Silk Meter architecture
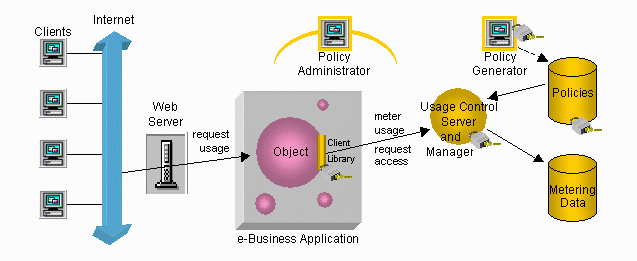
Silk Meter licensing and metering are used in an application as follows:
- A client accesses the web server and requests usage of an application or component that is controlled by Silk Meter.
- The request is passed to the
Usage Control Server, which determines whether or not to grant access to the e-business application, based on information contained in the policy.
Note: If there are multiple valid policies available for the same product, the first policy in the list that satisfies the request is being used. The other policies are ignored in this case. The order in which the policies are validated is the same as in the list of policies on the Policy Administrator.
- The Usage Control Server then authorizes the application to grant access to the requested application or component through the web server. If the Usage Control Server denies access to the application or component, the web server might display an error message.
- Metering data is collected and stored. These statistics are accessible from the Policy Administrator.
Silk Meter is designed based on the following design considerations to ensure flexibility and extensibility:
- Silk Meter uses IIOP as the communication protocol, guaranteeing interoperability with programs built using any CORBA-compliant object request broker. The protocol between Silk Meter clients and servers is fully documented.
- The security module is isolated from the rest of the system, permitting substitution with encryption algorithms other than the default MD5 .
- The policy format is extensible, and the management software is independent of policy content.
- Silk Meter fully conforms to the OMG COS Licensing Specification, which defines the standard for object access control and usage metering, enabling interaction with other CORBA compliant systems.