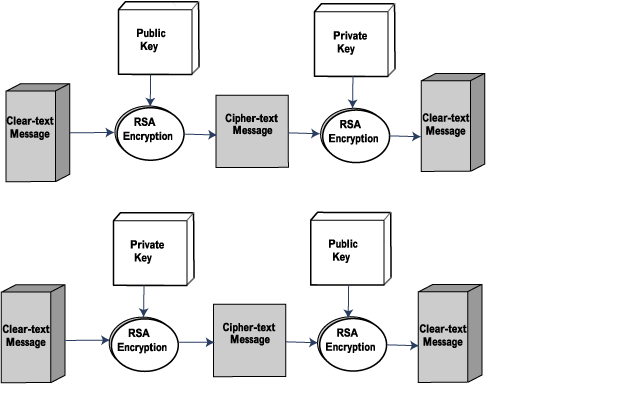
In addition to username/password-based authentication, VisiSecure also supports public-key encryption. In public-key encryption, each user holds two keys: a public key and a private key. A user makes the public key widely available, but keeps the private key secret.
Data that has not been encrypted is often referred to as clear-text, while data that has been encrypted is called cipher-text. When a public key and a private key are used with the public-key encryption algorithm, they perform inverse functions of one another, as shown in the following diagram.
When you distribute your public key, the recipients of that key need some sort of assurance that you are indeed who you claim to be. The ISO X.509 standard defines a mechanism called a certificate, which contains a user's public key that has been digitally signed by a trusted entity called a Certificate Authority (CA). When a client application receives a certificate from a server, or vice-versa, the CA that issued the certificate can be used to verify that it did indeed issue the certificate. The CA acts like a notary and a certificate is like a notarized document.
A distinguished name represents the name of a user or the CA that issued the user's certificate. When you submit a certificate request, it includes a distinguished name for the user that is made up of the components listed in the following table.
|
2
|
Since the Acme CA is not in Joe's certificate chain, Joe obtains the issuer of the certificate for CA_2.
|
|
3
|
Because CA_2 is not a trusted CA, the server decides whether to accept or reject the connection.
|
VisiSecure uses Java Secure Sockets Extension (JSSE) to perform SSL communication. VisiSecure SPI Secure Socket Provider class provides access to the underlying SSL implementation. Any appropriate implementation following Java Secure Socket Extension (JSSE) framework can be easily plugged in, independent of other provider mechanisms. The only necessary step is mapping the interfaces (or, in other words, callback methods) defined to the corresponding JSSE implementation. For more information on the SPI Secure Socket Provider class, see VisiSecure SPI for Java and “Security SPI for C++”.
The list of supported cipher suites for VisiSecure is determined by the underlying security implementation. For VisiSecure for Java, this is the JSSE package used, which in turn depends on the version and manufacturer of the JDK used. For VisiSecure for C++, it depends whether you are using the Certicom or the MFCryptLib/OpenSSL security provider (see “Specifying the Security Provider”); in either case you can find the list of supported ciphers in the <install_dir>/include/csstring.h file, or by using the ssl::CipherSuiteInfoList* listAvailableCipherSuites() API.
OpenSSL supports many pre-defined ECC curves (also known as 'named curves' or ‘elliptic curves’), used in ECDH and ECDHE ciphers. A complete list of the supported named curves can be obtained by executing the following command, using the openssl utility (in this example, for RedHat Linux):
The list of supported curves that may be used with the vbroker.security.server.socket.ecdheCurve property is as follows:
If no elliptic curve key is detected, the ECDHE_RSA cipher suites require that an elliptic curve is chosen to create the ECDHE temporary keys that will be used in the session. The ECDHE_RSA curve will be selected automatically. However you can also use the new server-side property vbroker.security.server.socket.ecdheCurve to set the curve that will be used for ECDHE cipher suites. The value of this property is a comma-separated list of curves, each of which must match one of the well-known elliptic curves as defined by IANA (the Internet Assigned Numbers Authority) for use with TLS.
|
•
|
secp192r1 (also listed as prime192v1)
|
|
•
|
prime256v1 (also listed as secp256r1)
|
If secp192r1 is specified, prime192v1 will appear in the logs; these names indicate the same curve. Similarly, if prime256v1 is specified, secp256r1 will appear.
A previous ANSI X9.62 standard, Public Key Cryptography For The Financial Services Industry, defined some of the same curves as the IANA list, but with different names. Where this occurs either name can be used in the VisiBroker configuration.
|
•
|
|
•
|
ORB and all its C++ services use a special Logger instance (the ‘Default Logger’ with the name “default”), which is created automatically the first time the ORB logs a message. For more information, refer to the chapter on ‘VisiBroker logging’ in the VisiBroker for C++ Developer’s Guide.
SimpleLogger class is a mechanism to log information of various levels. Currently, it supports four different levels: LEVEL_WARNING, LEVEL_NOTICE, LEVEL_INFO, and LEVEL_DEBUG, with increasingly detailed information. There is only one logger in the whole security service. For information on the SimpleLogger class, see “vbsec::SimpleLogger”.
The default value is "debug".
The default value is "debug".
|
•
|
An applet using IIOP/HTTPS cannot use the X509Certificate[] class to set or examine identities. All certificate and private key administration is handled by the browser. Furthermore, when the ORBalwaysTunnel parameter in the applet tag is set to true, the ORB cannot resolve SSLCurrent objects.
|
|
•
|
To enable an applet to use only IIOP/HTTPS, set ORBalwaysTunnel to true in the HTML page. If ORBalwaysTunnel is set to false (or unspecified) the ORB first tries to use IIOP/SSL, which requires the SSL classes and native SSL library to be installed locally.
|
|
•
|
GateKeeper, by default, does not ask for the client identity. You can enable this function by setting ssl_request_client_certificate to true in the GateKeeper configuration file.
|
|
•
|
GateKeeper, by default, does not ask for the client identity. Although you can enable this function by setting ssl_request_client_certificate=true in the GateKeeper configuration file, you cannot use IIOP/HTTPS because the browser asks for permission before responding with the user's credentials.
|
Internet Explorer optionally requires the Common Name field within the server certificate to be the same as the host name of the server. From the View > Internet Options menu, select the Advanced tab and scroll to the Security section. Make sure the box next to Warn about invalid site certificates is not checked to use a server certificate that does not contain the host name of the server.