5.8.6 Configuring Behavioral Analytics
You can integrate Access Manager with Micro Focus Interset to leverage its User and Entity Behavioral Analytics (UEBA) capability. Using the organization's data, Interset establishes the normal behavior for the organizational entities. Interset then, using advanced analytics and machine learning, identifies the anomalous behaviors that constitute potential risks. For example, compromised accounts, insider threats, or other cyber threats.
How It Works
Access Manager Risk Service periodically fetches risk scores for all entities from Interset and keeps the latest scores in the cache. While configuring Interset, you need to configure it to receive data from various applications used in your organization. Interset analyzes the behavior of entities and users using this data.
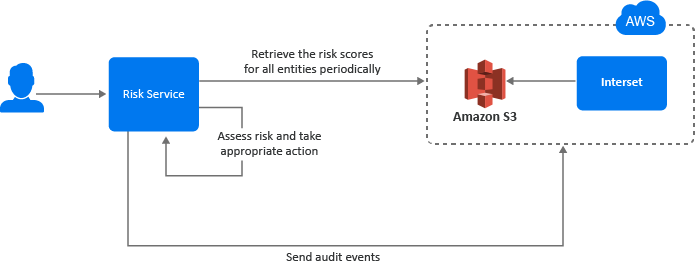
The following diagram illustrates how this integration works:
-
A user tries to log in to a protected resource.
-
Risk Service checks the behavioral risk score for this user in the risk score cache.
Risk Service keeps retrieving the latest behavioral risk scores for all entities at a regular interval and updates the cache.
-
Risk Service assesses the score and takes appropriate action.
-
Access Manager sends the audit events to Interset for the auditing purpose.
For more information about Interset UEBA, see User and Entity Behavioral Analytics.
For step-by-step details for integrating Access Manager with Interset, see Enabling Behavioral Analytics Using Micro Focus Interset.
Prerequisites for Configuring Interset Details
-
An ArcSight Intelligence (formerly Interset) account on AWS is available. For more information, see ArcSight Intelligence.
-
AWS S3 Interest URL from where you want to get the data
-
AWS region name
-
AWS access key and access secret required to access AWS S3 Interset URL
-
(Optional) Interset syslog connector URL
-
(Optional) Syslog connector certificate
NOTE:Interset syslog connector URL and syslog connector certificate are required only when you want to send Access Manager audit events to Interset.
Configuring Interset Details
-
Click Policies > Risk-based Policies > Behavioral Analytics.
-
Select Enable Integration with Interset.
-
Specify the following details under Read Behavioral Analytics Data from Interset:
Field
Description
Interset Data URL
The AWS S3 bucket URL from where you want to get the Interset data.
AWS Region
The AWS region where Interset is deployed.
Access Key ID
The AWS access key ID to access the Interset URL.
Secret Access Key
The AWS secret access key to access the Interset URL.
Update every
The interval for syncing the data from Interset. The recommended value is 360 minutes (sync four times a day).
NOTE:To prevent disruption of service, ensure that Access Key ID and Secret Access Key specified here are up to date when these are rotated as per AWS guidelines.
-
(Optional) If you want to send Access Manager audit events to Interset, specify the following details under Send Events to Interset:
Field
Description
Enable
Select this option to enable sending audit events to Interset. See Audit Events Supported for Behavioral Analytics.
Interset Syslog Connector URL
Specify the URL of the AWS Interset syslog connector in the domain:port format.
Identity Server and Access Gateway send audit events to this syslog server.
Syslog Connector Certificate
Upload the syslog connector certificate.
This certificate validates and secures the connection to the syslog connector.
-
Click OK.
After you complete the Interset configuration, an external parameter rule is configured using the appropriate Interset-specific values. The rule is named as BehavioralAnalyticsRule.
-
Go to Policies > Risk-based Policies > Rules. Click BehavioralAnalyticsRule, verify, and edit it if required.
This rule is configured with the default behavior to consider any user with Interset score less than 50 as a low-risk user. You can modify this rule to change how the score from Interset is interpreted. You can modify Negate Result and the value for the score (the default value for the score condition is < 50). Do not modify any other field.
Field
Details
Negate Result
Select this option to reverse the result of the rule evaluation.
Parameters Set 1
Modify the value for the score parameter, if required.
-
Add BehavioralAnalyticsRule to a risk policy. Assign the risk score and the levels to configure appropriate weightage to the behavioral risk score.
-
Create an authentication method and a contract for the authentication class associated with the risk policy to use the behavioral analytics capability.
See Configuring a Method for an Authentication Class and Configuring a Contract for an Authentication Class.