|
•
|
a client always connects through a proxy (vbroker.orb.alwaysProxy)
|
|
•
|
a client always use HTTP-tunneling mode (vbroker.orb.alwaysTunnel)
|
See “Configuring client properties” for details.
See “Configuring client properties” for details.
|
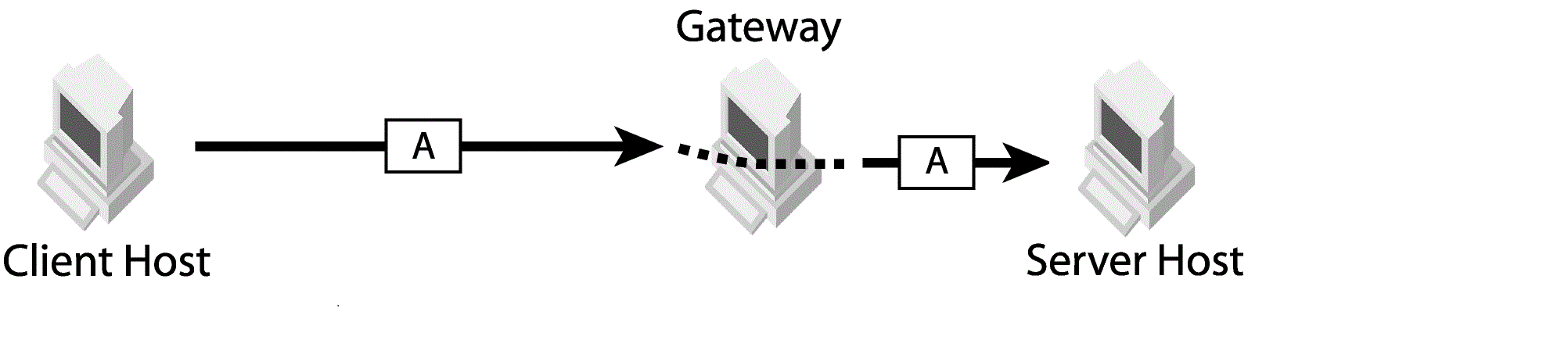
Figure 2
|
|
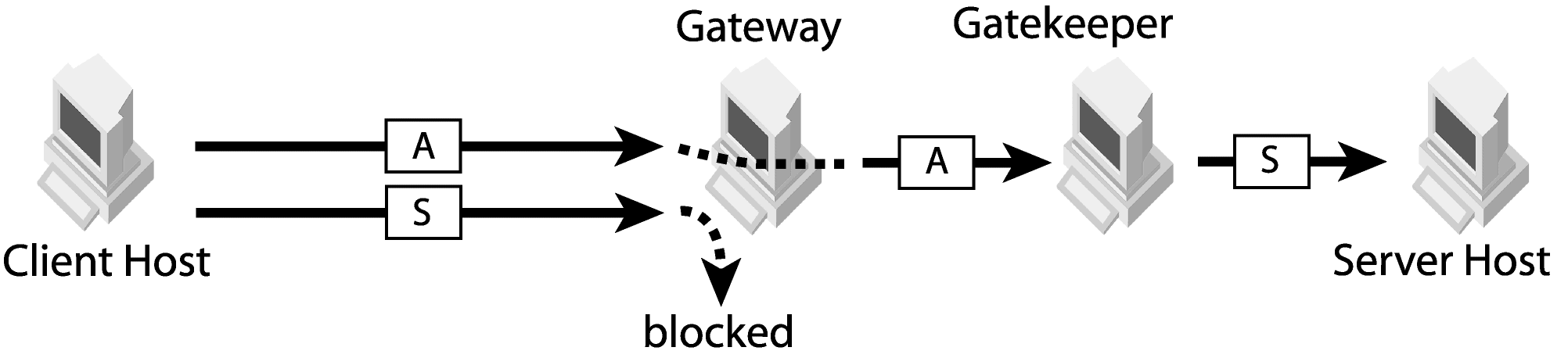
Figure 3
|
|
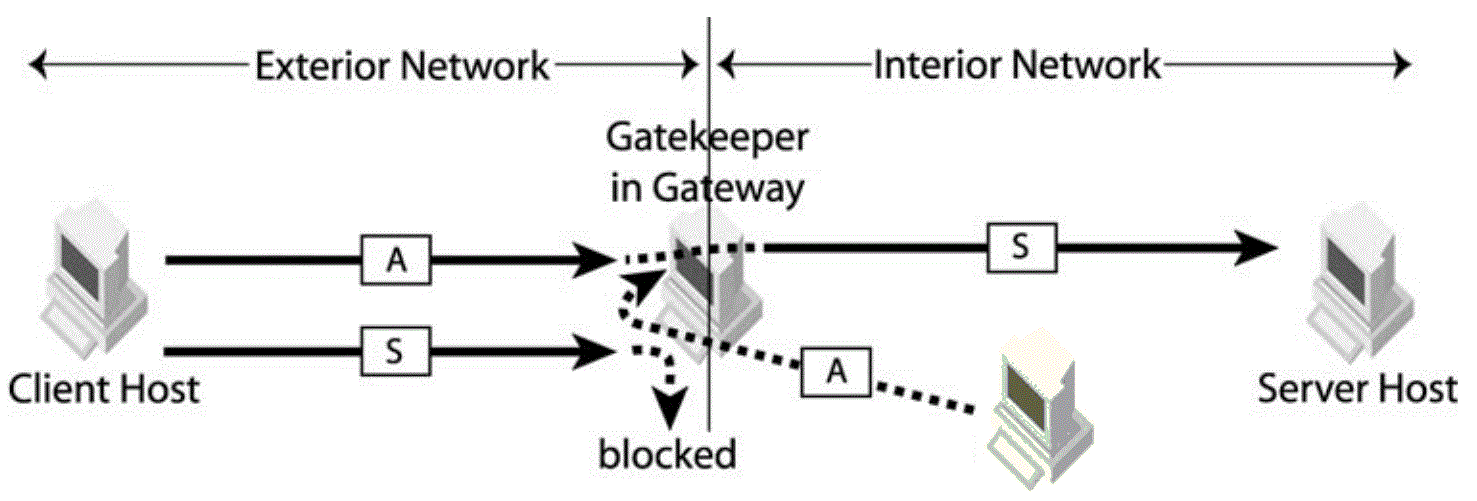
Figure 4
|
|
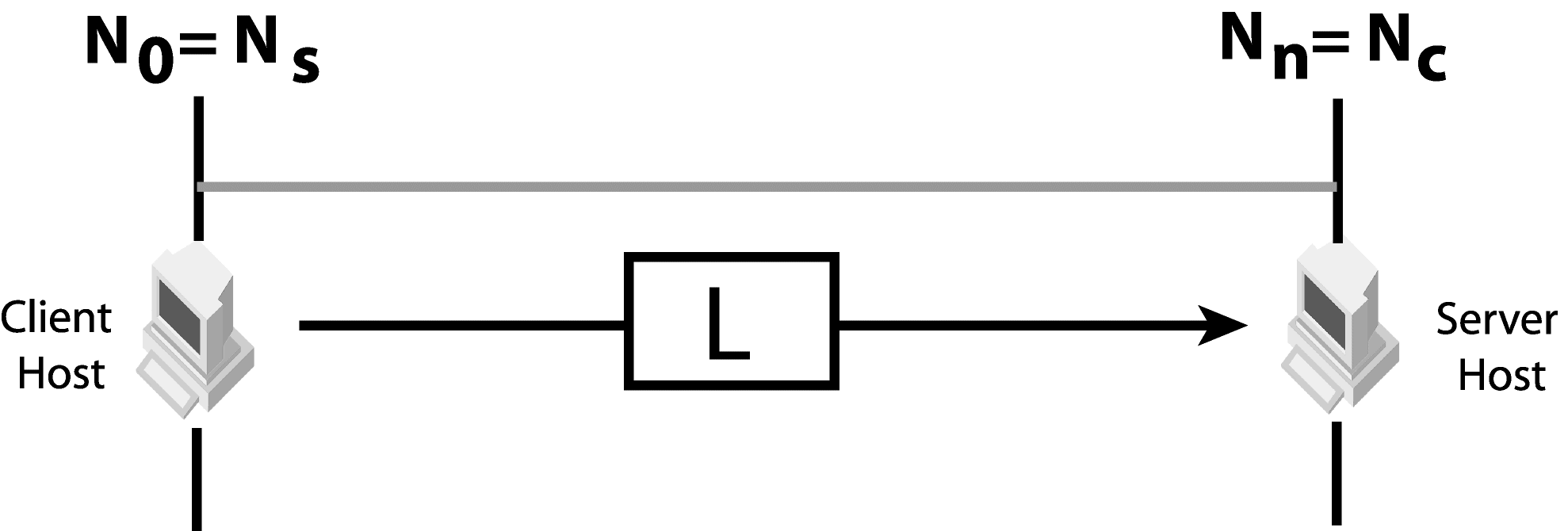
Figure 5
|
|
Figure 6
|
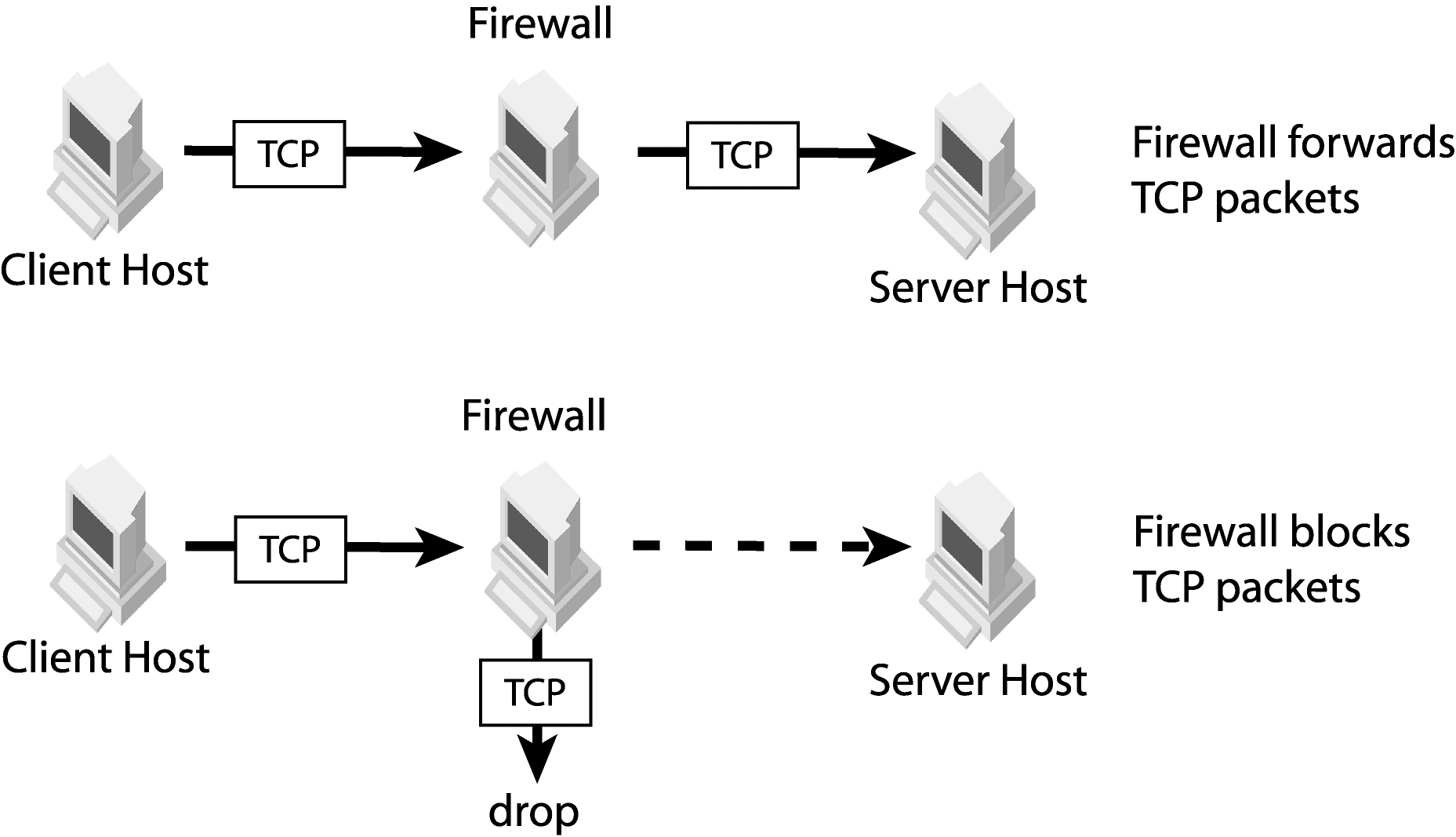
For illustration purposes, the client network will be numbered as N0. The network adjacent to the client network will be numbered as N1, the next adjacent network as N2 and so on until the server network. The server network will be numbered as Nn in the following discussions. Replace n with the actual number depending to the network configuration. Also, the internetworking device between network Nn-1 and Nn is numbered as GWn.
Clients can use different transport types to communicate with servers. Examples of transport types are IIOP, IIOP/SSL, HTTP and HTTPS. For each valid transport type, locate the furthest network that the client message can reach. The client located in network N0 sends a message to network N0. GW1 may or may not forward the message to network N1. The message can reach network N1 if GW1 can forward the message from N0 to N1. Subsequently, GW2 may or may not forward the message to network N2. Traverse the networks starting from the client network, then moving towards the server network. Mark the last network that the message can reach as Nc. In other words, GWc+1 cannot forward the message to the network Nc+1.
A server has one or more listener ports. Each port listens to one type of messages from clients. As an example, a server with an IIOP listener port and an SSL listener port will use the IIOP port to listen to IIOP messages and the SSL port to listen to IIOP over SSL messages. For each listener port, find the furthest network from the server to which a client message can reach the server. Mark the furthest network as Ns. In other words, a client located in network Ns is able to send a message to the server.
If callback for VisiBroker 3.x style is required, an additional condition is required for Nc and Ns. The callback message from the server (from network Nn) must be able to reach the network Ns. When GateKeeper is used, the client must be able to set up a callback communication channel to network Nc.
If the client cannot send messages using transport type L, deploy GateKeeper on a network within N0 and Nc to proxy client messages of other transport types (M) to transport type L. For example, the server listens to IIOP and the client can only communicate using IIOP over HTTP.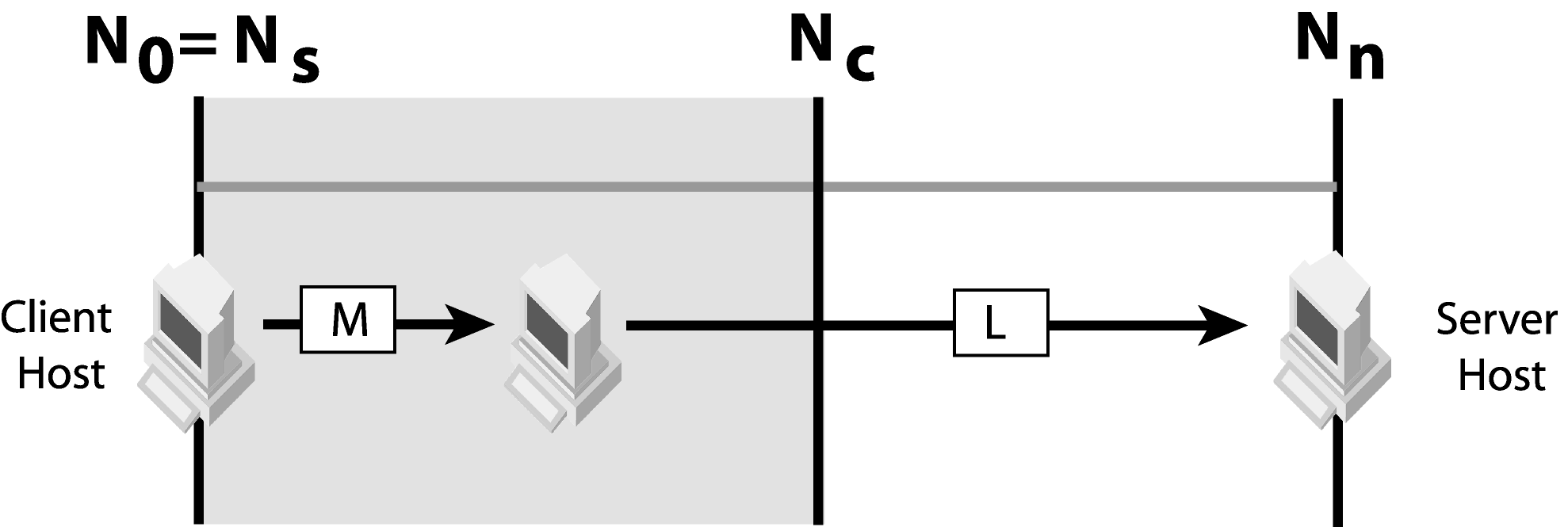

If the server does not listen to the client's message transport type, GateKeeper is required in any network within Ns and Nn. GateKeeper acts as a proxy to relay client messages of type M to one of the server listener types (L). For example, M (client message transport type) is IIOP over HTTP and L (server listener type) is IIOP.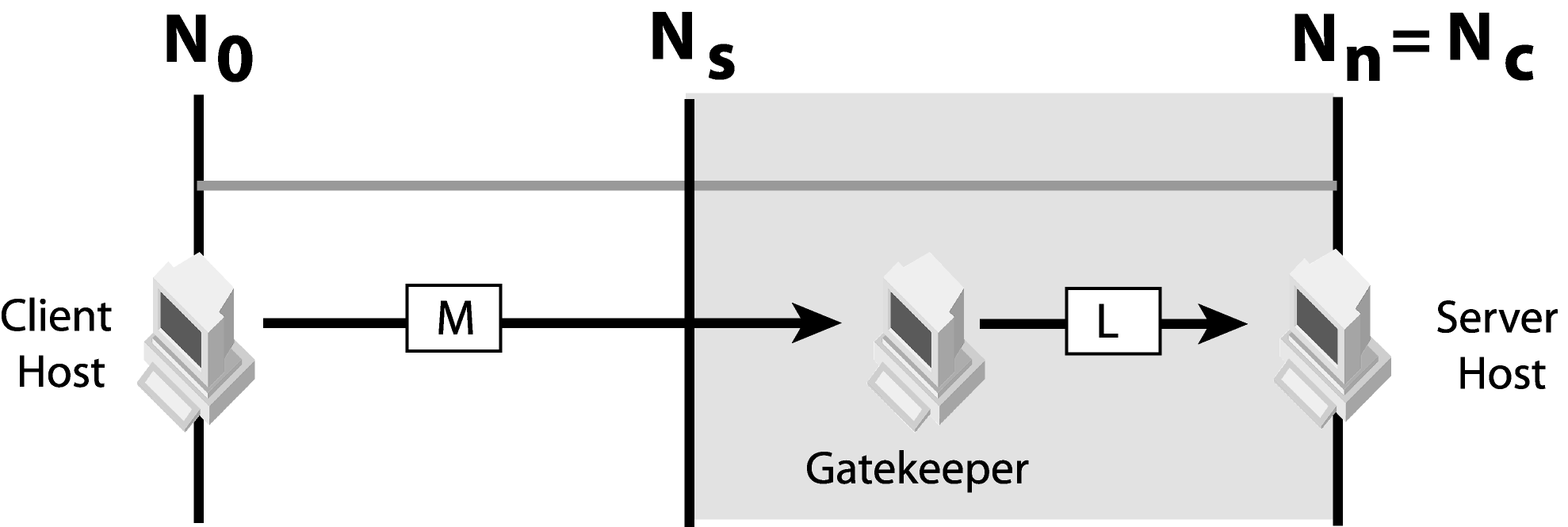

When c >= s, the client transport type (M) and the server listener type (L) must be different. Deploy GateKeeper in any network between Ns and Nc inclusive. In this case, GateKeeper acts as a proxy to relay client messages of type M to the server listener port of type L. As an example, the client's IIOP over HTTP messages can reach the networks up to Nc. IIOP messages sent from any network between Ns and Nn can reach the server. Deploying GateKeeper in between Ns and Nc will help bind the client's IIOP over HTTP messages to the server's IIOP listener port.

Check if GateKeeper chaining is possible or not. See “Chaining of GateKeepers” for details of GateKeeper chaining. GateKeeper chaining is possible only when there is another transport type (K) available for the two GateKeepers to communicate successfully from Nc to Ns. Deploy one GateKeeper on network (Nc) and another GateKeeper on network Ns. After which, chain them together. For example, client sends IIOP over HTTP messages, the server listens to IIOP messages and both GateKeeper instances can use SSL to communicate with each other. The client connects to GateKeeper 1 using HTTP, GateKeeper 1 communicates with GateKeeper 2 using SSL, and GateKeeper 2 communicates with the server using IIOP.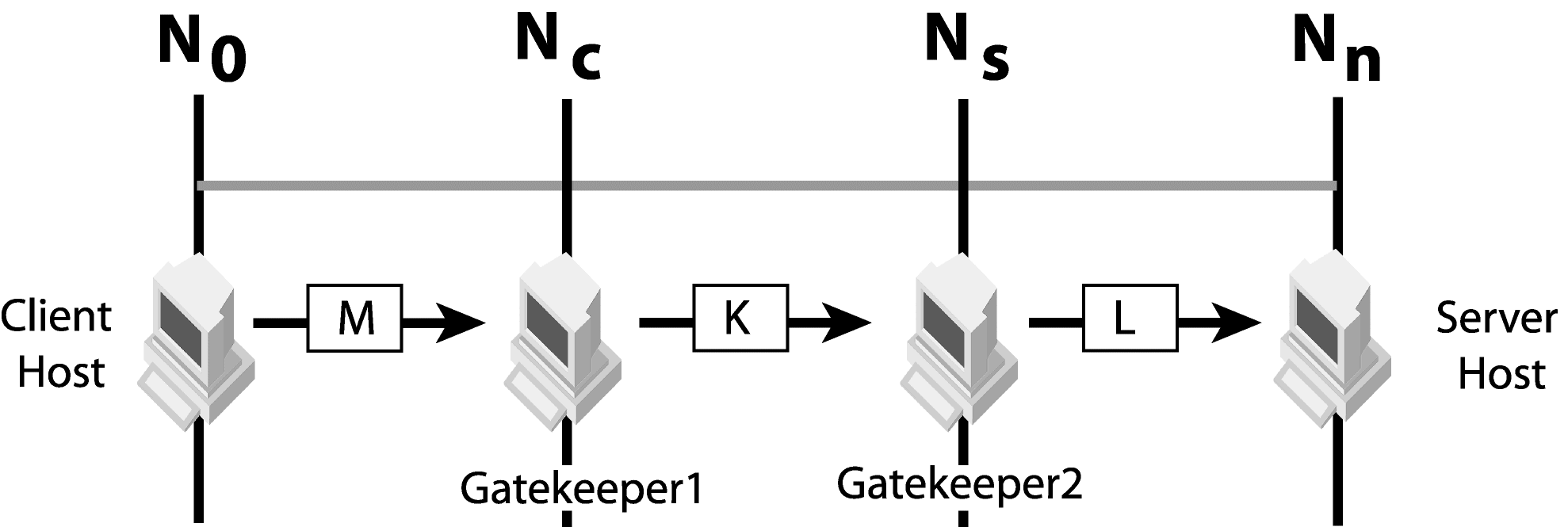

If chaining is not possible, there is no suitable network to deploy GateKeeper. The internetworking devices connecting networks Nc and Ns must be reconfigured so that the appropriate type of messages can be forwarded from Nc to Ns. After which, locate the new Nc and Ns, and refer to the previous cases accordingly.

See “Configuring server properties” for details on how to configure server objects to use TCP firewall with NAT. Be sure that the NAT translation mappings are added into the NAT device for successful communication between client and server objects.
After setting the above properties, GateKeeper activates its interior server engine to receive callback messages from the server. The listener can be configured using the in-iiop and in-ssl SCMs. In addition, a callback listener is activated for a client to establish an additional communication channel for callback messages. See “VisiBroker 3.x style callback” for details on specifying the listener port and additional related information. Be sure the selected ports are reachable from the client and the server by ensuring that these ports are not blocked by any firewalls.
If the client requests a pass-through connection, GateKeeper will not examine any messages that pass between the server and client. When the above property is set to false, GateKeeper binds the client to the server using normal (non-pass-through) connections even when the client requests a pass-through connection. In this case, GateKeeper examines the exchanged messages for routing and binding purposes.
See “Support for pass-through connections” for more information about the above properties.
The first property specifies the host IP address of the Smart Agent. The second property specifies the file that defines a list of hosts running Smart Agents. The third property specifies the OSAGENT_PORT. The default value for the first two properties is null, which tells GateKeeper to contact the Smart Agent running on the same network.
See “Using the Smart Agent” in the VisiBroker Developer's Guide for more details about Smart Agent settings and other methods of setting Smart Agent parameters.
See Using the Object Activation Daemon in the VisiBroker Developer's Guide for more information about OAD.
|
•
|
|
•
|
|
•
|
See “Exterior server engine”, “Interior server engine” and “Administration” for the full list of properties for the above SCMs.
|
•
|
The vbroker.security.disable=false property enables the required security packages into the VisiBroker ORB of the GateKeeper.
|
|
•
|
The vbroker.orb.dynamicLibs=com.borland.security.hiops.Init property loads the additional HIOPS package, which allows IIOP messages over HTTPS; it is loaded separately.
|
|
•
|
The vbroker.se.exterior.scms=ex-iiop,ex-hiop,ex-ssl,ex-hiops property adds the SCM ex-ssl and ex-hiops into the exterior server engine.
|
The IIOP/SSL and HTTPS listeners can be configured using the SCM properties prefixed with vbroker.se.exterior.scm.ex-hiops and vbroker.se.exterior.scm.ex-ssl. For a comprehensive list of these SCM properties, see “Appendix GateKeeper properties”.
However, without transport identity clients configured with peerAuthenticationMode require and require_and_trust will not connect. Additionally, as an SSL server, if GateKeeper itself does not have a client transport identity, it may not require client transport identities.
In the realm list, among other realms, there needs to be Certificate#CLIENT and/or Certificate#SERVER and/or Certificate#ALL.
|
•
|
Certificate#CLIENT is an SSL identity that is used for outgoing SSL connections,
|
|
•
|
Certificate#SERVER is for incoming SSL connections,
|
|
•
|
Certificate#ALL can be used for both.
|
|
1
|
Certificate#CLIENT is used first.
|
|
2
|
|
3
|
If there is also none set in Certificate#ALL, the outgoing SSL connection will have no identity.
|
Use the peerAuthenticationMode policy as usual. Set the property as follows:
|
•
|
The licensing jars lm.jar, sanct6.jar, and sanctuary.jar are needed only when the applet code creates persistent POAs.
|
|
•
|
When VisiSecure functionality is involved, vbsec.jar is needed in the applet's archive list. The applet parameter that enables it is also needed. Optionally, when HIOPS functionality is involved, it needs to be loaded separately using dynamicLibs as above.
|
A Java webstart application can run without a web browser because it has its own launcher, which can be launched directly from a command shell on UNIX or by double-clicking on Windows. This launcher is the default mime handler for application/x-java-jnlp-file which is associated automatically when installing JDK/JRE on Windows and by any other means on UNIX. Therefore, clicking a link on a web page that results in any http response with that mime will launch the installed Java webstart launcher for processing the content of that reply. The content is actually an XML containing information about where to locate the required jars and other information pertaining to running the application. For example, the required java security permissions.