Viewing Fortify WebInspect Scan Results in Fortify Software Security Center
Fortify WebInspect saves scan results (results data and audit![]() The process of assessing an application or program for security vulnerabilities. data) in FPR format, which you can upload to Fortify Software Security Center. (See Uploading Scan Artifacts.) Fortify WebInspect issue details differ somewhat from those shown for issues uncovered by other analyzers, such as Fortify Static Code Analyzer.
The process of assessing an application or program for security vulnerabilities. data) in FPR format, which you can upload to Fortify Software Security Center. (See Uploading Scan Artifacts.) Fortify WebInspect issue details differ somewhat from those shown for issues uncovered by other analyzers, such as Fortify Static Code Analyzer.
Important! To successfully integrate Fortify WebInspect with Fortify Software Security Center, you must install a trusted CA certificate on the Java Runtime environment on both the Fortify Software Security Center and WebInspect servers.
In the left panel of the CODE tab, the Overview section displays summary information about the finding and the Implications section. The Additional References section lists any pertinent references available.
The center panel displays the following information:
Method: HTTP method![]() An action that a web service performs. For instance, one web service may have one WSDL that contains four operations. Those might be, for example, Update, Create, Delete, and Diagnostic. (Same as operation). used for the attack (for example GET, PUT, and POST)
An action that a web service performs. For instance, one web service may have one WSDL that contains four operations. Those might be, for example, Update, Create, Delete, and Diagnostic. (Same as operation). used for the attack (for example GET, PUT, and POST)
Vulnerable Parameter: Name of the vulnerable parameter![]() An item of information, such as a name, a selection, or a number, passed to a program by another program or an end-user.
An item of information, such as a name, a selection, or a number, passed to a program by another program or an end-user.
Attack Payload: Shellcode used as the payload![]() A discrete software unit deployed over a network. for exploiting the vulnerability
A discrete software unit deployed over a network. for exploiting the vulnerability
Below this information, the Request section displays the request made, with the attack highlighted. The Response section displays the response to the request, with the trigger highlighted.
Note: If responses contain binary data or a large volume of data (more than 50 KB), you can see the Download Response button at the bottom of the Response section. To download responses such as these in a text file, click Download Response.

Viewing Additional Details and Recommendations
To view additional details and recommendations for the issue, on the issue toolbar, click one of the following:
-
Open in new tab
- Expand to full screen

On the right, the DETAILS section provides suggestions on what to look for in this issue.
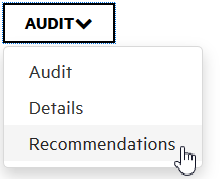
To view recommendations and tips on how to address the issue, from the DETAILS list, select Recommendations.
For information about how to use the panel on the right to audit the issue, see Auditing Issues.