Brokering Flow
Figure 5-24 Brokering Group Configuration
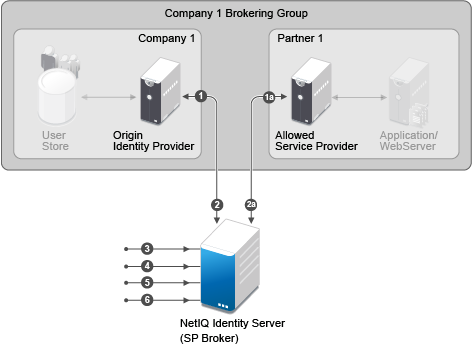
The Brokering Group configuration image provides information about how the Identity Provider Brokering group is configured with Service Provider Brokering Group.
-
Identify the Company and Partners’ Identity Providers.
-
Company 1 Brokering Group is configured with their Identity Server.
-
1a is the partner of Company 1 Brokering Group configured with Service Provider Brokering Group that is Novell Identity Server.
-
-
The federation is established between the company and partners’ Identity Provider and the Service Provider Brokering Group that is Novell Identity Server.
-
Company 1 Brokering Group is configured with their Service Provider Brokering Group that is Novell Identity Server.
-
2a is the partner of Company 1 Brokering Group configured with Service Provider Brokering Group that is Novell Identity Server.
-
-
Create a new brokering group.
The Service Provider manages the brokering group based on roles.
-
Roles based on Identity Provider authentication.
-
Roles based on Service Provider brokering authentication.
-
Assign the Identity Providers and Service Providers.
-
-
Using Liberty, SAML 1.1, and SAML 2.0 protocols define policies and do the intersite transfer around the Service Provider Brokering feature.
-
Using the Brokering Service construct URLs.
-
Construct URL for each Identity Provider and Service Provider pair.
Figure 5-25 Brokering Group Flow
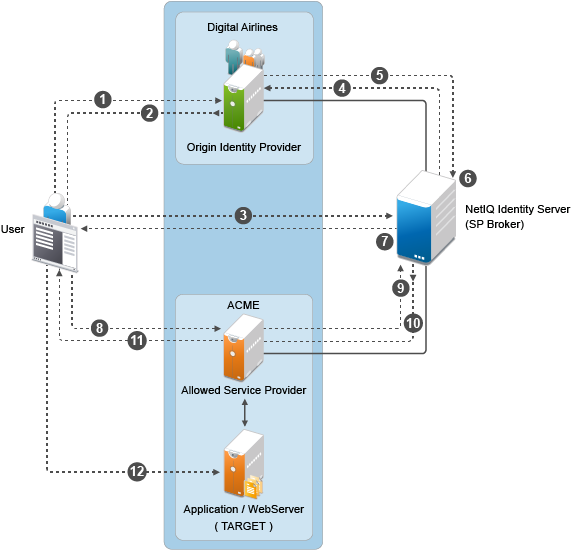
Identity Server is being shared to provide Service Provider brokering to a set of logical customers. Company 1 has one partner. All the trusted providers are configured at one broker Identity Server
-
User clicks on URL1. The browser send a request to https://idp.customer1.com/nidp/saml2/idpsend?PID=https://brokeridp.verizon.com/nidp/saml2/metadata&ID=partner1-sp-id&TARGET=https://www.partnerapp.partner1.com
-
Customer Identity Provider prompts the user for credentials if not already logged in. User logs in at Customer-1-IDP. The Identity Provider then performs an inter site transfer to Identity Provider Broker. This involves creating an sp-assertion-consumer-URL request and redirects the user to the following URL which eventually lands at Broker Identity Providers’ Assertion Consumer URL https://brokeridp.abc.com/nidp/saml2/sp_assertion_consumer
-
POST contents will include SAML Artifact = <artifact> and RelayState=https://brokeridp.abc.com/nidp/saml2/?idpsend=partner1-sp-id&TARGET=https://www.partnerapp.partner1.com
-
The service provider assertion consumer URL processing includes a hook to enforce broker rules.
-
From the Artifact, it finds the trusted provider that it is receiving the artifact from origin trusted provider.
-
If the RelayState contains IDPsend, then it finds the target trusted provider from the RelayState and also finds the target.
-
Using origin trusted provider, the group to which this brokering request belongs is found and a search is made for the policies representing origin trusted provider, target trusted provider and brokering service provider.
-
At this time, only role is unknown. A decision can be taken if the brokering is allowed between origin trusted provider and target tested provider for a particular target or not. If it is allowed then it is proceeded to the next step of artifact resolution.
-
after this request needs further processing of role enforcement which will be known only after an assertion is received from customer identity provider, a flag is set on the Novell identity provider session object. This flag (Broker_role_enforcement) is checked during assertion processing.
-
-
Artifact resolution happens at customer identity server.
-
Artifact resolution response is sent to the broker identity server which contains the assertion.
-
A new hook is made in the assertion processing.
-
If Broker_role_enforcement flag is set on the session, then Roles are identified for this userBroker rules are again enforced for the Roles.
-
If the brokering is not allowed for the Role an error message is displayed at the browser. Otherwise the browser is redirected back to the Broker Identity Server (to itself) with the following URL https://brokeridp.verizon.com/nidp/saml2/?idpsend=partner1-sp-id&TARGET=https://www.partnerapp.partner1.com
-
Intersite transfer is now made to the DSP with the following URL https://partner.idp.com/nidp/saml2/spassertion_consumer
-
The POST message contains SAML Artifact and RelayState (which contains the target URL).
-
-
The partner service provider verifies the artifact over SOAP back channel with broker identity servers.
-
Broker Identity Servers resolves the artifact and sends the assertion.
-
Partner Service Providers redirects the browser to the target URL (https://www.partnerapp.partner1.com). It sets its cookie on the browser during the redirection. At this time the user has a valid authenticated session on Partner Service Provider.
-
The Partnerapp.partner1.com validates the session and provides access to the user.