 previous
previous
 next
next
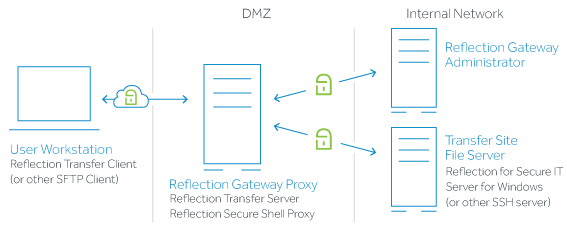
Transfer Sites provide a secure way to manage file exchange. Secure authentication and encryption are used for all connections.
The main components for Transfer Sites are:
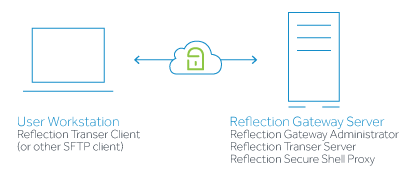
User workstation
Users can transfer files using the web-based Reflection Transfer Client or an alternate SFTP client.
Reflection Gateway Proxy
The following two services always run on the same server. These services are installed together when you install the Reflection Gateway Proxy feature.
Reflection Transfer Server: Provides the Transfer Client web application and communicates with the Reflection Gateway Administrator for user authentication and Transfer Site configuration information.
Reflection Secure Shell Proxy: Manages Secure Shell file transfers to and from the designated Transfer Site file server.
Reflection Gateway Administrator
The Gateway Administrator service maintains user and transfer data and provides a web-based tool for provisioning users and configuring transfers. You can use it to provide access to external users (such as customers or business partners), as well as to allow access to remote employees (users with domain accounts in Active Directory who are working outside your firewall).
Transfer Site file server
In the simplest configuration, you upload and download files to and from the Reflection Gateway Proxy. However, in most cases you will want to store files securely behind your firewall. You can configure to transfer files to and from a designated file server. This can be a Windows system running the Reflection for Secure IT server (included with Reflection Gateway) or any other SFTP-enabled SSH server.
NOTE:The configuration diagrams in this section show only the components required for Transfer Sites. If you are setting up for both Jobs and Transfer Sites, review Reflection for Secure IT Gateway Components to see how to include Job components in your planning.
The simplest configuration for Transfer Sites has only two components – the user workstation and the Reflection Gateway server. All Reflection Gateway services are located on a single server, and files are transferred to and from this server. This configuration can be helpful for initial testing even if your final plans involve a more complex configuration.
A typical distributed configuration is shown below. This configuration supports secure file exchange with users outside your network. Files are transferred through a proxy in the DMZ to a Transfer Site file server behind the firewall. In this configuration, the Reflection Gateway Administrator (which manages user and transfer configuration) also runs securely in the internal network.