16.9 DMZ Setup for Filr
IMPORTANT:Security is a complex subject and OpenText does not attempt to suggest a complete defense solution with this example. OpenText recommends that you consult with your security professional to implement Filr in a DMZ.
To provide an additional level of security, you can set up Filr in a DMZ. You might want to consider setting up Filr in a DMZ especially if you are planning to allow external users to access the Filr system. It is most secure to restrict external user access to Filr appliances that are located in the DMZ, rather than allowing external users access to a Filr appliance behind the internal firewall.
The actual data is never stored in the DMZ. It is stored behind the internal firewall on the database and search appliances, on the Windows and OES servers (for your Net Folders), and on a SAN for files in personal storage.
Figure 16-1 illustrates a basic setup with Filr running in a DMZ, including information about the ports that you need to open for the firewalls and for communication between the various servers.
Figure 16-1 Filr in a DMZ
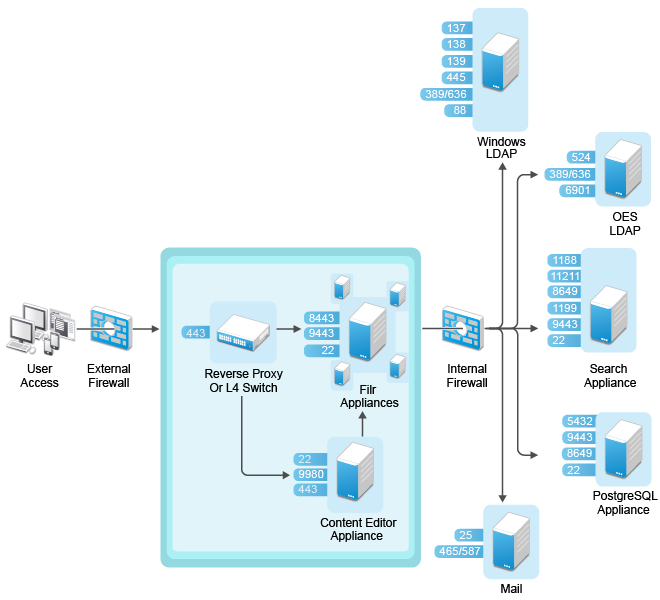
Only traffic destined to the DMZ is allowed through the front-end firewall, and only traffic from the DMZ to the internal network is allowed through the back-end firewall.
In a clustered environment, it is also possible for some of the Filr appliances in the cluster to run behind the internal firewall while others run in the DMZ. Doing so can result in performance benefits for internal users. Setting up Filr in this way requires that you use memcached caching. For more information about configuring memcached caching, see Filr Clustering Configuration in the OpenText Filr 23.4: Administrative UI Reference.
For more information about port configuration in Filr, see Port Numbers
in the OpenText Filr 23.4: Administrative UI Reference.
For information about setting up NetIQ Access Manager as a reverse proxy, see Access Manager (NAM) and Filr Integration
in the OpenText Filr 23.4: Installation, Deployment, and Upgrade Guide.