SmartConnector-
These methods enable batch loading and automatic ongoing maintenance. Both methods offer limited distinctions.
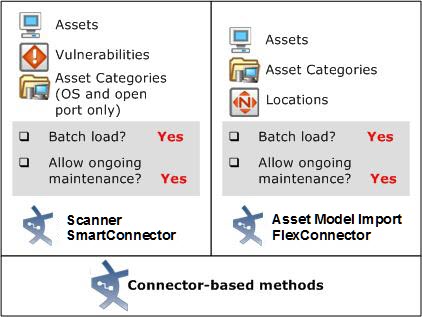
Using the Asset Model Import FlexConnector
The system offers an Asset Model Import FlexConnector that reads Asset, Location, and Asset Category information from a CSV file, which it then sends to the Manager. New assets are added and existing assets in the model are updated .
This method does not create asset ranges, and assumes that Zones, Networks, customers, and locations are already created.
For more about the Asset Import FlexConnector, see the Developer's Guide for Asset Model Import FlexConnector.
Automatically From a Vulnerability Scanner Report
Set up a scanner SmartConnector (such as FoundStone, ISS Internet Scanner, or Nessus) to use the output of a vulnerability scan to convert device information into Assets along with Vulnerability information, and basic Asset Categories, such as operating system and open ports. The scanner connector that corresponds with your vulnerability scanning product sets up a directory that to regularly scan for updated reports. It then converts the scanner report output into internal scanner meta-events, which the Manager converts into Assets, open port and OS Asset Categories, and Vulnerabilities. For more about the architecture of how this works, see the topic “How Vulnerability Scans Populate and Update the Network Model” in ESM 101.
You can also set the scanner SmartConnector to save network model data as a CSV file, which you can then upload into the Manager using the Files resource during your initial network model setup.
Data derived from vulnerability scanner reports does not create asset ranges, and assumes that Zones and Networks are already created. Once scanner data is imported, you can add Customer and Location distinctions to the assets individually. For details about how the system adds updated vulnerability information arriving from a new scanner report, see Reporting on Output from Vulnerability Scanners.
This method is appropriate for updating and maintaining your network model. Subsequent scans update the basic Asset, Asset Category, and Vulnerability information without overwriting the other network modeling settings you add individually.
For more information about the scanner SmartConnector for your vulnerability scanning product, see the SmartConnector Configuration Guide that corresponds with your vulnerability scanning equipment.