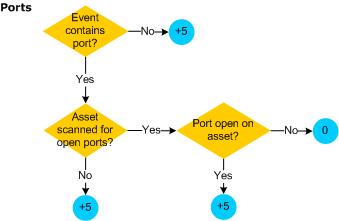
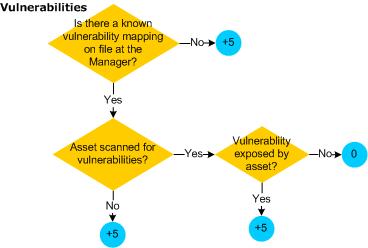
Priority Calculations and Ratings
The priority formula, formerly referred to as the Threat Level Formula, is a series of five criteria that each event is evaluated against to determine its relative importance, or urgency, to your network. This topic describes the calculations used to determine an event’s priority rating (Priority Rating).
Priority evaluation is applied to all the events that the Manager receives from SmartConnectors. The event's priority lets security operations personnel know whether this is an event that warrants further notice. The priority value assigned to an event is essentially the severity the event was assigned by the original reporting SmartConnector, as modified by the weighting schemes model confidence, relevance, severity, and asset criticality. Each of these four criteria described in the table below contributes a numeric value to the priority formula.
Each of the four factors evaluates to a value in the range of 0 to 10, where 0 is low and 10 is high. The values have a specific positive or negative influence (weight) on the original SmartConnector severity value. See Prioritization Fields for definitions of these factors.
The priority formula consists of 4 factors that combine to generate an overall priority rating. Each of the criteria described in Factors Contributing to Priority Evaluations contributes a numeric value to the priority formula, which calculates the overall importance, or urgency, of an individual event.
All values fall in the range between 0 and 10. A high priority factor generally indicates an event with a higher risk factor. Not every high priority event is necessarily a threat, however. For example, if a critical e-mail server fails, the priority of the events reporting it may be very high, although it does not necessarily represent a threat to your network.
The following table describes the factors considered in the ESM priority evaluation. If you require help in changing the values, enter a case with Software Support. The maximum score for each factor is 10: if the value of qualifying conditions for that factor totals more than 10, the amount over 10 is not considered.
Note: You can view an event’s priority information by right-clicking the event on the grid and selecting Debug Event Priority. The window displays information on how the priority score was determined for the selected event. The values described in the following table come from actual values stored for the events. The debugging information, however, is real time without history.
If you set the severity through a rule action, the debug event priority shows this value; however, the debug information does not cover this particular rule action. This is because the values described in the information are based on actual values stored for the event. Event conditions defined in the rule are based on live evaluation of the current state of the system.
You can use asset aging to reduce asset confidence level as the time since the last scan increases. For information on configuring that, refer to the ESM Administrator’s Guide, “Configuration” section, topic on “Asset Aging.”
The priority calculation formulas are made up of basic elements organized by operators called Sum and Difference. These elements are based on simple condition expressions.
More information: