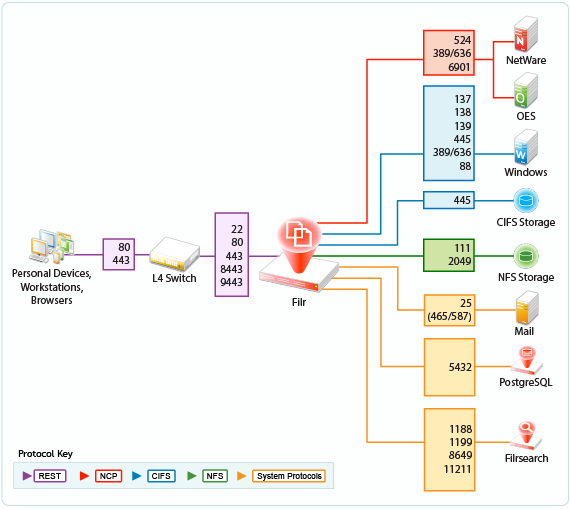
2.7 Ports Used in Filr Deployments
Figure 2-14 illustrates the ports that can be used in Filr deployments, including insecure ports. For information on configuring and securing Filr securely, see DMZ Setup for Filr
in the Filr 5.0: Maintenance Best Practices Guide.
Figure 2-14 Filr Port Usage