1.2 The Solution That Sentinel Provides
Sentinel acts as the central nervous system to the enterprise security. It gathers data from across your entire infrastructure—applications, databases, servers, storage, and security devices. It analyzes and correlates the data, and makes the data actionable, either automatically or manually.
Figure 1-2 The Solution That Sentinel Provides
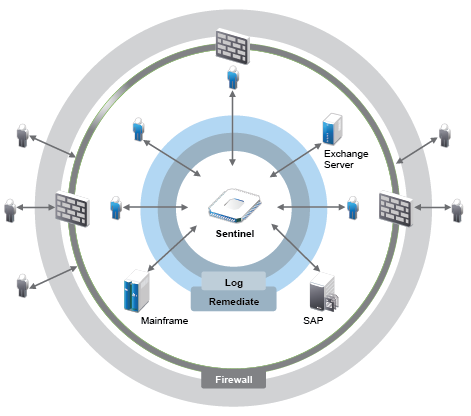
With Sentinel, you know what is happening in your IT environment at any given point, and you have the ability to connect the actions taken on resources to the people taking those actions. This allows you to determine user behavior and effectively monitor activities to prevent malicious activities.
Sentinel achieves this by:
-
Providing a single solution to address IT controls across multiple security standards.
-
Address the gap between what should happen and what is actually happening in your IT environment.
-
Helping you to be compliant to security standards.
-
Providing out-of-the-box compliance monitoring and reporting programs.
Sentinel automates log collection, analysis, and reporting processes to ensure that IT controls are effective in supporting threat detection and audit requirements. Sentinel provides automated monitoring of security events, compliance events, and IT controls. It allows you to take immediate action if there is a security breach or non-compliant event occurring. Sentinel also allows you to gather summary information about your environment, which you can share with your key stakeholders.