved based on similarity and similar rows are kept together until the top matching candidates are found.
When you select Automatic Suggestions and save the default criteria or specify criteria, OpenText Identity Governance applies the criteria as boundary conditions and removes the rows and columns that do not meet the specified criteria. It also removes any empty rows and columns that are created after applying criteria, then creates cluster or clusters of permission-user pairs based on the candidate type and other settings
Understanding Technical Role Automatic Suggestions Mining Approach Settings
By default, role mining candidate type is Any Perimissions and administrators can use the default candidate type and related default settings to generate role mining suggestions. However, based on your data and business needs, you might need to modify your default role mining settings and candidate type to generate more specific technical role suggestions. For both candidate types, you can:
-
Filter permissions by users and by permissions settings using advanced filters to limit permissions used in a technical role using user and permission attributes respectively.
NOTE:When you filter permissions by users, OpenText Identity Governance finds permissions that satisfy all your criteria. Therefore, all permissions held by your specified users might not be included in the suggested role candidates if you selected Any permission as the candidate type. You might want to increase the number of candidates to get more common permissions. To find only all permissions held in common by your specified users, select Only all common permissions as the candidate type, then specify additional filter and exclusion settings.
-
Search and select specific users and permissions to exclude from the calculation of suggested technical roles.
Additionally, when selecting Any permissions as the candidate type, you can:
-
Change the maximum number of suggestions to display.
NOTE:OpenText Identity Governance can display maximum thousand suggestions. Each suggestion includes a different set of users and permissions.
-
Specify minimum number of users that must hold the permissions to be included in the suggested role.
-
Specify minimum number of permissions that the suggested role should include.
-
Specify percentage of users that must hold a permission for the permission to be included in the calculation of roles. For example, if you specify permission coverage is ten percent for permissions held by hundred users, then at least ten users should hold the permission to be included in the suggestion.
Example with Candidate Type as Any Permissions
When the candidate type is Any Permission, OpenText Identity Governance displays the top matching suggestions based on Number of candidates to show and weighted rank. The resulting permission-assignment map is a set of rectangles (technical role suggestions) where the number of rectangles is equal to your specified number of candidates to show.
Find next a simple example of the role mining settings and corresponding permission-assignment map and results when OpenText Identity Governance searches for technical role candidates based on the following criteria.
-
Candidate Type: Any permissions
-
Filter permissions by users: Display Name equals one of ['Armando Colaco', 'Franke Drake', 'Henry Morgan', 'Leon Lavalette', 'James Ross', 'Lisa Haagensen" or 'Camille Pissaro']
-
Number of candidates to show: 5
-
Minimum number of permissions: 3
-
Minimum number of users: 3
-
Permission coverage: 0%
Based on these specified criteria, OpenText Identity Governance finds 4 candidates corresponding to the biggest clusters on the permission-assignment map.
Figure 15-2 Permission-Assignment Map for Techncial Role Candidates With Any Permission

Figure 15-3 Any-Permission Candidate Type Results

OpenText Identity Governance ranks the role mining suggestions by the number of permissions multiplied by the number of users. In the above example, 5 users match the role mining criteria and hold 4 permissions in common (total twenty), OpenText Identity Governance lists them first as it has the most number of users and the highest total of permissions multiplied by users. The following candidates have 4 users who hold 5 permissions in common (total twenty), 6 permissions held by 3 users (total 18), then 3 permissions held by 4 users (total twelve).
Example with Candidate Type as Only All Common Permissions
When the candidate type is Only All Common Permissions, OpenText Identity Governance displays one candidate that includes all common permissions held by all users or user specified by the additional role mining settings.
Find next another example of permission-assignment map and results when OpenText Identity Governance searches for technical role candidates based on following criteria.
-
Candidate Type: Only common permissions
-
Filter permissions by users: Display Name equals one of ['Armando Colaco', 'Franke Drake', 'Henry Morgan', 'Leon Lavalette', 'James Ross', 'Lisa Haagensen" or 'Camille Pissaro']
Figure 15-4 Permission-Assignment Map for Technical Role Candidates With Only Common Permissions
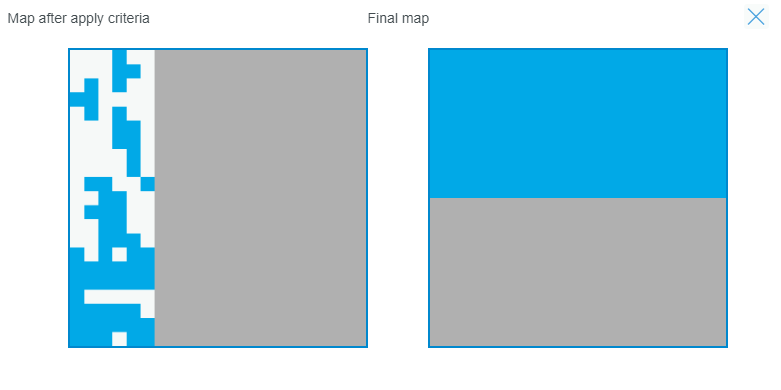
Figure 15-5 Only-All-Common-Permissions Candidate Type Results
15.4.2 Determining Which Technical Role Approach to Use
Use Table 15-1 to determine the type of role mining to select.
Table 15-1 Determining Which Role Mining Approach to Use
|
If |
Then |
|---|---|
|
You want to use user and permission relationships to automatically identify potential candidates and create more than one technical role based on any permissions or only common permissions |
Select Automatic Suggestions NOTE:Automatic role mining identifies potential role candidates and allows you to choose a role candidate instead of creating one, thereby avoid duplicating a technical role. |
|
You want to use the user access map to create a role candidate, add or remove permissions, estimate users, and analyze SoD violations |
Select Visual Role Mining |