5.1 Understanding Federated SSO with SAML 2.0
To understand the federated single sign-on process with Access Manager, you must understand SAML 2.0.
5.1.1 Understanding SAML 2.0
SAML is an XML-based framework for communicating user authentication, entitlement, and attribute information. For more information see, Security Assertion Markup Language (SAML) V2.0 Technical Overview.
SAML 2.0 creates a two-way agreement between two vendors asserting that the information provided is valid. It provides a standard framework to share this information, so you do not need to recreate the configuration for every vendor you want to share information.
To use the SAML 2.0 connectors provided for Access Manager, you must understand the basic concepts and components of SAML 2.0.
SAML 2.0 defines each of the components using the XML schema. You must be able to read and format documents in XML to use SAML 2.0 connectors.
XML-based framework: You must understand the XML format, structure, elements, and how it defines rules for encoding documents. For more information, see Introduction to XML on the w3schools website.
Assertion: SAML assertions define the syntax for creating XML-encoded assertions to describe authentication, attribute, and authorization information for an entity. The SAML 2.0 connectors help create the assertions for Access Manager and the federation applications.
Attributes: LDAP attributes passed between two entities. In this case, it is LDAP attributes passed between Access Manager and connected federation applications.
Metadata: Metadata defines how SAML 2.0 shares configuration information between two communicating entities. You must be able to access and share the Access Manager metadata information with the federated application. You must also be to access and share the federated application metadata with Access Manager
Protocols: SAML 2.0 supports HTTP, HTTPS, and SOAP protocols. SAML 2.0 connectors use HTTPS to establish a secure connection between Access Manager and federated applications. To establish a secure HTTPS connection, you must obtain the certificate from the metadata of Access Manager and the application. Each side then uses the other side’s certificate to create the secure connection
5.1.2 Understanding SAML 2.0 Federated SSO Processes with Access Manager
Federated SSO relies on a trust relationship between an identity provider and a service provider to give users access to web services or applications.
SAML 2.0 is an open standard for federation that provides a vendor-neutral means of exchanging user identity, authentication, attribute information, and authorization information. SAML 2.0 defines the structure and content of assertions and protocol messages used to transfer this information between Access Manager and the web services or applications (service providers). For more information about SAML 2.0, see Section 5.1.1, Understanding SAML 2.0.
Using a SAML 2.0 connection, the service provider (web services or applications) trusts the identity provider (Access Manager) to validate the user’s authentication credentials and to send identity information about the authenticated user. The service provider accepts the data and uses it to give the user access to the web service or application. This data exchange is transparent for the user. It allows the user to access the web service or application without providing additional credentials.
Figure 5-1 illustrates how a SAML SSO authentication works with Access Manager:
Figure 5-1 Access Manager SSO with SAML 2.0
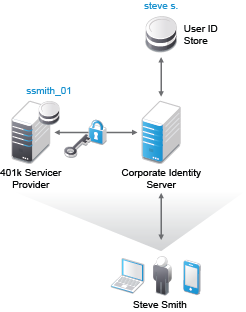
-
The user Steve Smith authenticates to the corporate Identity Server (Access Manager) with his corporate user name and password.
-
Access Manager authenticates Steve against the user name steve s. and associated password in the user store.
-
Steve accesses User Portal with an appmark to the 401k application that he is entitled to use.
-
When Steve clicks the 401k appmark, Access Manager produces an authentication assertion or token for the 401k application (service provider) that contains the identity attributes needed for authentication.
-
The 401k application consumes the assertion or token to establish a security context for the user with Access Manager.
-
The 401k application uses the assertion or token to validate that steve s. is ssmith_01 and authorizes the authentication (resource request).
-
The 401k application establishes a session with Steve.
Access Manager now provides a simpler means of creating the SAML 2.0 federation for SSO by providing connectors for specific applications. When you use the connectors, Access Manager automatically creates an appmark for the web service or application and places the appmark on the User Portal page for users to access. You can limit access to the SAML 2.0 web service or application by using role assignments configured on the Applications page. You can limit visibility of the SAML 2.0 appmarks on the User Portal page by using role assignments configured on the appmarks.
Access Manager allows you to convert the existing SAML 2.0 service providers to applications that you can manage from the Applications page. The benefit of conversion is to add the ability to configure access control to the application using roles. For more information, see Section 5.5, Converting SAML 2.0 Service Providers in to a SAML 2.0 Application.