12.5 Configuring the OpenText Directory Services Application Collector
The OpenText Directory Services application collector collects accounts, permissions, and hybrid permissions. The REST OTDS Permission template allows you to collect hierarchical permissions. While configuring the service parameters in the template, enable the option 'Populate Nested Permission Assignments'. However, when you enable this option, OpenText Identity Governance prevents you from fulfilling change requests to remove permissions from accounts and permission assignments. Additionally, the template allows you to select various permission types from the Collect OTDS Permissions view, including groups, roles, and access roles and in any combination.
12.5.1 Configuring the OpenText Directory Services Hybrid Permission Collector
By default the hybrid permission collector template script is configured to collect permissions from xECM and synchronize it to OpenText Directory Services user attributes, supplemental markings, and security clearance. To collect these permissions you must generate a CSV file from xECM first and use the file as the input value. After collection, these permissions are mapped as user profile attributes in OpenText Directory Services. Any changes you make to these attributes in OpenText Directory Services are synchronized to xECM.
NOTE:Before configuring the REST OTDS Hybrid Permission template, you must first generate a CSV file with the security clearance and supplemental marking permission from xECM.
To generate the CSV file:
-
From any client application that is used for API testing, for example, Postman, send a ‘Get’ request for security clearance using the following request URL:
https://{{host}}/cs/cs/api/v1/securityclearances
Replace {{host}}with the xECM hostname.
For more information on how to authenticate users and get security clearance and supplemental marking, refer to the following links:
-
When you have the data, copy the JSON result and convert it to a CSV file.
-
Review the CSV file output and make any necessary adjustments. This may involve aligning the column headings with those specified in the Row Pattern field for Hybrid Permission > Collect Permission view or consolidating relevant data under a single column.
The following shows a sample CSV file after making changes:
Figure 12-1 Sample CSV File
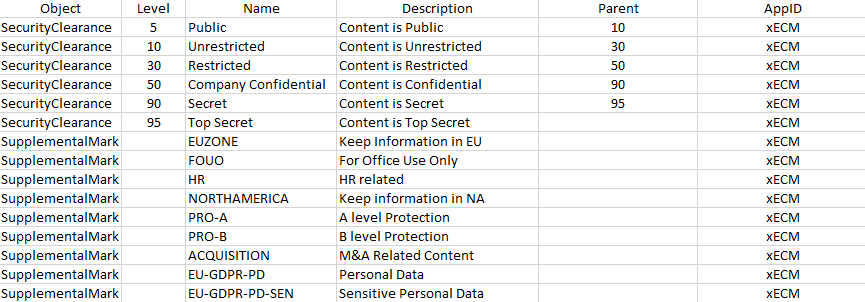
-
Save the CSV file on your local drive, then copy it to a folder on the OpenText Identity Governance server.
-
Log in to OpenText Identity Governance, then navigate to Data Sources > Applications.
-
Create an application source or click the application name from the Application Sources page.
-
Select the OTDS Hybrid permission template.
-
Configure service parameters as required.
-
Expand the Collect Permission view and in the Permission File Name field specify the full path to the CSV file.
-
Specify details as necessary.
-
Expand the Collect Holder to Permission Mapping view and select Collect this data? to collect holders from OpenText Directory Services.
-
Specify details as necessary and save.
In the Collect Holder to Permission Mapping view, the User Profile Permission Attribute and the Holder Permission(s) fields should have corresponding attribute values. The default values in the template are otSupplementalMarking and otSecurityClearanceLevel. However, you can modify or change these values. For example, if you modify the User Profile Permission Attribute value from oTSupplementalMarking to SupplementalMarking, you must update the Holder Permission(s) field as well. Additionally, update the holder permission ECMA script and change all instances of oTSupplementalMarking to SupplementalMarking as given in this sample script.
/* start of generated script to extract variables from inputValue */
/* NOTE: any code inserted within this block will get overridden if inputs are regenerated */
var vals={};
// inputValue is string, we need to parse it to convert it into a javascript object
var inputValueParsed = JSON.parse(inputValue);
vals.oTSecurityClearanceLevel = inputValueParsed.oTSecurityClearanceLevel ? inputValueParsed.oTSecurityClearanceLevel : '';
vals.SupplementalMarking = inputValueParsed.SupplementalMarking ? inputValueParsed.SupplementalMarking : '';
var holders = [];
var logger = org.slf4j.LoggerFactory.getLogger("debug");
if ((vals.oTSecurityClearanceLevel !== undefined) && (vals.oTSecurityClearanceLevel !== ''))
{
holders = JSON.parse(vals.oTSecurityClearanceLevel);
}
if ((vals.SupplementalMarking !== undefined) && (vals.SupplementalMarking !== ''))
{
//we need to split value, since it is a multivalue attribute
holders = holders.concat(JSON.parse(vals.SupplementalMarking));
//logger.info("holders are: " + JSON.stringify(holders));
//logger.info("**********");
}
outputValue = JSON.stringify(holders);
// enable debug by uncommenting lines below
//logger.info("**********");
//logger.info("inputValue is: " + JSON.stringify(inputValue));
//logger.info("extracted vals are " + JSON.stringify(vals));
//logger.info("**********");
/* NOTE: any code inserted within this block will get overridden if inputs are regenerated */
/* end of generated script */