Adding or Removing Enforced Filters
About:
Enforced filters define which events a user group can view. By default, all new groups cannot view any events. If you view the Events tab on a new group's ACL Editor, the filter is shown as
/All Filters/Arcsight System/Core/No Events
After you add filters to this tab, these filters become the user group's enforced filters that are enforced at run time. The filters you add can be ArcSight-provided filters or filters you created, based on individual groups’ requirements.
By default, members of the administrators group can view all events, as indicated by the Administrators group's enforced filter: /All Filters/ArcSight System/Core/All Events.
Prerequisite:
Event filters must be available before you can add them to the Events tab of the ACL Editor for the user group. For more information about filters in general, see Filtering Events. For more information about events, see Events and Event Categorization.
Important notes about enforced filters:
-
ESM evaluates the enforced filters with an OR operator. Evaluating events against filters using OR becomes relevant especially if different filters are applied to a hierarchy of user groups, or if a user is linked to multiple user groups. You should keep these relationships in mind, to determine the ultimate set of events that a user sees.
-
An event only needs to match one of the filters, for that event to be accessible. This means if the ACL Editor's Events tab has multiple filters, not all filters are necessarily evaluated after the first match is found. You can consider combining multiple filters into one filter using the
MatchesFilteroperator, then add that filter to the ACL Editor's Events tab for the user group, to ensure that all filters are evaluated. -
Active channels, when launched, use the enforced filters associated with the user who launched the channels.
-
Reports and query viewers use the enforced filters to return and display data.
-
Trends and data monitors use the enforced filters of the user who created these resources.
-
Users have the ability to annotate events that match any one of their enforced filters.
Where: Navigator > Resources > Users > user group
-
Right-click the user group and select Edit Access Control.

-
In the ACL Editor, select the Events tab.
The default enforced filter is listed on the tab.
Caution: Be sure to set permissions on resources and permissions on events appropriately for user groups.
Preventing users from viewing groups of resources does not necessarily prevent those same users from viewing event data on those resources.
Users with permissions to view certain events (determined by event filters as described here), can view all event fields for those particular events (in reports, query viewers, and so forth) even if they do not have permissions on some resources reflected in the event data.
For example, a user with no read permissions on an asset could still have permissions to view event data related to the asset, and thereby have access to the data contained in the event fields (such as server name, IP address) in the context of that event.
As a best practice, keep the above in mind when granting permissions on events. Otherwise, you might give some users a view into resource information through event data that you did not intend for them to see.
-
Add or remove user group permissions to view events as follows.
-
To add permissions to view events captured by a filter not shown in the current list, click Add.

On the Filters Selector dialog, choose the filters for events that the user group can view and click OK. For example:
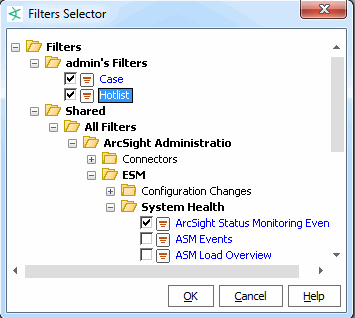
The list of enforced filters for the user group is updated to include the ones you added:

The default
/No Eventsfilter is disabled as you add enforced filters to the Events tab. -
To remove enforced filters (event filters for this user group), select a filter in the list and click Delete. The Delete button is at the bottom of the Events tab. You cannot delete the default
/No Eventsfilter. -
Click OK on the User Group ACL Editor to save changes to Operations permissions.