Connect to Hosts using the Security Proxy Add-On
The Security Proxy Add-On acts as a proxy for terminal sessions and provides token-based access control, provides-token-based-access-control,-routing-encrypted-network-traffic to and from user workstations.
Note
The Security Proxy Add-on requires the base installation of the Management and Security Server, which provides the Administrative Server. It is not included with the Management and Security Server license. To activate this product, you must purchase a separate license.
Using the Security Proxy Add-On, you can set up the following types of centrally managed secure connections.
| Connect using... | Description |
|---|---|
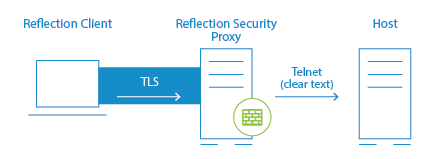
| Client Authorization | When using the default configuration for the Security Proxy, users are authorized using security tokens. Transmitted data between the client and the Security Proxy is encrypted; transmitted data between the Security Proxy and the host is not. The Security Proxy server should be installed behind a corporate firewall when used in this mode. |
| Before you create a connection, review the review the Requirements for connections through the Security Proxy and Getting to the Security Settings. | |
| Then see the instructions for creating and assigning secure sessions in the Management and Security Server Administrator Guide, in the Host Access Management and Security Server Documentation. | |
 | |
| Pass Through | When configured as a Pass Through Proxy, the Security Proxy passes data to the destination host without regard to content (that is, it ignores any TLS handshaking data) and does not provide client/server authentication or encryption. If TLS is used in this mode, the TLS session is created between the client and destination host and encrypted data simply passes through the Security Proxy. |
| You can secure data traffic using TLS between the client and the destination host by enabling TLS user authentication on the destination host. When using a Pass Through proxy, client authorization is not an option. | |
| Before you create a connection, review the Requirements for connections through the Security Proxy and Getting to the Security Settings. For instructions that show how to configure the Security Proxy, see the Management and Security Server Administrator Guide, in the Host Access Management and Security Server Documentation. | |
| Note: If you want to establish an TLS-secured connection between InfoConnect and the destination host using the Security Proxy in Pass Through mode, you may need to unselect Host name must match certificate or, preferably, add the Security Proxy as the Subject Alternate name in the host server certificate. | |
| To create a Desktop session that connects to the Security Proxy, see Create Secure Sessions in the Management and Security Server Administrator Guide. | |
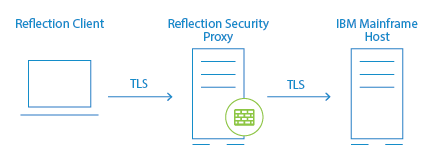
| End-to-End TLS Security | This option, available for 3270 sessions only, combines user authorization with TLS security for the entire connection. Single sign-on capability using the IBM Express Logon Feature is also supported, provided the host supports TLS. See Connect using End-to-End Encryption in 3270 TLS Sessions. |
 | |
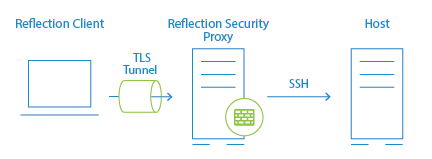
| End-to-End SSH Security | In a standard configuration for a secure InfoConnect session, the connection between the client and security proxy server is encrypted using TLS, but the connection between the security proxy and the host uses unencrypted Telnet. By sending an SSH-encrypted connection through the security proxy tunnel, you can configure a secure InfoConnect session so that the entire communication path is encrypted from the client, through the proxy server, and on to the host. See Connect using End-to-End Encryption in VT SSH Sessions |
 |
Requirements and Other Information for Using the Security Proxy
Requirements for connections through the Security Proxy
Requirements for connections through the Security Proxy include:
-
TLS must be enabled on the hosts to which you want to establish TLS connections. See the documentation included with the hosts for instructions.
-
A centralized management server with the Security Proxy Add-On installed must be available. The Security Proxy must be configured to require client authorization. (It can optionally be configured to require client authentication. For client authentication, you can use a single certificate or two separate client certificates on each server (Security Proxy and destination host).
-
You may need multiple digital certificates to successfully establish the TLS sessions between the client and the Security Proxy, and the client and the destination host.
Getting to the Security Settings
This section includes references to the Management and Security Server Administrator Guide in the Host Access Management and Security Server Documentation.
The Create Secure Sessions procedure referenced in this guide does not include product-specific information for setting up TLS connections.
For IBM terminal sessions, when you create a session in InfoConnect Desktop, use the following steps to go to these security settings:
Getting to security settings for IBM terminals
-
Enter the Host name and Port.
-
Select Configure additional settings to open the Settings window and then choose Set Up Connection Security.
-
In the Configure Advanced Connection Settings dialog box, click Security Settings.
For ALC, UTS, or T27 terminals, when you create a session in InfoConnect Desktop, use the following steps to configure these settings
Getting to security settings for ALC, UTS, or T27 terminals
-
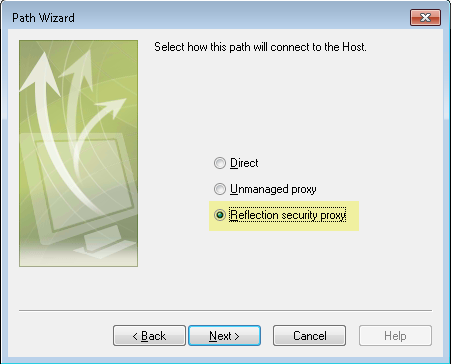
In the Create New Document dialog box, click Create Path to start the Path Wizard. Respond to the prompts for yourconnection type until you see the following dialog box. (These options appear only when you are running in WebStation mode.)
-
Select Reflection security proxy and click Next. You can use the next dialog box to configure your connection to the host through the proxy.
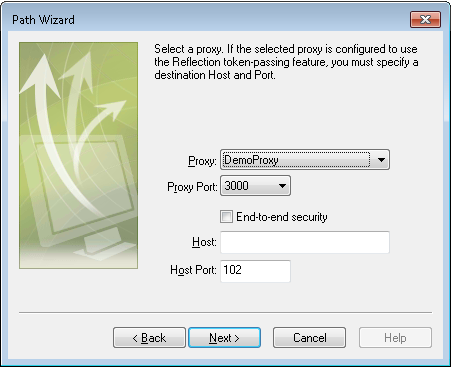
-
Click Next and continue through the wizard to complete the configuration. When you click Finish, the session opens in InfoConnect.
About Certificates
| Server Certificates | Destination TLS hosts and Security Proxy servers typically have server certificates already installed. Each of these server certificates must be trusted by the client. The client will trust a server certificate if: |
| -It is signed by the certificate authority that is trusted by the client, or | |
| - It is self-signed and imported into the trusted root certificate store where InfoConnect can find it. | |
| To use a single server certificate for both the destination host and the Security Proxy, do one of the following: | |
| - In the InfoConnect session, unselect the Verify Server Identity check box on the Connection Editor dialog box. | |
| - (Recommended) Create a certificate that uses the destination host address for the Subject Common Name and the Security Proxy address for the Subject Alternative Name. | |
| Client certificates | Certificates used for client authentication must be signed by a certificate authority that is trusted by both the Security Proxy and the destination host's TLS server. |
| Express Logon also requires that the client certificate used to authenticate on the TN3270 server be registered with RACF. (For details, see the documentation that came with the 3270 server.) | |
| For more details on configuring TLS and creating certificates on the host, see Technical Note 7022182. |
Connect using End-to-End Encryption in 3270 TLS Sessions
End-to-end encryption tunnels a direct TLS connection to the host, while still connecting through the Security Proxy Server. These connections require two certificates and TLS handshakes — one for the client/proxy server connection and another for the client/host connection. Without end-to-end encryption, only data between the client and proxy server is encrypted.
Before you create a connection, review the Requirements for connections through the Security Proxy and Getting to the Security Settings.
To configure a session with end-to-end encryption, see the instructions for creating secure sessions in the Management and Security Server Administrator Guide in the Host Access Management and Security Server Documentation.
Note
You can modify the level of security by adjusting the TLS protocol version and encryption key-strength setting. Click PKI Manager to add the Certificate Revocation List (CRL) and Online Certificate Status protocols (OCSP) to certificate validation.
Connect using End-to-End Encryption in VT SSH Sessions
You can configure an InfoConnect Desktop session to send an SSH-encrypted connection through the Security Proxy Server.

In a standard Administrative Console configuration for a secure InfoConnect session, the connection between the client and security proxy server is encrypted using TLS, but the connection between the security proxy and the host uses unencrypted Telnet. By sending an SSH-encrypted connection through the security proxy tunnel, you can configure a secure InfoConnect session so that the entire communication path is encrypted from the client, through the proxy server, and on to the host.This feature has the following advantages:
-
Encryption is used for the entire connection.
-
The IP addresses and names of your secure hosts are not exposed outside of the internal network.
-
Only clients with a valid authorization token can launch a secure session.
-
The authorization token contains connection information. This enables the security proxy to send all secure host connections through a single port, eliminating the need to open multiple firewall ports.
-
All settings required for a connection (such as the trusted certificate, the personal certificate, user keys, and host keys) reside on the Administrative Console and are downloaded to users' workstations when they start sessions.
You can set up this configuration using the InfoConnect VT Terminal type (used for UNIX and OpenVMS sessions).
Prerequisites
To make these SSH connections through the Security Proxy, you must have the following:
-
The host must have an SSH server installed.
-
InfoConnect Desktop v16 or greater must be installed locally on your workstation.
-
You must have access to the centralized management server Security Proxy and Administrative Console.
-
Host Sessions must be opened from the Administrative Console or the Links List page.
-
Sessions must be configured from the Administrative Console in the centralized management server.
-
The Security Proxy must be running with Client authorization enabled.
Note
Management and Security Server is not licensed for connections from InfoConnect Desktop clients. You must have a Management and Security Server activation file installed to configure InfoConnect Desktop sessions.
To connect your VT session SSH connection through the Security Proxy Add-On
-
Follow the instructions for creating a new session in the Management and Security Server Administrator Guide in the Host Access Management and Security Server Documentation* and create a new VT session.
-
When you configure the session, select Secure Shell for the connection type.
-
Enter the host name and user name (optional; users are otherwise prompted when they connect). Then select Configure additional settings and click OK to open the Settings dialog box.
-
Under Host Connection, click Set up Connection Security.
-
In the Reflection Secure Shell Settings dialog box, on the Reflection Security Proxy tab, select Use Reflection Security Proxy, and then choose a Security proxy and a Proxy port.
Note
The Destination host values you entered in step 6 should be entered automatically here. If you don't see them, select the Security proxy name from the drop-down list to populate these fields.
-
Configure SSH connection settings such as the trusted certificate, the personal certificate, user keys, and host keys as required for your connection.
-
Click OK to close the open dialog boxes and initiate the connection. Select Always to import the host key for these sessions.
Note
If you do not want to include the user name in the configuration, cancel the connection. If you cancel, you will be unable to import the host key for the session.
-
Save the session. When prompted, choose to send the settings for this session to the Administrative Console, and then exit the InfoConnect workspace.
All the files required for your configuration are uploaded to the Administrative Console. When a user launches the session, these files are downloaded to their workstation so that InfoConnect has access to all configuration data required to establish a connection.
notes
All non-default SSH settings required to establish a connection are saved in three files:
-
The
sessionname.rsshfile contains the public key (if public key authorization is used), the host key (if a host key is accepted while in administrative mode), and the settings normally stored in both thepki_configfile and theconfigfile. It also includes all TLS settings such as the TLS version, cipher suites, and applicable proxy data. -
The
sessionname.psfile stores any personal certificates included for the connection. -
The
sessionname.tsfile includes any trust certificates.
When you send settings for the session to the Administrative Console, these files are uploaded along with the session document file.
-