5.8.10 Risk-Based Authentication: Sample Configuration
This section explains the use cases and their configuration steps demonstrated in the Try Now option on the Risk Configuration > Overview interface.
Let us assume a company named Company1 wants to control access to its resources. There are two users. One is a permanent employee of Company1 and another is a trainee at Company1. This configuration will refer the regular employee as Employee and the trainee as Trainee.
Company1 wants to achieve the following actions:
-
Scenario 1:Trainee or Employee accesses a resource by using the internal network: Allow access.
-
Scenario 2:Trainee accesses the resource by using the external network: Deny access.
-
Scenario 3: Risk associated with accessing the resource from an external network can depend various conditions. The following are the conditions with equal weightage:
-
Employee’s request contains a cookie from the Intranet site or has a header from the Payroll site, indicating that Employee was successfully logged into these resources earlier.
-
Employee is logging in during normal work hours that is 9 am to 5 pm
All conditions are evaluated. The risk decreases as the number of conditions met increases. The action performed depends on the risk score and associated risk level.
-
The following diagram illustrates the rule execution logic of the demo risk policy:
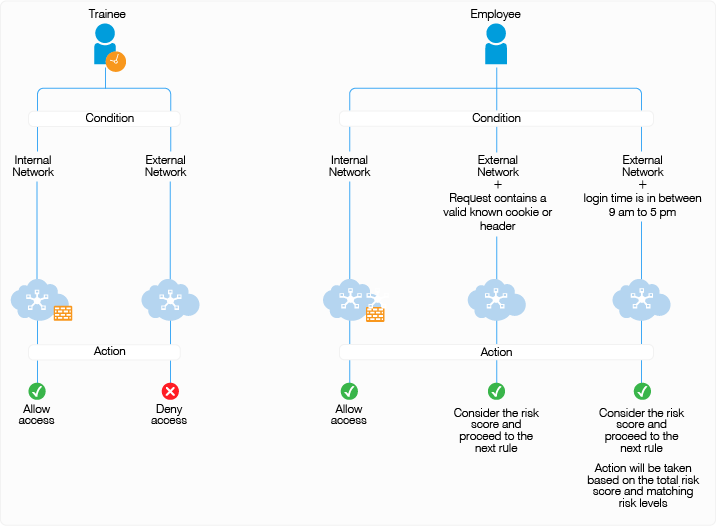
You can configure rules for these scenarios and arrange the rules in the order of priority on the UI. The rules are executed based on the priority from top to bottom. You can drag and drop rules on the UI to change their priority.
In this sample, the following five rules are created and executed in the same sequence:
|
Sequence of Execution |
Rule Name |
Action |
|---|---|---|
|
1 |
DemoRule_InternalNetwork |
If Trainee or Employee is in the internal network, then allow access and exit the policy. If not, add risk score of 20 and proceed to the next rule. |
|
2 |
DemoRule_TraineeUser |
If Trainee is accessing from an external network, deny access and exit the policy. If Employee is accessing from an external network, add risk score of 20 and proceed to the next rule. |
|
3 |
DemoRule_Combo |
If Employee is accessing with a cookie from the payroll site or HTTP Header value contains loggedIn, proceed to the next rule with the total risk score accumulated due to the failure of the above three rules. For example, assume the risk score for each rule is 20. If the condition for this rule is met, then proceed to next rule with a risk score 60. If the condition for this rule is not met, then proceed to next rule with a risk score of 80. NOTE:To use this rule, you must set cookies or headers per domain with a path of /, so that Identity Server can receive them. |
|
4 |
DemoRule_TimeOfLogin |
If Employee is logging in using an external network and time is in between 9 AM to 5 PM, proceed to the next rule. The risk score will depend on whether the condition of the DemoRule_Combo was met. If the conditions of both DemoRule_Combo and DemoRule_TimeOfLogin rules fail, the total risk score will be 100 and access will be denied. |
The following steps have been performed to configure the demo risk policy:
-
Go to Policies > Risk-based Policies > Risk Policy.
-
Click the Create Risk Policy icon.
-
Under Add Risk Policy, specify the following details:
Risk Policy Name: Specify Demo_RiskPolicy.
Policy Description: Specify the purpose of this policy.
Assign Policy To: Select Identity Server cluster and then configure an authentication class.
-
Select Create Risk-based Auth Class.
-
Specify Class Name as Demo_RBAAuthClass.
-
Click Save.
-
-
Create the following rules:
Under Policy Rules, click Create Rule and specify the following values:
-
DemoRule_InternalNetwork
-
Rule Name: DemoRule_InternalNetwork
-
Rule Definitions: IP Address Rule
-
Specify the IP address range as 121.1.1.1 - 121.121.255.255 and click OK
-
If rule condition is met, then: Allow Access and Exit Policy
-
If rule condition is not met, add risk score: 25
-
Click OK.
-
-
DemoRule_TraineeUser
-
Rule Name: DemoRule_TraineeUser
-
Rule Definitions: User Profile
-
Select EmployeeType, Equals, and then specify Trainee. Click OK.
-
If rule condition is met, then: Deny Access and Exit Policy
-
If rule condition is not met, add risk score: 25
-
Click OK.
-
-
DemoRule_Combo
-
Rule Name: DemoRule_Combo
-
Rule Definitions:
Rule 1: Cookie Rule
Cookie Name: IntranetCookie
Cookie Value: is test 12
Rule 2: HTTP Header Rule
HTTP Header Name: PayrollAccessHeader
HTTP Header Value: Contains loggedIn
-
Combination Rule Definition: In Condition Group, click Assign Rules and then select both rules. Select OR in Group Operator
-
If rule condition is met, then: Proceed to Next Rule
-
If rule condition is not met, add risk score: 25
-
Click OK.
-
-
DemoRule_TimeOfLogin
-
Rule Name: DemoRule_TimeOfLogin
-
Rule Definitions: User Time of Login Rule
User time of login: is
Day: Monday to Friday
Time: 9 AM to 5 PM
-
Click OK
-
If rule condition is met, then: Proceed to Next Rule.
-
If rule condition is not met, add risk score: 25
-
Click OK
-
-
-
Under Risk Levels, click Actions > Add Risk Level and create the following risk levels:
-
Low
Field
Value
Risk Score
Less than 35
Risk Level
Low
Action
Allow Access
-
Medium
Field
Value
Risk Score
Between 35 and 75
Risk Level
Medium
Action
Additional Authentication > Trust levels
-
High
Field
Value
Risk Score
Greater than 75
Risk Level
High
Action
Deny Access
-
-
Click OK.
-
Create an authentication method. See Configuring a Method for an Authentication Class.
-
Create a contract. See Configuring a Contract for an Authentication Class.