1.8 Setting Up Firewalls
It is recommended to use Access Manager with firewalls. Figure 1-10 illustrates a simple firewall setup for a basic Access Manager configuration of an Identity Server, an Access Gateway, and an Administration Console. This is one of many possible configurations.
Figure 1-10 Access Manager Components between Firewalls

The first firewall separates Access Manager from the Internet, allowing browsers to access the resources through specific ports.The second firewall separates Access Manager components from web servers they are protecting and from Administration Console.
This section describes the following topics:
1.8.1 Required Ports
List of Tables
-
Table 1-2, When a Firewall Separates an Access Manager Component from a Global Service
-
Table 1-3, When a Firewall Separates Administration Console from a Component
-
Table 1-4, When a Firewall Separates Identity Server from a Component
-
Table 1-5, When a Firewall Separates Access Gateway from a Component
-
Table 1-6, When a Firewall Separates Analytics Server from Administration Console or any Services
Table 1-2 When a Firewall Separates an Access Manager Component from a Global Service
|
Component |
Port |
Description |
|---|---|---|
|
NTP Server |
UDP 123 |
Access Manager components must have time synchronized else the authentication fails. It is recommended to configure all components to use an network time protocol (NTP) server. Depending upon where your NTP server is located, you might need to open UDP 123, so that Access Manager components can use the NTP server. |
|
DNS Servers |
UDP 53 |
Access Manager components must be able to resolve DNS names. Depending upon where your DNS servers are located, you might need to open UDP 53, so that Access Manager components can resolve DNS names. |
|
Remote Administration Workstation |
TCP 22 |
If you want to use SSH for remote administration of Access Manager components, open TCP 22 to allow. |
Table 1-3 When a Firewall Separates Administration Console from a Component
|
Component |
Port |
Description |
|---|---|---|
|
Access Gateway, Identity Server |
TCP 1443 |
For communication from Administration Console to devices. |
|
TCP 8444 |
For communication from devices to Administration Console. |
|
|
TCP 1290 |
For communication from devices to the syslog server on Administration Console. |
|
|
TCP 524 |
For NCP certificate management with NPKI. Open this port so that both the device and Administration Console can use the port. |
|
|
TCP 636 |
For secure LDAP communication from devices to Administration Console. |
|
|
HTTP 2443 HTTP 8443 |
For the installer to communicate with Administration Console. You can close these port after installation is complete. |
|
|
Importing an Access Gateway Appliance |
ICMP |
During an import, Access Gateway Appliance sends two pings through ICMP to Administration Console. When the import has finished, you can disable the ICMP echo requests and echo replies. |
|
LDAP User Store |
TCP 524 |
Required only if the user store is eDirectory. When configuring a new eDirectory user store, NCP is used to enable Novell SecretStore by adding a SAML authentication method and storing a public key for Administration Console. It is not used in day-to-day operations. |
|
TCP 636 |
For secure LDAP communication from Administration Console to user store. |
|
|
Administration Console |
TCP 524 |
Required to synchronize the configuration data store. |
|
TCP 636 |
Required for the secure LDAP communication. |
|
TCP 8080, 8443 |
Used for the Tomcat communication. |
|
TCP 705 |
Used by Sub Agent-Master Agent communication inside Administration Console. |
|
|
UDP 161 |
Used for communication by an external Network Monitoring System with Administration Console by using SNMP. |
|
|
Browsers |
TCP 8080 |
For HTTP communication from browsers to Administration Console. |
|
TCP 8443, 2443, 2080 |
For HTTPS communication from browsers to Administration Console. NOTE:2443 and 2080 are optional ports required when Administration Console and Identity Server are collocated. |
|
|
TCP 8028, 8030 |
To use iMonitor or DSTrace from a client to view information about the configuration store on Administration Console. |
|
|
Upgrade Assistant Agent |
TCP 9968 |
For HTTPS communication from Upgrade Assistant agent to Administration Console. |
Table 1-4 When a Firewall Separates Identity Server from a Component
|
Component |
Port |
Description |
|---|---|---|
|
Access Gateway |
TCP 8080 or 8443 |
For authentication communication from Access Gateway to Identity Server. The default ports for Identity Server are TCP 8080 and 8443. They are configurable. You need to open the port that you configured for the base URL of Identity Server. |
|
TCP 80 or 443 |
For communication from Identity Server to Access Gateway ESP. This is the reverse proxy port that is assigned to be ESP (see the Reverse Proxy /Authentication page). This is usually port 80 or 443. |
|
|
Administration Console |
TCP 1443 |
For communication from Administration Console to devices. This is configurable. |
|
TCP 8444 |
For communication from Identity Server to Administration Console. |
|
|
TCP 8443 |
For Docker deployment. |
|
|
TCP 1290 |
For communication from devices to the Syslog server on Administration Console. |
|
|
TCP 524 |
For NCP certificate management with NPKI from Identity Server to Administration Console. |
|
|
TCP 636 |
For the secure LDAP communication from Identity Server to Administration Console. |
|
|
Identity Server |
TCP 8443 or 443 |
For HTTPS communication. You can use iptables to configure this for TCP 443. See Translating Identity Server Configuration Port. |
|
TCP 7801 |
For back-channel communication with cluster members. You must enable the multicast traffic on this port. This port is configurable. NOTE:For Docker deployment, use TCP port 7901. |
|
|
LDAP User Stores |
TCP 636 |
For secure LDAP communication from Identity Server to the LDAP user store. |
|
Service Providers |
TCP 8445 |
If you have enabled identity provider introductions, open a port to allow HTTPS communication from the user’s browser to the service provider. |
|
TCP 8446 |
If you have enabled identity provider introductions, open a port to allow HTTPS communication from the user’s browser to the service consumer. |
|
|
Browsers |
TCP 8080 |
For HTTP communication from a browser to Identity Server. You can use iptables to configure this for TCP 80. SeeTranslating Identity Server Configuration Port. |
|
TCP 8443 |
For HTTPS communication from a browser to Identity Server. You can use iptables to configure this for TCP 443. See Translating Identity Server Configuration Port. |
|
|
CRL and OCSP Servers |
Configurable |
If you are using x.509 certificates that include an AIA or CRL Distribution Point attribute, you need to open the port required to talk to that server. Ports 80/443 are the most common ports, but the LDAP ports 389/636 can also be used. |
|
Active Directory Server with Kerberos |
TCP 88, UDP 88 |
For communication with KDC on the Active Directory Server for Kerberos authentication. |
|
Upgrade Assistant Agent |
TCP 9968 |
For HTTPS communication from Upgrade Assistant agent to Identity Server. |
Table 1-5 When a Firewall Separates Access Gateway from a Component
|
Component |
Port |
Description |
|---|---|---|
|
Identity Server |
TCP 8080 or 8443 |
For authentication communication from Access Gateway to Identity Server. The default ports are TCP 8080 and 8443, which are configurable. You need to open the port of the base URL of Identity Server. |
|
TCP 80 or 443 |
For communication from Identity Server to ESP of Access Gateway. This is the reverse proxy port that is assigned to be ESP (see the Reverse Proxy /Authentication page). This is usually port 80 or 443. |
|
|
Administration Console |
TCP 1443 |
For communication from Administration Console to Access Gateway. This is configurable. |
|
TCP 8444 |
For communication from Access Gateway to Administration Console. |
|
|
TCP 1290 |
For communication from devices to the Syslog server on Administration Console. |
|
|
TCP 524 |
For NCP certificate management with NPKI from Access Gateway to Administration Console. |
|
|
TCP 636 |
For secure LDAP communication from Access Gateway to Administration Console. |
|
|
Access Gateway |
TCP 7801 |
For back-channel communication with cluster members. You must enable the multicast traffic option on this port. This port is configurable. It is set by Identity Server cluster configuration that Access Gateway trusts. See Configuring a Cluster with Multiple Identity Servers in the NetIQ Access Manager 5.0 Administration Guide. |
|
TCP 80 or 443 |
For communication among Embedded Service Providers (ESP) of the Access Gateway cluster members. This is the reverse proxy port that is assigned to be ESP (see the Reverse Proxy /Authentication page). This is usually port 80 or 443. This port is configurable. |
|
|
Access Gateway Appliance Configuration console (https://<access_gateway_appliance-IP address>:9443) |
TCP 9090 or 9443 |
For using the Jetty service on the appliance Configuration console. For information about the Configuration console, see Configuring Access Gateway Appliance. |
|
TCP 1099 |
For the Java RMI communication. |
|
|
Browsers/Clients |
TCP 80 |
For HTTP communication from the client to Access Gateway. This is configurable. |
|
TCP 443 |
For HTTPS communication from the client to Access Gateway. This is configurable. |
|
|
Web Servers |
TCP 80 |
For HTTP communication from Access Gateway to web servers. This is configurable. |
|
TCP 443 |
For HTTPS communication from Access Gateway to web servers. This is configurable. |
|
|
Upgrade Assistant Agent |
TCP 9968 |
For HTTPS communication from Upgrade Assistant agent to Access Gateway. |
Table 1-6 When a Firewall Separates Analytics Server from Administration Console or any Services
|
Component |
Port |
Description |
|---|---|---|
|
Administration Console |
TCP 1444 |
For communication between Administration Console and Analytics Server. |
|
Browsers |
TCP 8445 |
For HTTPS communication with Analytics Server for Access Manager Dashboard. |
|
Syslog |
TCP 1468 |
For sending Syslog messages from Access Manager components to Analytics Server. |
|
Docker |
TCP 2443 |
For Docker deployment. |
|
Remote Administration Workstation |
TCP 22 |
For communication from your remote administration workstation to Analytics Server. |
|
Upgrade Assistant Agent |
TCP 9968 |
For HTTPS communication from Upgrade Assistant agent to Administration Console or any services. |
NOTE:On SLES, you can use YaST to configure UDP ports and internal networks.
Table 1-7, Table 1-8, and Table 1-9 are intended for use in configuring the security groups in cloud deployments. The security groups, by default, do not restrict the outbound ports. Therefore, these tables include only the inbound ports.
Table 1-7 Administration Console on Cloud
|
Component |
Port |
Traffic Direction |
Description |
|---|---|---|---|
|
Access Gateway, Identity Server |
TCP 1290 |
Inbound |
For communication from devices to the Syslog server on Administration Console. |
|
TCP 2443 |
Inbound |
For the installer to communicate with Administration Console. |
|
|
TCP 8444 |
Inbound |
For communication from devices to Administration Console. |
|
|
TCP 524 |
Inbound |
For NCP certificate management with NPKI. Open this port so that both the device and Administration Console can use the port. |
|
|
TCP 636 |
Inbound |
For secure LDAP communication from devices to Administration Console. |
|
|
Access Gateway |
TCP 1289 |
Inbound |
For importing Access Gateway into Administration Console. |
|
SSH |
TCP 22 |
Inbound |
For accessing Administration Console using SSH. |
|
Access Gateway |
ICMP |
Inbound |
For importing Access Gateway. |
|
Upgrade Assistant Agent |
TCP 9968 |
Inbound |
For HTTPS communication from Upgrade Assistant agent to Administration Console on Cloud. |
Table 1-8 Identity Server on Cloud
|
Component |
Port |
Traffic Direction |
Description |
|---|---|---|---|
|
Administration Console |
TCP 1443 |
Inbound |
For communication from Administration Console to devices. This is configurable. |
|
TCP 524 |
Inbound |
For NCP certificate management with NPKI from Identity Server to Administration Console. |
|
|
Identity Server |
TCP 7801 |
Inbound |
For the back-channel communication with cluster members. You must enable the multicast traffic option on this port. This port is configurable. |
|
SSH |
TCP 22 |
Inbound |
For accessing Identity Server using SSH. |
|
Access Gateway, Browsers |
TCP 8443 |
Inbound |
For authentication communication from Access Gateway to Identity Server. For HTTPS communication from a browser to Identity Server's base URL when the default ports are used. |
|
Upgrade Assistant Agent |
TCP 9968 |
Inbound |
For HTTPS communication from Upgrade Assistant agent to Identity Server on Cloud. |
Table 1-9 Access Gateway on Cloud
|
Component |
Port |
Traffic Direction |
Description |
|---|---|---|---|
|
Service Providers |
TCP 8445 |
Inbound |
If you have enabled identity provider introductions, open a port to allow HTTPS communication from the user’s browser to the service provider. |
|
TCP 8446 |
Inbound |
If you have enabled identity provider introductions, open a port to allow HTTPS communication from the user’s browser to the service consumer. |
|
|
Access Gateway |
TCP 7801 |
Inbound |
For back-channel communication with cluster members. You must enable the multicast traffic option on this port. |
|
Administration Console |
TCP 1443 |
Inbound |
For communication from Administration Console to Access Gateway. This is configurable. |
|
SSH |
TCP 22 |
Inbound |
For accessing Administration Console using SSH. |
|
Identity Server |
TCP 80 or 443 |
Inbound |
For communication from Identity Server to Access Gateway ESP. This is the reverse proxy port that is assigned to be ESP. |
|
Browsers/Clients |
TCP 443 |
Inbound |
For HTTPS communication from workstation browsers to Access Gateway. |
|
TCP 80 |
Inbound |
For HTTP communication from workstation browsers to Access Gateway. |
|
|
Upgrade Assistant Agent |
TCP 9968 |
Inbound |
For HTTPS communication from Upgrade Assistant agent to Access Gateway on Cloud. |
The following syslog ports for Docker are configured for Access Gateway, Administration Console, and Identity Server so they are unique and do not conflict:
Table 1-10 Syslog Ports on Docker
|
Ports for Administration Console |
Ports for Access Gateway |
Ports for Identity Server |
|---|---|---|
|
1290 |
1490 |
1390 |
|
1291 |
1491 |
1391 |
|
1292 |
1492 |
1392 |
1.8.2 Restricted Ports
The following ports are reserved for internal use only and other applications should not use these:
- 22
- 111
- 524
- 1443
- 2443
- 3443
- 8028
- 8030
- 8080
- 8443
- 8444
- 9000
- 9001
- 55982
- 61222
- 61613
- 61616
- 61617
- 9443
- 9090
If required, use port redirection by using IP tables.
1.8.3 Sample Configurations
Access Gateway and Identity Server in DMZ
First Firewall
If you place a firewall between browsers and Access Gateway and Identity Server, you need to open ports so that the browsers can communicate with Access Gateway and Identity Server and Identity Server can communicate with other identity providers.
See, Figure 1-10
Table 1-11 Ports to Open in the First Firewall
|
Port |
Purpose |
|---|---|
|
TCP 80 |
For HTTP communication. |
|
TCP 443 |
For HTTPS communication. |
|
Any TCP port assigned to a reverse proxy or tunnel. |
|
|
TCP 8080 |
For HTTP communication with Identity Server. For information about redirecting Identity Server to use port 80, see Translating Identity Server Configuration Port. |
|
TCP 8443 |
For HTTPS communication with Identity Server. For information about redirecting Identity Server to use port 443, see Translating Identity Server Configuration Port. |
|
TCP 8445 |
For HTTP Identity Provider introductions. If you do not enable Identity Provider introductions, you do not need to open this port. |
|
TCP 8446 |
For HTTPS Identity Provider introductions. If you do not enable Identity Provider introductions, you do not need to open this port. |
Second Firewall
The second firewall separates web servers, LDAP servers, and Administration Console from Identity Server and Access Gateway. You need the following ports opened in the second firewall:
Table 1-12 Ports to Open in the Second Firewall
|
Port |
Purpose |
|---|---|
|
TCP 80 |
For HTTP communication with web servers. |
|
TCP 443 |
For HTTPS communication with web servers. |
|
Any TCP connect port assigned to a web server or to a tunnel. |
|
|
TCP 1443 |
For communication from Administration Console to the devices. |
|
TCP 8444 |
For communication from the devices to Administration Console. |
|
TCP 1290 |
For communication from the devices to the Syslog server installed on Administration Console. If you do not enable auditing, you do not need to open this port. |
|
TCP 524 |
For NCP certificate management in NPKI. The port needs to be opened so that both the device and Administration Console can use the port. |
|
TCP 636 |
For secure LDAP communication of configuration information. |
A Firewall Separating Access Manager Components from the LDAP Servers
You can configure Access Manager components so that your Administration Console is on the same side of the firewall as your Access Manager components and have a firewall between them and the LDAP servers.
Figure 1-11 A Firewall Separating Administration Console and the LDAP Server
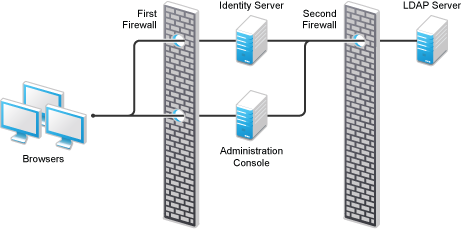
In this configuration, you need to open the following ports in the second firewall for Administration Console and Identity Server:
Table 1-13 Ports to Open in the Second Firewall
|
Ports |
Purpose |
|---|---|
|
TCP 636 |
For secure LDAP communication. This is used by Identity Server and Administration Console. |
|
TCP 524 |
For configuring eDirectory as a new User Store. NCP is used to enable SecretStore by adding a SAML authentication method and storing a public key for Administration Console. During day-to-day operations, this port is not used. If your LDAP server is Active Directory, this port does not need to be opened. |