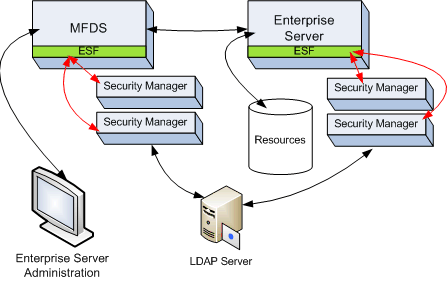
When a user attempts to access an Enterprise Server feature or application, or when an application attempts to access a controlled resource, Enterprise Server's External Security Facility (ESF) submits a security query to the appropriate ESMs to authenticate or authorize the action.
The illustration below shows the components involved in securing an installation, and the communications between each.
- When they log on to a system, Enterprise Server administrators are authenticated against any security managers that are configured for the Directory Server. Access to Enterprise Server configuration is denied unless the authentication is successful.
- When an Enterprise Servers accesses a resource, for example programs or databases, the request is authenticated against the security managers configured for the Enterprise Server. Access to the resource is denied unless the authentication is successful.
- Security managers can use LDAP repositories to verify authentication requests.