
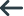
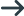

Bruce is logged in to the XDB Server develop. He issues a SELECT command referencing orders.eastern.may. This request is received by the XDB Server develop. Based on the system tables on develop, outbound mapping might occur. Assuming that outbound mapping does not occur, the SELECT request referencing orders.eastern.may is sent to sales with an AuthID of bruce and no password.
The SELECT request is then received at the XDB Server sales with an AuthID of bruce and no password. Since no password is present, SYSIBM.SYSLUNAMES is checked on sales. The values in this table indicate that all requests coming from the XDB Server develop are to be trusted. The values in SYSIBM.SYSLUNAMES also indicate that requests from the XDB Server develop are subject to inbound mapping.
Since no password accompanied the request, SYSIBM.SYSUSERNAMES is checked next. The values in this table indicate that any request from the XDB Server develop should be mapped to an AuthID of developr. Finally, the SELECT command referencing orders.eastern.may is processed with an AuthID of developr. Privileges are checked and a result is returned to bruce via the XDB Server develop.