Understanding the Capabilities that You Can Deploy
The Platform infrastructure enables you to deploy a combination of container-based capabilities, which represent licensed products and functions that shape your ArcSight environment. Each release of the Platform supports a specific set of capabilities that you can deploy.
To perform appropriately, some capabilities that you deploy depend on the presence of additional capabilities. For example, most capabilities need the Fusion capability because it provides the user management functions in the Platform.
For a complete security, user, and entity solution, you might also need to integrate software and components that are not deployed within the Platform. For example, your solution might need a database for data storage and OpenText ArcSight SmartConnectors for data collection from various data sources.
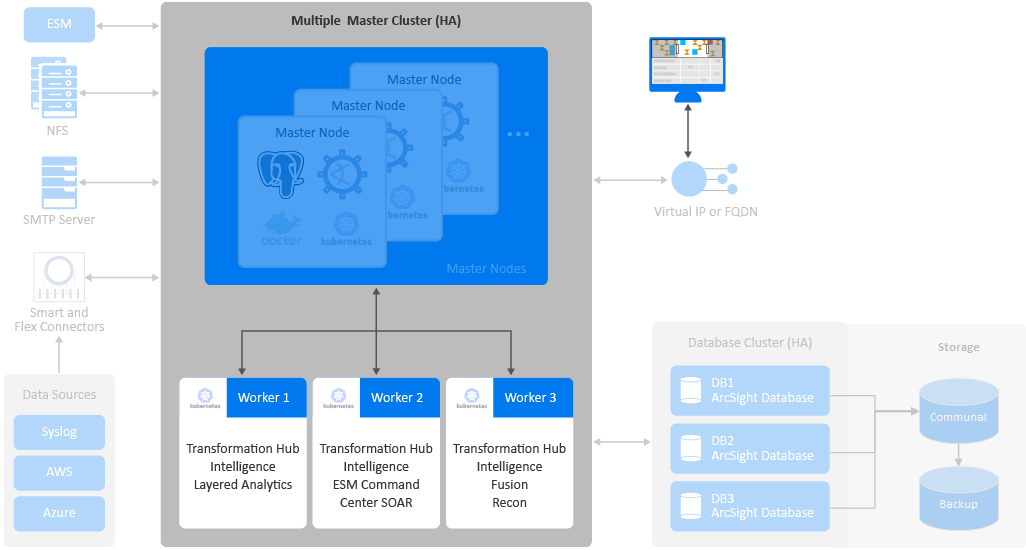
You can deploy the following capabilities in the Platform:
- ArcSight ESM Web App (ESM Command Center)
- Fusion
- Intelligence
- Layered Analytics
- Recon
- Transformation Hub
For more shared capabilities, see Understanding Labels and Pods
ArcSight ESM Web App (ESM Command Center)
The ArcSight ESM Web App (ESM Command Center in the ArcSight Platform) is a licensed product that provides widgets and dashboards that you can customize in the Dashboard feature for detecting threats to your enterprise. If you deploy Intelligence and Layered Analytics in the same cluster as ESM Command Center, certain widgets will combine data from ESM and Intelligence to provide you greater insight into events and entity behavior.
With Transformation Hub deployed in the same cluster, ESM can receive event data for dashboarding and further correlation. This capability requires Fusion to be deployed in the same cluster.
For more information about ESM Command Center, see the following topics:
Fusion
All capabilities require that Fusion be deployed in the same cluster.
To ensure a unified solution experience, Fusion provides the common elements needed for the products that you deploy in the Platform environment: user management, the Dashboard, SOAR, ArcMC, and other core services. Fusion services also support single sign-on (SSO) configuration across the capabilities, high-capacity data management, and a search engine.
Fusion enables you to add users and groups, as well as manage their roles and permissions. The My Profile section of user management enables users to set their preferences for features like Search. The Dashboard enables you to visualize, identify, and analyze potential threats by incorporating intelligence from the multiple layers of security sources that might be installed in your security environment.
Fusion ArcMC, the containerized version of ArcSight Management Center (ArcMC), serves as a centralized management interface to help you effectively administer and monitor Transformation Hub and the SmartConnectors. Fusion ArcMC communicates with the Platform by connecting to the virtual IP address or fully qualified domain name (FQDN) assigned to the primary master node in the cluster. You can configure Fusion ArcMC to manage another instance of Fusion ArcMC or to manage the standalone ArcMC product. Note that, although a standalone instance of ArcMC can manage other standalone instances of ArcMC, it cannot manage Fusion ArcMC.
Fusion includes ArcSight SOAR, a licensed Security Orchestration, Automation and Response Platform that combines orchestration of both technology and people, automation, and incident management into a seamless experience. You can connect the dots between people, process, and technology in SecOps with various and diverse forms of automation, analyst augmentation, and collaborative investigation and response. With 120+ integrations from different vendors, SOAR provides a single pane of glass for security operations and speeds up the incident response process. To use SOAR's capabilities, you must deploy the ESM, Intelligence, or Recon capability, or any combination of these capabilities.
For more information about Fusion, see the following topics:
Intelligence
ArcSight Intelligence provides a market-leading analytics platform, using unsupervised online machine learning to identify unknown threats like insider threats or targeted outside attacks such as APTs. These types of threats simply cannot be identified by searching for a known “bad signature.” Unsupervised machine learning gives threat hunters a high-quality set of leads to help them identify these elusive threats. The analytics platform in ArcSight Intelligence uses:
- ArcSight SmartConnectors
- Supporting Active Directory/Authentication data
- Web proxy data
- Additional data sources
In addition, you can use FlexConnectors to pull ArcSight Intelligence analytical results and push them into ESM for higher accuracy correlation rules that leverage unsupervised learning anomalies, as well as correlation rule filtering using top risky entity lists.
If you deploy ArcSight ESM Web App (ESM Command Center) and Layered Analytics in the same cluster as the ArcSight Intelligence capability, certain widgets will combine data from ESM and ArcSight Intelligence to provide you greater insight into events and entity behavior. This capability requires the Fusion and Transformation Hub capabilities to be deployed in the same cluster, and the ArcSight Database.
For more information about Intelligence, see the following topics:
Layered Analytics
Layered Analytics blends the analytics results from the ArcSight ESM Web App (ESM Command Center) and Intelligence capabilities, thus providing multiple layers of useful data that can lead to actionable insights.
This capability requires the ESM Command Center and Intelligence capabilities.
Recon
ArcSight Recon, also known as Log Management and Compliance, is a licensed product that enables you to search, analyze, and visualize machine-generated data gathered from web sites, applications, sensors, and devices that make up your monitored network. Recon indexes the events from your data source so that you can view and search them. The intuitive search language makes it easy to formulate queries. You can use the large set of dashboards and reports available in the Reports Portal to monitor and identify vulnerabilities and threats in your enterprise.
Recon integrates with Transformation Hub for event transport. Recon also can integrate with ESM to receive alerts and start the investigation process. This capability requires the Fusion and Transformation Hub capabilities to be deployed in the same cluster, and the ArcSight Database.
For more information about Recon, see the following topics:
Transformation Hub
Transformation Hub is a licensed product that lets you take advantage of scalable, high-throughput, multi-broker clusters for publishing and subscribing to event data. It coordinates and manages data streams, which enables your environment to scale, and opens events to third-party data solutions.
Transformation Hub ingests, enriches, normalizes, then routes event data from data producers to connections between existing data lakes, analytics platforms, and other security technologies and the multiple systems within the Security Operations Center (SOC).
Transformation Hub can seamlessly broker data from any source and to any destination. Its architecture is based on Apache Kafka and it supports native Hadoop Distributed File System (HDFS) capabilities, enabling both the ArcSight Logger and ArcSight Recon technologies to push to HDFS for long-term, low-cost storage. This architecture reduces the overall ArcSight infrastructure footprint, scales event ingestion using built-in capabilities, and greatly simplifies upgrades to newer Transformation Hub releases. It also positions the Platform to support an analytics streaming plug-in framework, supporting automated machine learning and artificial intelligence engines for data source onboarding, event enrichment, and detection and attribution of entities and actors.
This capability requires Fusion to be deployed in the same cluster.
For more information about Transformation Hub, see the following topics: